Assessment Dashboard - Cyber Security Risk Management (Excel XLSX)
BUY WITH CONFIDENCE
BENEFITS OF DOCUMENT
- Diagnose Cyber Security Risk Management projects, initiatives, organizations, businesses and processes using accepted diagnostic standards and practices.
- Implement evidence-based best practice strategies aligned with overall goals.
- Integrate recent advances in Cyber Security Risk Management and process design strategies into practice according to best practice guidelines.
DESCRIPTION
This product (Assessment Dashboard - Cyber Security Risk Management) is an Excel template (XLSX) with a supplemental Zip archive file document, which you can download immediately upon purchase.
National Institute of Standards and Technology (NIST) U.S. Department of Commerce Cyber Security Framework Aligned.
Governments, sectors, and organizations around the world are increasingly recognizing the NIST Cyber Security Framework (CSF) as a recommended cyber security baseline to help improve the cyber security risk management and resilience of their systems.
This Self Assessment provides conformance to the NIST CSF risk management practices, allowing you to properly protect your data.
The Cyber Security Risk Management Self-Assessment will make you a Cyber Security Risk Management domain expert by:
1. Reducing the effort in the Cyber Security Risk Management work to be done to get problems solved
2. Ensuring that plans of action include every Cyber Security Risk Management task and that every Cyber Security Risk Management outcome is in place
3. Saving time investigating strategic and tactical options and ensuring Cyber Security Risk Management opportunity costs are low
4. Delivering tailored Cyber Security Risk Management advise instantly with structured going-forward plans.
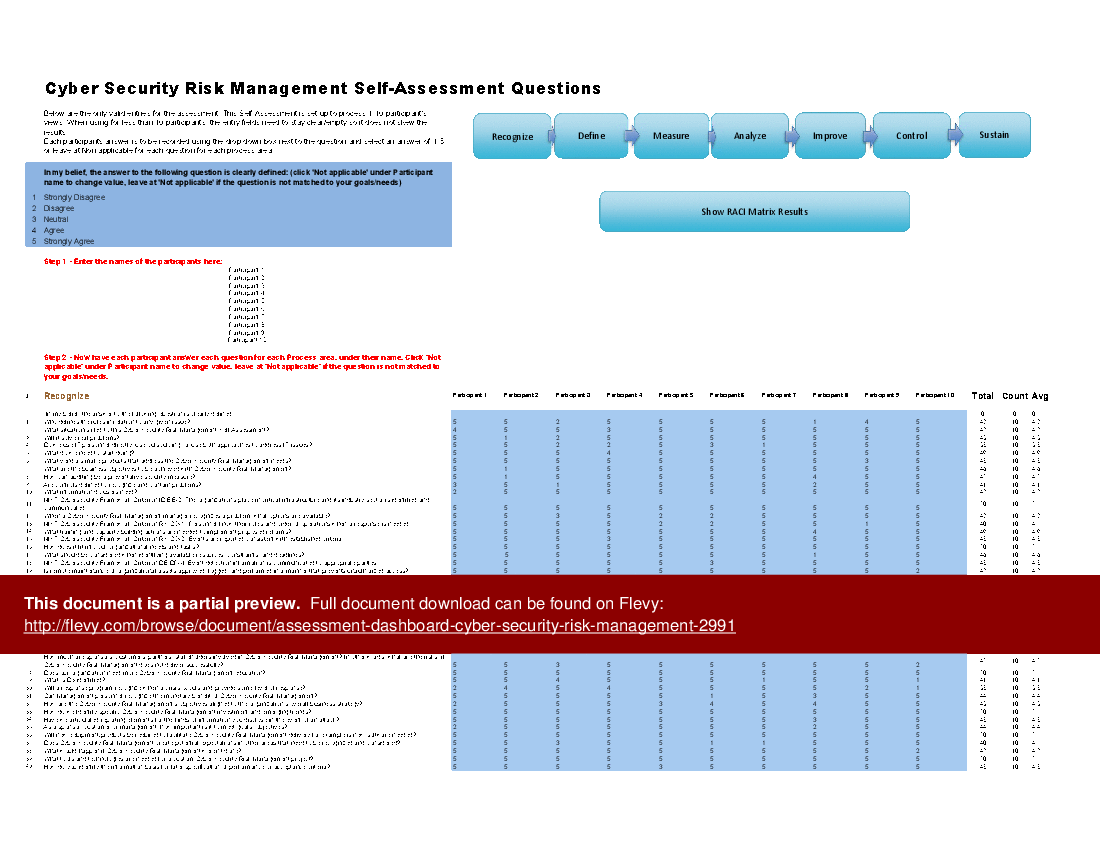
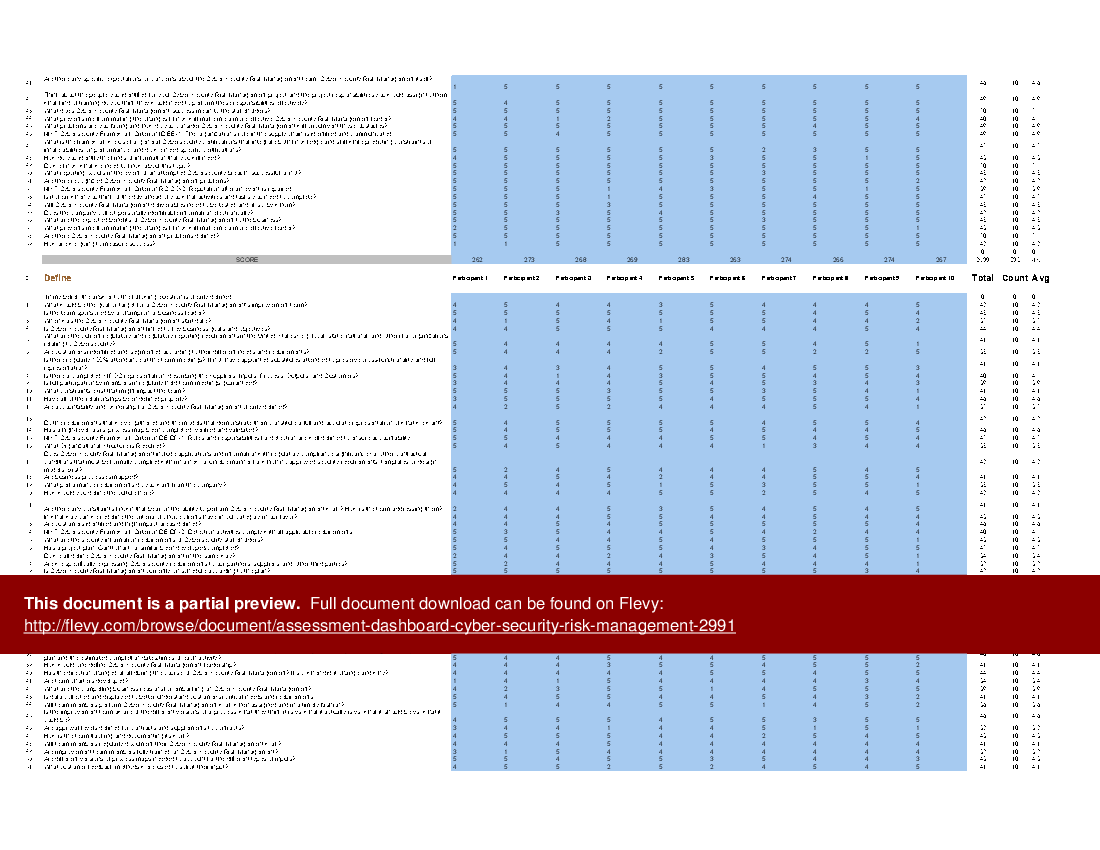
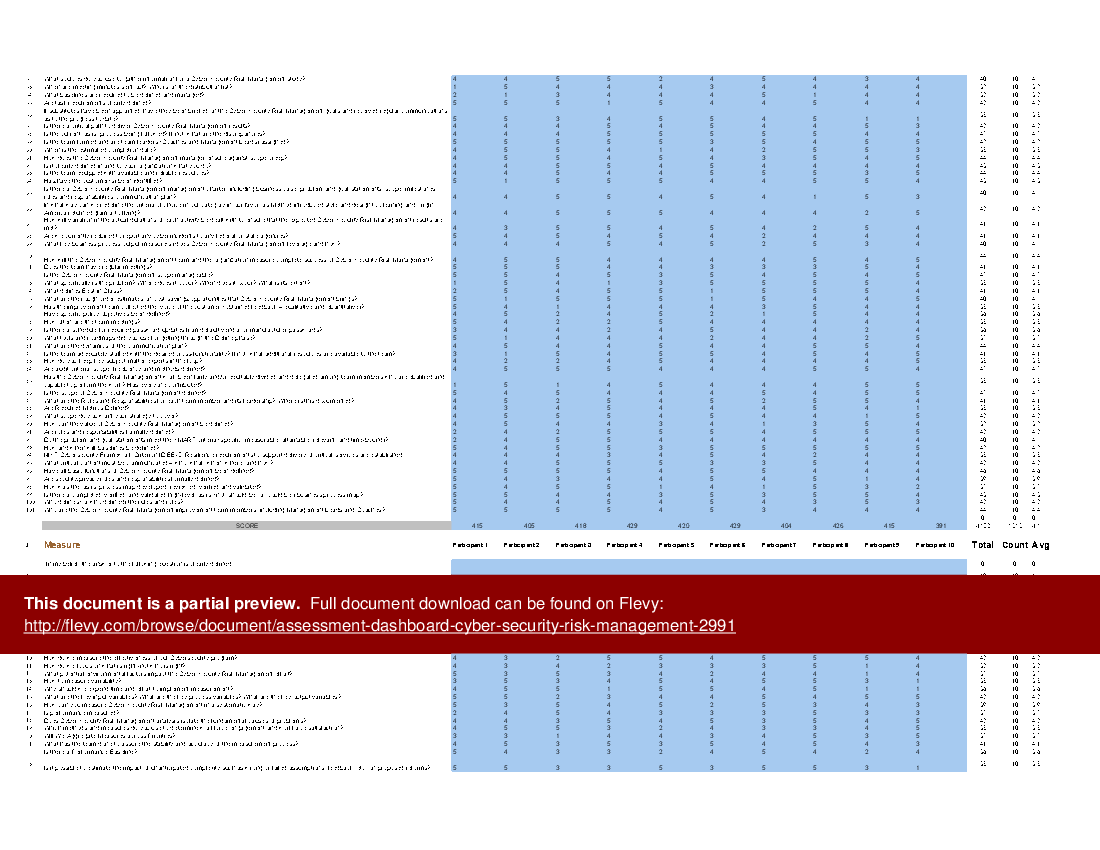
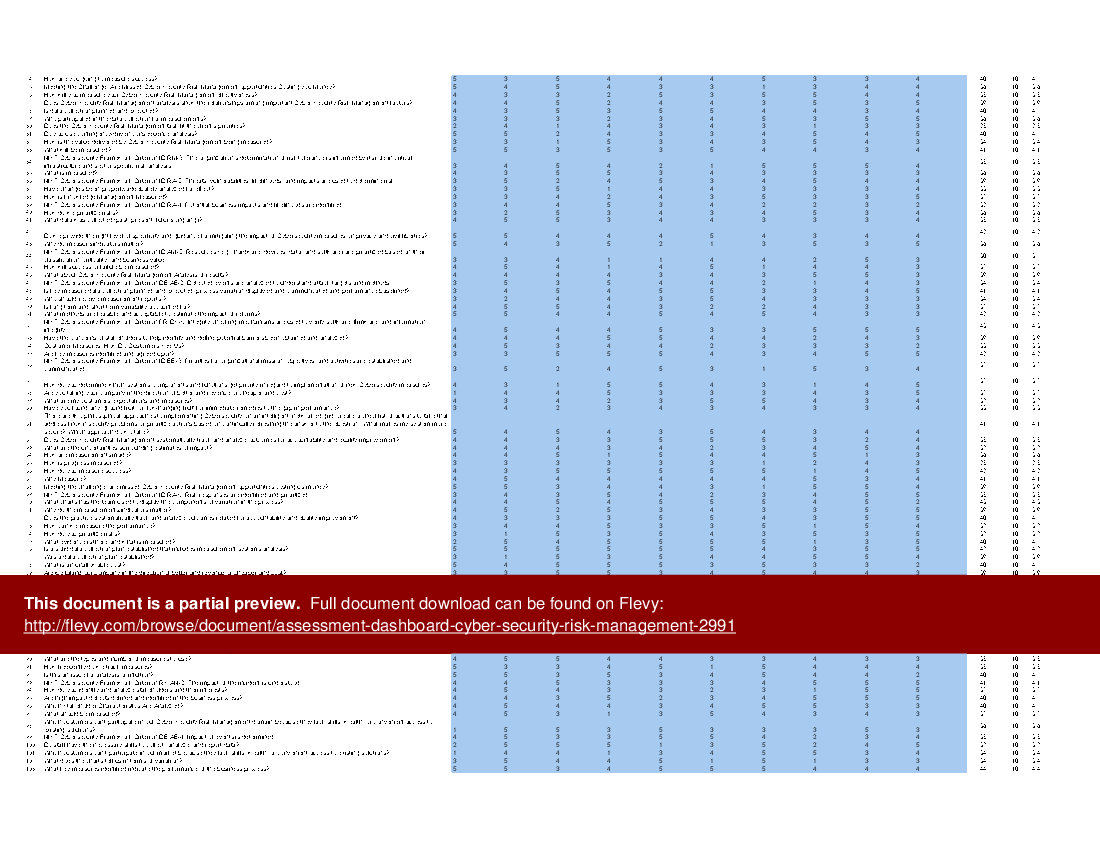
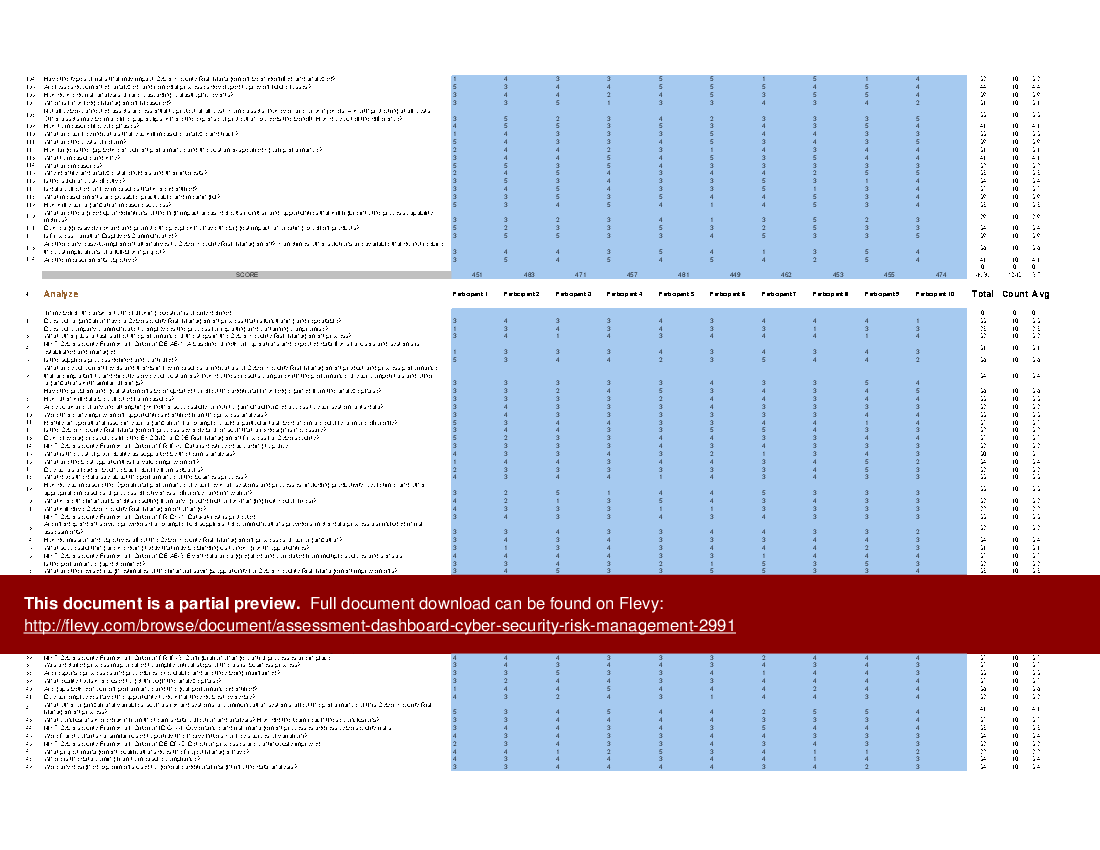
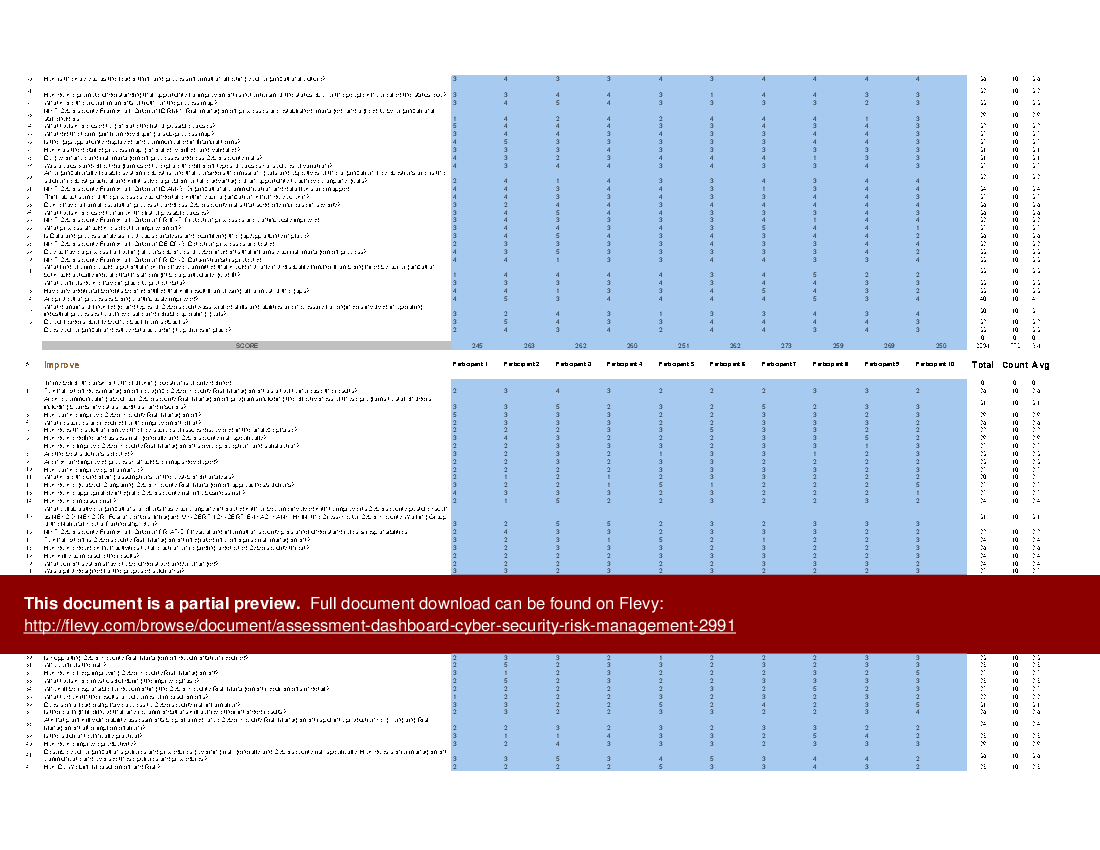
All the tools you need to an in-depth Cyber Security Risk Management Self-Assessment. Featuring 913 new and updated case-based criteria, organized into seven core areas of process design, this Self-Assessment will help you identify areas in which Cyber Security Risk Management improvements can be made.
The Self Assessment tool is a comprehensive dashboard built in MS Excel. It ensures you don't miss anything with 913 criteria in 7 RDMAICS (Recognize, Define, Measure, Analyze, Improve, Control and Sustain) steps with easy and quick navigating and answering for 1-10 participants.
The above preview showcases an example of a completed version. The secondary document includes a blank template, as well as a detailed 140+ page PDF guide. The guide provides a convenient way to distribute and share among the participants to prepare and discuss the Self Assessment.
Got a question about the product? Email us at support@flevy.com or ask the author directly by using the "Ask the Author a Question" form. If you cannot view the preview above this document description, go here to view the large preview instead.
Source: Best Practices in Cyber Security Excel: Assessment Dashboard - Cyber Security Risk Management Excel (XLSX) Spreadsheet, Gerard Blokdijk
OVERVIEW
![]() (XLSX)
(XLSX)![]() (ZIP)
(ZIP)
Gerard is the CEO at The Art of Service. He has been providing information technology insights, talks, tools and products to organizations in a wide range of industries for over 25 years. Gerard is a widely recognized and respected information expert. Gerard founded The Art of Service consulting business in 2000. Gerard has authored numerous published books to date.
Ask the Author a Question
Cyber Security Kanban Board Risk Management ISO 27001 ITSM Kanban Change Management ITIL Digital Transformation Mobile Strategy Enterprise Architecture Service Management Customer Experience Business Transformation Change Readiness Business Continuity Planning IEC 27002 Business Architecture