Culture of Security (PowerPoint PPTX Slide Deck)
PowerPoint (PPTX) 28 Slides FlevyPro Document
RISK MANAGEMENT PPT DESCRIPTION
Advancement in technology, unfortunately, has helped attackers be more aggressive and capable of inflicting more damage to IT systems and infrastructure deployed at most enterprises today.
Application security tools and techniques are also evolving continuously. However, they are not up to the mark, as organizations still fall prey to vulnerabilities—e.g., cross-site scripting, SQL injection, access control, and business logic errors. The primary reason is failure to focus on establishing strong defenses against threats, merely doing patch work, and leaving the weaknesses unguarded.
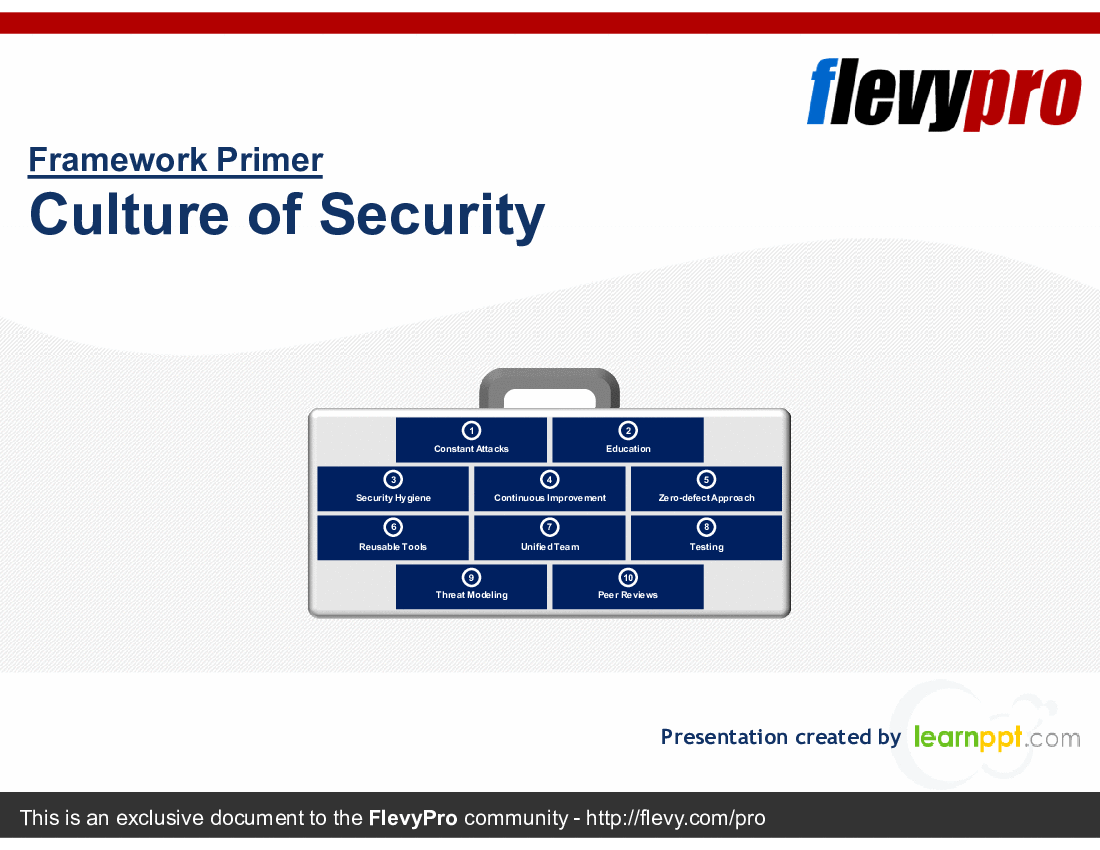
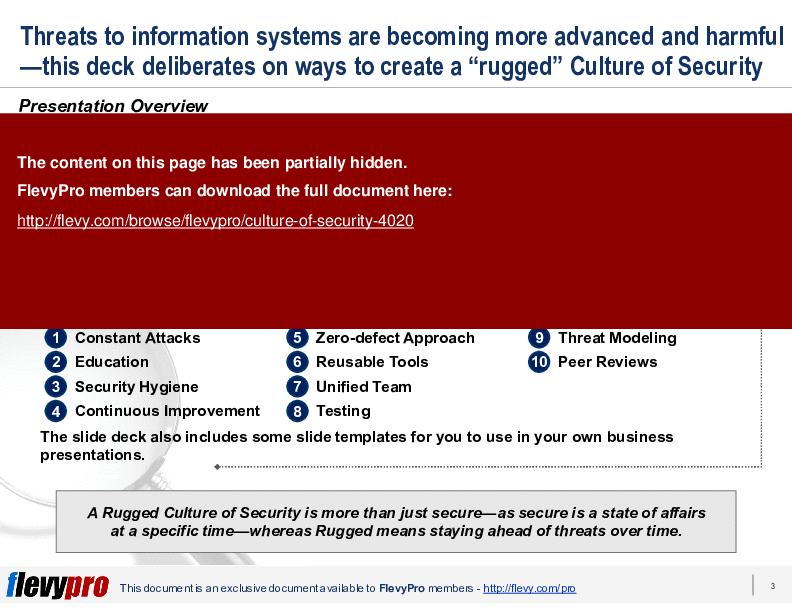
This deck provides a detailed overview of Rugged software, its development, and the guiding principles to enable a Rugged Culture of Security. The 10 guiding principles include:
1. Constant Attacks
2. Education
3. Security Hygiene
4. Continuous Improvement
5. Zero-defect Approach
6. Reusable Tools
7. Unified Team
8. Testing
9. Threat Modeling
10. Peer Reviews
The slide deck also includes some slide templates for you to use in your own business presentations.
The PPT dives into the current state of security, highlighting the increasing complexity and interconnectedness of business applications. It underscores the importance of integrating security tools and practices into organizational systems to prevent vulnerabilities such as SQL injections, access control issues, and business logic errors. The material emphasizes that security is not just a technical concern, but a strategic business objective that needs to be aligned with overall organizational goals.
A case study on the U.S. Citizenship and Immigration Services (USCIS) illustrates the practical application of these principles. The case study details how the new CIO at USCIS overhauled the existing security culture, implemented multifactor authentication, and incorporated automated security tests into the software development process. This real-world example provides valuable insights into how a proactive approach to security can lead to significant improvements in system resilience and overall security posture.
Got a question about this document? Email us at flevypro@flevy.com.
Source: Best Practices in Corporate Culture, Cybersecurity, Security PowerPoint Slides: Culture of Security PowerPoint (PPTX) Presentation Slide Deck, LearnPPT Consulting
Did you need more documents?
Consider a FlevyPro subscription from $39/month. View plans here.
For $10.00 more, you can download this document plus 2 more FlevyPro documents. That's just $13 each.