Cyber Security Toolkit (PowerPoint PPTX Slide Deck)
PowerPoint (PPTX) 237 Slides
BENEFITS OF THIS POWERPOINT DOCUMENT
- Empowers organizations with a comprehensive understanding of cyber threats and effective cybersecurity management strategies.
- Equips individuals with knowledge and tools to implement industry-leading security controls like Intrusion Detection Prevention Systems and Security Information and Event Management.
- Guides organizations in adopting renowned standards such as NIST Framework for Cyber Security and ISO/IEC 27001 for robust and compliant security management.
CYBER SECURITY PPT DESCRIPTION
Introducing the Ultimate Cybersecurity and IT Security Toolkit: Safeguarding Your Digital Fortresses
In today's interconnected world, cybersecurity is more critical than ever. The ever-evolving landscape of cyber threats demands robust protection measures for individuals and organizations alike. To equip you with the knowledge and tools needed to safeguard your digital fortresses, we proudly present the comprehensive Cybersecurity and IT Security Toolkit – a 230+ slides PowerPoint deck designed to cover every aspect of cybersecurity you need to know. Let's delve into the key learning objectives that this powerful toolkit offers:
Learning Objective 1: Understanding Cyber Crimes
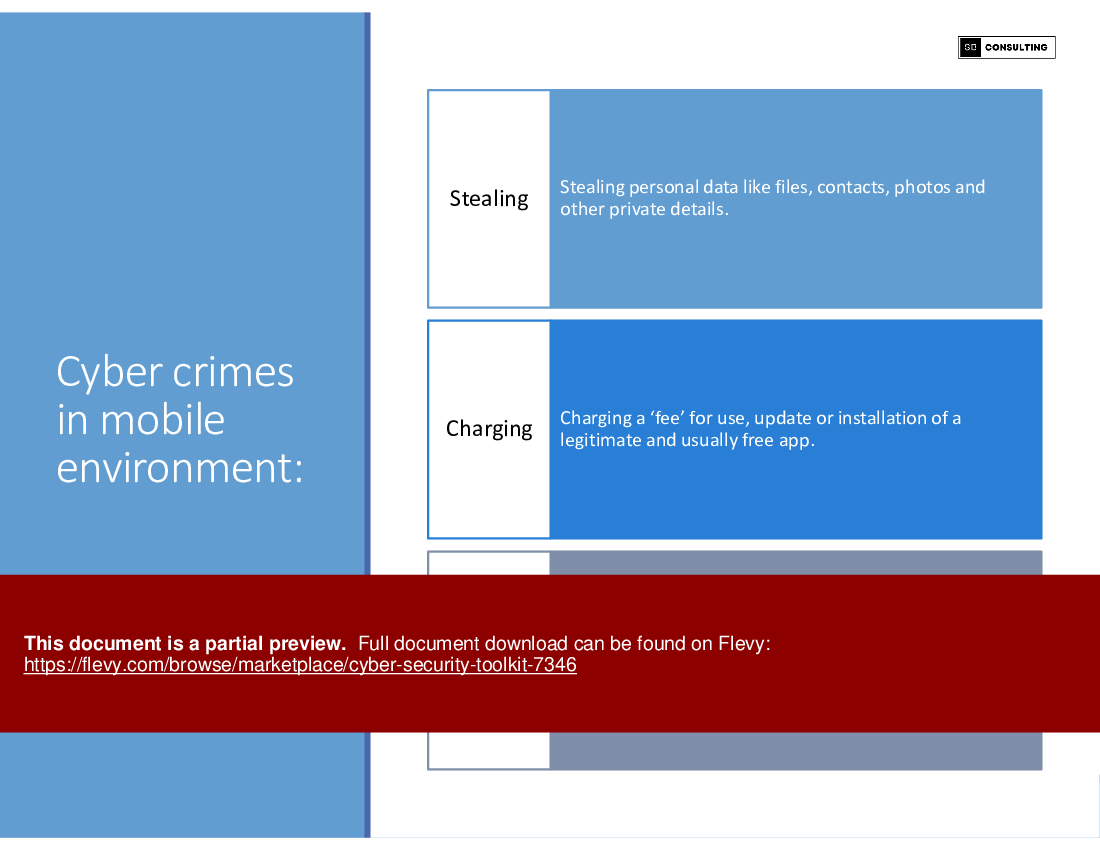
The first section of the toolkit shines a light on the dark world of cyber crimes. From hacking and data breaches to ransomware attacks and identity theft, we provide a comprehensive overview of the various cyber threats that lurk in the shadows. Armed with this knowledge, you'll gain insight into the tactics employed by cybercriminals, enabling you to stay one step ahead and fortify your defenses.
Learning Objective 2: Importance and Benefits of Cybersecurity
Why is cybersecurity so crucial in today's digital age? This section delves deep into the significance of cybersecurity and the multitude of benefits it brings to individuals and organizations. Discover how a robust cybersecurity posture can protect your sensitive data, preserve your reputation, and keep your operations running smoothly in the face of potential cyber threats.
Learning Objective 3: Understanding Cybersecurity
Here, we lay the foundation of cybersecurity knowledge. From the fundamentals of cybersecurity principles to the role of encryption and authentication, you'll gain a solid understanding of the core concepts that underpin cyber defense strategies. Whether you're a beginner or seasoned professional, this section provides invaluable insights.
Learning Objective 4: Cyber Security Frameworks
Navigating the world of cybersecurity can be complex, but fear not! This part of the toolkit introduces various cybersecurity frameworks that serve as roadmaps for implementing effective security measures. Unravel the key components of renowned frameworks such as NIST and ISO/IEC 27001, empowering you to tailor the best-fit approach for your organization.
Learning Objective 5: Types of Cyber Attacks
Knowledge is power, and understanding your adversaries is critical. In this section, we unveil the different types of cyber attacks, ranging from malware and phishing to DDoS attacks and insider threats. By comprehending these attack vectors, you'll be better prepared to detect, prevent, and respond to potential incidents.
Learning Objective 6: Cyber Security Management
In the realm of cybersecurity, preparation is key. Learn how to establish a robust cyber security management strategy that aligns with your organization's objectives and risk tolerance. From risk assessment and vulnerability management to incident response planning, this section equips you with the tools to lead your team in safeguarding your digital assets.
Learning Objective 7: Organizational IT-Security
Organizational culture plays a significant role in cybersecurity success. This segment focuses on instilling a security-first mindset across your organization. Discover the best practices for security awareness training, creating a security-conscious workforce, and fostering a culture of vigilance against potential threats.
Learning Objective 8: Cyber Security Controls
Implementing effective security controls is crucial for mitigating risks and securing your IT infrastructure. Learn about access controls, encryption, network segmentation, and other fundamental security controls that form the backbone of a robust security architecture.
Learning Objective 9: Intrusion Detection Prevention Systems (IDPS)
Detecting and stopping cyber threats in real-time is vital for minimizing damage. Dive into the world of Intrusion Detection and Prevention Systems (IDPS), understanding how these technologies analyze network traffic, detect anomalies, and respond to potential intrusions.
Learning Objective 10: Security Information and Event Management (SIEM)
In the ever-expanding digital landscape, monitoring security events is paramount. This section introduces Security Information and Event Management (SIEM) solutions, helping you centralize and analyze security-related data to identify potential threats proactively.
Learning Objective 11: Security Incident Handling
No matter how robust your defenses are, incidents may still occur. This part equips you with the knowledge and techniques to handle security incidents efficiently. Learn how to investigate, contain, eradicate, and recover from security breaches, minimizing the impact on your organization.
Learning Objective 12: NIST Framework for Cyber Security
The NIST Cybersecurity Framework is a renowned standard for improving cybersecurity risk management. In this section, we break down the framework's core components, guiding you in implementing a structured approach to managing cybersecurity risks.
Learning Objective 13: ISO/IEC 27001
ISO/IEC 27001 is a globally recognized standard for information security management systems. Here, we explain the key principles and processes behind this standard, enabling you to establish a robust and compliant security management system.
Embrace the Power of Knowledge and Protection:
The Cybersecurity and IT Security Toolkit is your all-encompassing resource for building a formidable defense against cyber threats. Equip yourself with the knowledge and tools necessary to safeguard your digital assets, protect your reputation, and ensure the continuity of your operations. Take charge of your cybersecurity journey today and stay ahead in the battle against cybercrime.
Disclaimer: The information provided in this article is for educational purposes only. Implementation of cybersecurity measures should be done with the advice and expertise of qualified professionals.
Key Words:
Strategy & Transformation, Growth Strategy, Strategic Planning, Strategy Frameworks, Innovation Management, Pricing Strategy, Core Competencies, Strategy Development, Business Transformation, Marketing Plan Development, Product Strategy, Breakout Strategy, Competitive Advantage, Mission, Vision, Values, Strategy Deployment & Execution, Innovation, Vision Statement, Core Competencies Analysis, Corporate Strategy, Product Launch Strategy, BMI, Blue Ocean Strategy, Breakthrough Strategy, Business Model Innovation, Business Strategy Example, Corporate Transformation, Critical Success Factors, Customer Segmentation, Customer Value Proposition, Distinctive Capabilities, Enterprise Performance Management, KPI, Key Performance Indicators, Market Analysis, Market Entry Example, Market Entry Plan, Market Intelligence, Market Research, Market Segmentation, Market Sizing, Marketing, Michael Porter's Value Chain, Organizational Transformation, Performance Management, Performance Measurement, Platform Strategy, Product Go-to-Market Strategy, Reorganization, Restructuring, SWOT, SWOT Analysis, Service 4.0, Service Strategy, Service Transformation, Strategic Analysis, Strategic Plan Example, Strategy Deployment, Strategy Execution, Strategy Frameworks Compilation, Strategy Methodologies, Strategy Report Example, Value Chain, Value Chain Analysis, Value Innovation, Value Proposition, Vision Statement, Corporate Strategy, Business Development
NOTE:Our digital products are sold on an "as is" basis, making returns and refunds unavailable post-download. Please preview and inquire before purchasing. Please contact us before purchasing if you have any questions! This policy aligns with the standard Flevy Terms of Usage.
Explore real-time analytics and rule-based approaches to counter cyber threats effectively. Understand how to balance security measures with employee trust and privacy.
Got a question about the product? Email us at support@flevy.com or ask the author directly by using the "Ask the Author a Question" form. If you cannot view the preview above this document description, go here to view the large preview instead.
TOPIC FAQ
What cybersecurity frameworks should I consider when building a security program?
Common frameworks to evaluate include NIST and ISO/IEC 27001, both referenced as roadmaps for implementing security measures. NIST helps structure risk-based activities and ISO/IEC 27001 underpins an information security management system, making these 2 frameworks key starting points in many programs.Which types of cyber attacks should security teams prioritize defending against?
Security teams commonly focus on malware, phishing, ransomware, data breaches, identity theft, distributed denial-of-service (DDoS) attacks, and insider threats. Understanding these vectors informs prevention, detection, and response planning, including controls and monitoring for malware, phishing, DDoS, and insider threats.What core security controls reduce enterprise risk most effectively?
Fundamental controls include access controls, encryption, network segmentation, and layered detection such as IDPS and SIEM. Implementing these controls addresses unauthorized access, lateral movement, and data protection, with access controls, encryption, and network segmentation as practical starting controls.How should I choose a cybersecurity toolkit or template set for my team?
Prioritize toolkits that map to recognized frameworks (NIST, ISO/IEC 27001), include incident response content, and cover detection technologies such as IDPS and SIEM. Also confirm format and size suit your needs; the Cyber Security Toolkit, for example, provides framework and incident handling material aligned to NIST and ISO/IEC 27001.What should I consider about time and internal capacity before buying a security slide deck?
If your team lacks presentation or template design capacity and needs pre-built content for strategy, controls, and incident response, a large deck can save time. Confirm the deck’s scope and format match your needs and be aware of purchase terms; the Cyber Security Toolkit is a 237-slide PPTX sold as a digital download.What should an incident response plan include after a security breach?
Core incident response activities include investigation, containment, eradication, and recovery to minimize impact and restore operations. Effective plans also define roles, escalation paths, and evidence collection procedures; the Cyber Security Toolkit includes material on security incident handling covering investigate, contain, eradicate, and recover.How do IDPS and SIEM differ, and what should I evaluate when selecting them?
IDPS focuses on real-time network and host traffic analysis to detect and prevent intrusions, while SIEM centralizes and correlates security event data for monitoring and investigation. Evaluate detection capability, integration, and analytics to ensure IDPS and SIEM work together effectively, as explained in the toolkit’s IDPS and SIEM sections.How can I align my information security program with ISO/IEC 27001 requirements?
Aligning requires establishing an information security management system (ISMS), documenting key principles and processes, and mapping controls to the standard’s requirements. Use gap analysis and documented policies to build compliance evidence; the Cyber Security Toolkit provides explanations of ISO/IEC 27001 principles to support ISMS setup.Source: Best Practices in Cyber Security, ISO 27001 PowerPoint Slides: Cyber Security Toolkit PowerPoint (PPTX) Presentation Slide Deck, SB Consulting