Editor's Note: Take a look at our featured best practice, Digital Transformation Strategy (145-slide PowerPoint presentation). Digital Transformation is being embraced by organizations across most industries, as the role of technology shifts from being a business enabler to a business driver. This has only been accelerated by the COVID-19 global pandemic. Thus, to remain competitive and outcompete in today's fast paced, [read more]
Also, if you are interested in becoming an expert on Digital Transformation, take a look at Flevy's Digital Transformation Frameworks offering here. This is a curated collection of best practice frameworks based on the thought leadership of leading consulting firms, academics, and recognized subject matter experts. By learning and applying these concepts, you can you stay ahead of the curve. Full details here.
* * * *
 Buying gold and silver bullion has always required a high level of security. But in modern times, technology is reshaping exactly how secure these transactions can be. From blockchain to AI, cutting-edge innovations are making buying precious metals safer and more transparent.
Buying gold and silver bullion has always required a high level of security. But in modern times, technology is reshaping exactly how secure these transactions can be. From blockchain to AI, cutting-edge innovations are making buying precious metals safer and more transparent.
Are you curious about how these advancements protect your investments? Let’s explore the technologies that are transforming secure transactions in the world of bullion purchasing.
Cybersecurity Best Practices Are Ensuring Safety for Buying Online Bullion
Securing online bullion transactions demands robust cybersecurity measures. In addition to using reputable sources, like the bullion dealer Pimbex, to minimize risks, utilize:
- Encryption, to ensure your data stays private during transfers.
- Multi-factor authentication, to provide an extra security layer, making unauthorized access tougher.
- Regular software updates, to close any security gaps promptly.
- Secure payment gateways, to further shield you from fraud.
- Advanced threat detection systems, to catch suspicious activities early on.
By staying vigilant and adopting these best practices, you can significantly reduce cyber threats when buying precious metals online.
Blockchain Is Revolutionizing Bullion Verification and Ownership
Blockchain technology reshapes the way we verify and own bullion. Its decentralized ledger provides transparency, ensuring every transaction is tamper-proof and traceable.
When you buy gold or silver, blockchain records your purchase in an immutable database. This means no more disputes over ownership; everything’s crystal clear on the public ledger. For instance, verifying the authenticity of bullion becomes straightforward since each piece has a unique digital signature linked to its physical counterpart.
Moreover, this technology cuts down intermediary costs by automating processes through smart contracts. These self-executing contracts ensure both parties meet their obligations without needing middlemen.
In short, blockchain ensures trustworthiness and efficiency in bullion transactions like never before.
AI-Driven Fraud Detection Is Enhancing the Security of Precious Metals Trading
Artificial intelligence revolutionizes fraud detection in precious metals trading. With advanced algorithms, AI analyzes vast datasets to identify unusual patterns and behaviors indicative of fraud.
For instance, machine learning models can detect anomalies in transaction volumes or timings that human analysts might miss. This early warning system helps traders react swiftly to potential threats.
Additionally, natural language processing scans for suspicious communication across various channels, flagging potential collusion or deceptive practices.
Combining these techniques makes AI a powerful tool for maintaining market integrity.
AI-driven systems also adapt over time, continuously improving their accuracy as they learn from new data. So, embracing AI enhances security and trustworthiness in the bullion trading industry.
Biometric Authentication Is Enhancing Security for Gold Purchases
Biometric authentication takes security in gold purchases to a new level. Using unique biological traits like fingerprints, facial recognition, or iris scans ensures that only authorized individuals can complete transactions.
This method is nearly foolproof since biometric data is incredibly difficult to replicate or forge. When you buy bullion online or in person, these systems add an extra layer of protection against identity theft and fraud.
For example, integrating fingerprint scanners at checkout points allows instant verification of buyers. Similarly, facial recognition software can be used on mobile apps to confirm the purchaser’s identity before approving any transaction.
Ultimately, biometrics provide a reliable way to secure your precious metal investments against unauthorized access.
IoT Applications Are Enabling Real-Time Tracking of Physical Gold and Silver
The Internet of Things (IoT) brings real-time tracking to physical gold and silver, transforming how we monitor bullion assets. By embedding IoT sensors in storage containers or packaging, you get live updates on the location and condition of your precious metals.
Imagine having instant alerts if your shipment deviates from its route or encounters environmental hazards like extreme temperatures. These smart sensors can even detect tampering attempts, ensuring the security of your investments.
IoT also enables better inventory management for dealers by providing precise data on stock levels and movement. This transparency enhances trust between buyers and sellers while minimizing risks associated with transporting high-value assets.
With IoT, keeping tabs on your bullion becomes seamless and secure.
Quantum Computing Could Revolutionize Future Financial Security
Quantum computing stands to revolutionize financial security, especially in bullion transactions. Unlike classical computers, quantum systems handle complex calculations at unprecedented speeds, making current encryption methods obsolete.
With quantum encryption, securing gold and silver purchases reaches new heights. Quantum key distribution ensures that any attempt to intercept or tamper with the data is immediately detectable. This adds an unbreakable layer of security to your transactions.
Moreover, quantum algorithms can optimize trading strategies by processing massive datasets instantaneously. This helps predict market movements more accurately and mitigates risks.
Although still emerging, the potential impact of quantum computing on financial security promises a future where bullion transactions are safer and smarter than ever.
The Bottom Line
Technology is revolutionizing secure transactions in bullion purchases, offering unparalleled transparency and protection. For instance, as we have seen, blockchain ensures verifiable ownership, AI enhances fraud detection, biometrics safeguard identities, IoT provides real-time tracking, and quantum computing promises future-proof security.
These advancements not only build trust but also make precious metal investments safer than ever. So, embrace these innovations to stay ahead in the evolving landscape of bullion trading.
Want to Achieve Excellence in Digital Transformation?
Gain the knowledge and develop the expertise to become an expert in Digital Transformation. Our frameworks are based on the thought leadership of leading consulting firms, academics, and recognized subject matter experts. Click here for full details.
Digital Transformation is being embraced by organizations of all sizes across most industries. In the Digital Age today, technology creates new opportunities and fundamentally transforms businesses in all aspects—operations, business models, strategies. It not only enables the business, but also drives its growth and can be a source of Competitive Advantage.
For many industries, COVID-19 has accelerated the timeline for Digital Transformation Programs by multiple years. Digital Transformation has become a necessity. Now, to survive in the Low Touch Economy—characterized by social distancing and a minimization of in-person activities—organizations must go digital. This includes offering digital solutions for both employees (e.g. Remote Work, Virtual Teams, Enterprise Cloud, etc.) and customers (e.g. E-commerce, Social Media, Mobile Apps, etc.).
Learn about our Digital Transformation Best Practice Frameworks here.
Readers of This Article Are Interested in These Resources

1490-slide PowerPoint presentation
Curated by McKinsey-trained Executives
Master Cybersecurity with the Ultimate Guide
Are you ready to elevate your organization's cybersecurity strategy to new heights? Dive into our comprehensive guide, a must-have resource for businesses, IT professionals, and compliance officers seeking
[read more]

23-slide PowerPoint presentation
Cybersecurity is a growing threat and should be at the forefront in any IT Risk Management Strategy. As role of
The PPT outlines the critical elements of a robust cybersecurity strategy, emphasizing the importance of integrity, availability, accountability, and provenance of information. It
[read more]

18-page Word document
This Word Document provides a template for an IT Security & Governance Policy and is easily customisable. Areas cover are: Security, Data Back-Up, Virus Protection, Internet & Email usage, Remote & 3rd Party Network Access, User-Account Management, Procurement, Asset Management and IS Service
[read more]
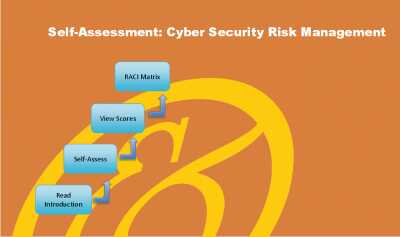
Excel workbook
National Institute of Standards and Technology (NIST) U.S. Department of Commerce Cyber Security Framework Aligned.
Governments, sectors, and organizations around the world are increasingly recognizing the NIST Cyber Security Framework (CSF) as a recommended cyber security baseline to
[read more]
 Buying gold and silver bullion has always required a high level of security. But in modern times, technology is reshaping exactly how secure these transactions can be. From blockchain to AI, cutting-edge innovations are making buying precious metals safer and more transparent.
Buying gold and silver bullion has always required a high level of security. But in modern times, technology is reshaping exactly how secure these transactions can be. From blockchain to AI, cutting-edge innovations are making buying precious metals safer and more transparent.