Access Management Process (ITSM, IT Service Management) (PowerPoint PPTX Slide Deck)
PowerPoint (PPTX) 19 Slides
BENEFITS OF THIS POWERPOINT DOCUMENT
- Easier implementation of ITSM Service Operation processes in your Organisation
- ISO 20000 and ITSM best practice compliant
- Awareness and Implementation Workshop for Access Management process
SLM PPT DESCRIPTION
IT Access Management Process is a part of ITSM Service Operation.
This Document contains detailed description of the IT Access Management Process, including:
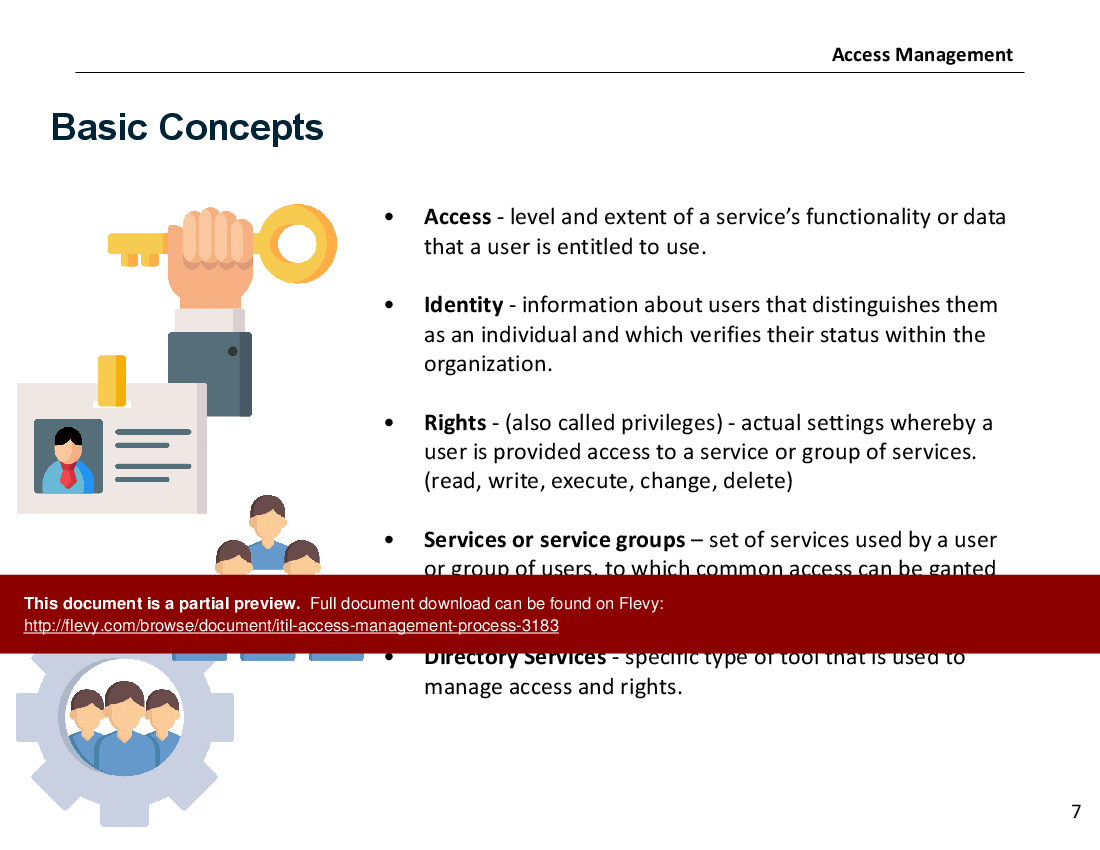
• Key definitions
• Purpose and Objectives
• Scope
• Roles
• Value to business
• Basic Concepts
• Process Workflow – step by step
• Triggers
• Process Inputs / Outputs/ Interfaces
• Information Management
• Challenges
• Risks
• Critical success factors (CSF)
• Key Performance Indicators (KPIs)
IT Access Management Process is a part of ITSM Service Operation.
This document contains detailed description of the IT Access Management Process.
This comprehensive PPT delves into the intricacies of Access Management within IT Service Management (ITSM). It outlines the purpose and objectives, emphasizing the importance of controlling access, maintaining confidentiality, and ensuring regulatory compliance. The document provides a clear framework for managing access rights, reducing data entry errors, and maintaining an audit trail, which are critical for any organization aiming to uphold stringent security standards.
Roles and responsibilities are clearly defined, with a single Access Management process maintained by Information Security Management and executed by various Service Operation functions. The document highlights the necessity of a coordinated approach, often centralized within IT Operations Management or the Service Desk, ensuring consistency and accountability in managing access rights.
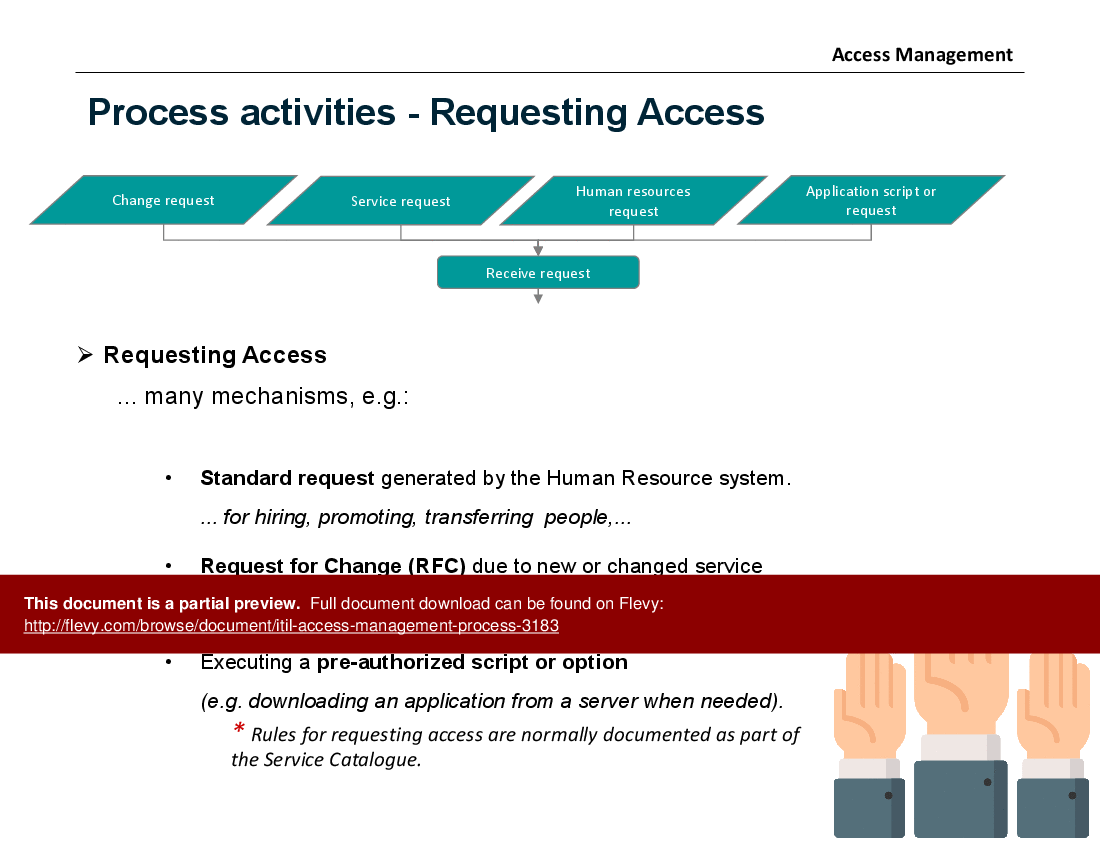
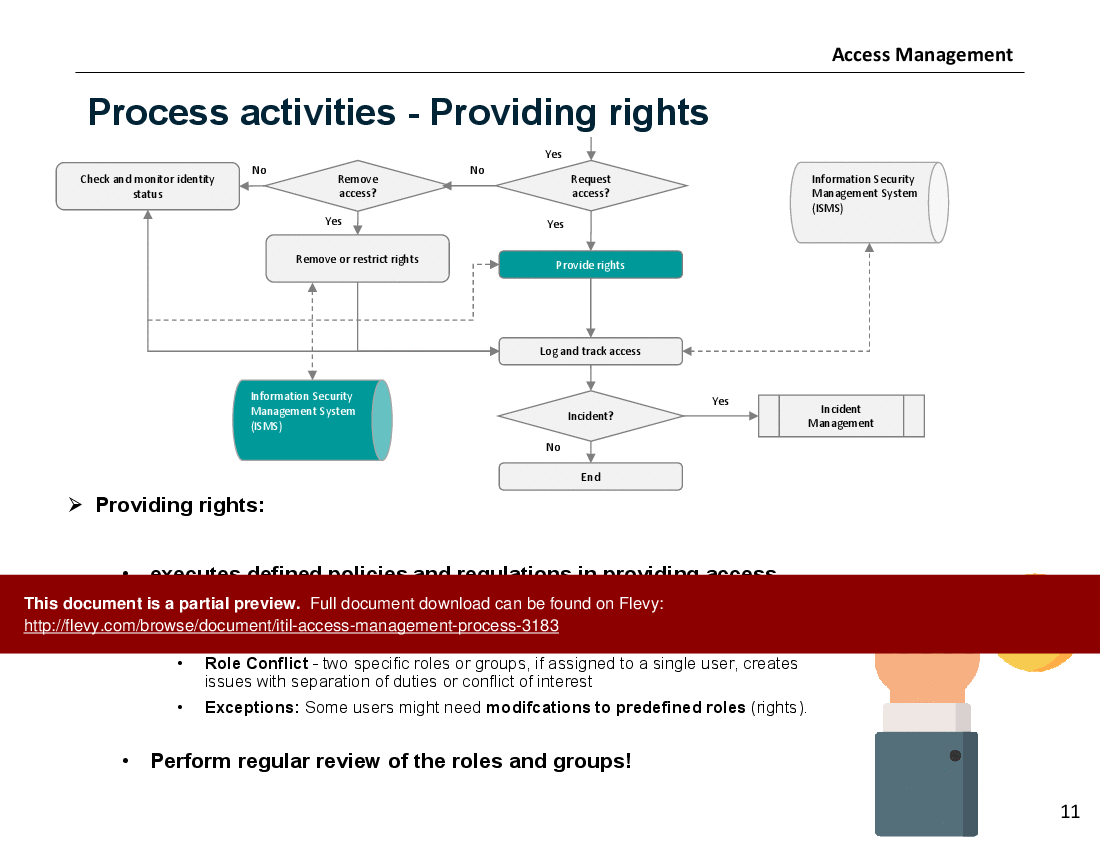
The document also covers essential process activities, including requesting and providing access, and monitoring identity status. It details the mechanisms for requesting access, such as standard requests, RFCs, and pre-authorized scripts, and outlines the procedures for providing rights, including handling role conflicts and exceptions. Regular reviews of roles and groups are recommended to maintain the integrity of the access management process.
Got a question about the product? Email us at support@flevy.com or ask the author directly by using the "Ask the Author a Question" form. If you cannot view the preview above this document description, go here to view the large preview instead.
Source: Best Practices in SLM, ITSM, Access Management PowerPoint Slides: Access Management Process (ITSM, IT Service Management) PowerPoint (PPTX) Presentation Slide Deck, ITSM Consulting