Cybersecurity Value Chain (PowerPoint PPTX Slide Deck)
PowerPoint (PPTX) 30 Slides
BENEFITS OF THIS POWERPOINT DOCUMENT
- Provides a framework for examining the Cybersecurity Industry (and Function).
- Identifies 15 important insights and considerations for Cybersecurity Value Chain Analysis.
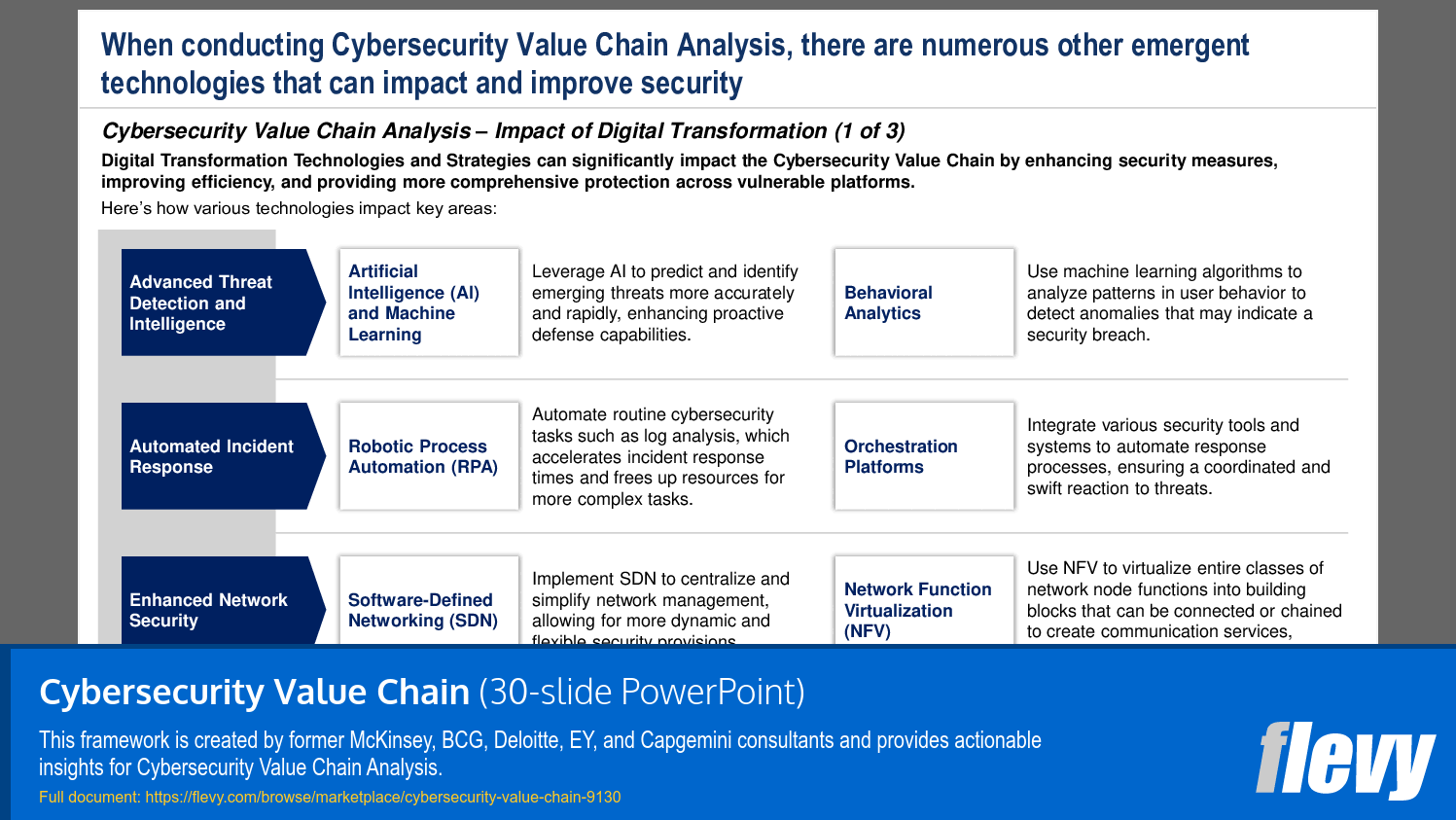
- Provides a detailed breakdown of the impact of other Digital Transformation Technologies across the Cybersecurity Value Chain.
CYBER SECURITY PPT DESCRIPTION
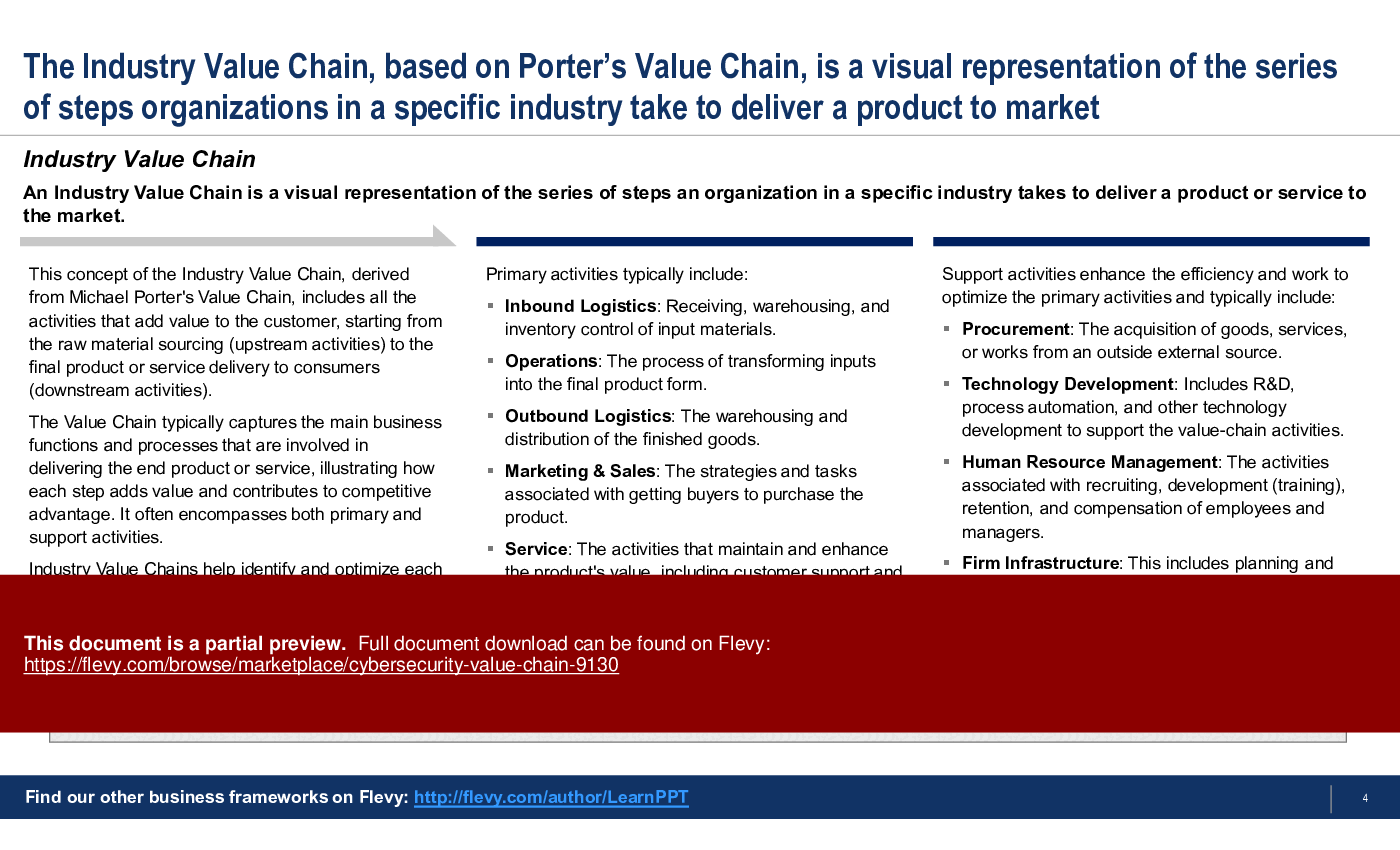
An Industry Value Chain is a visual representation of the series of steps an organization in a specific industry takes to deliver a product or service to the market. It captures the main business functions and processes that are involved in delivering the end product or service, illustrating how each step adds value and contributes to a Competitive Advantage. It often encompasses both primary and support activities.
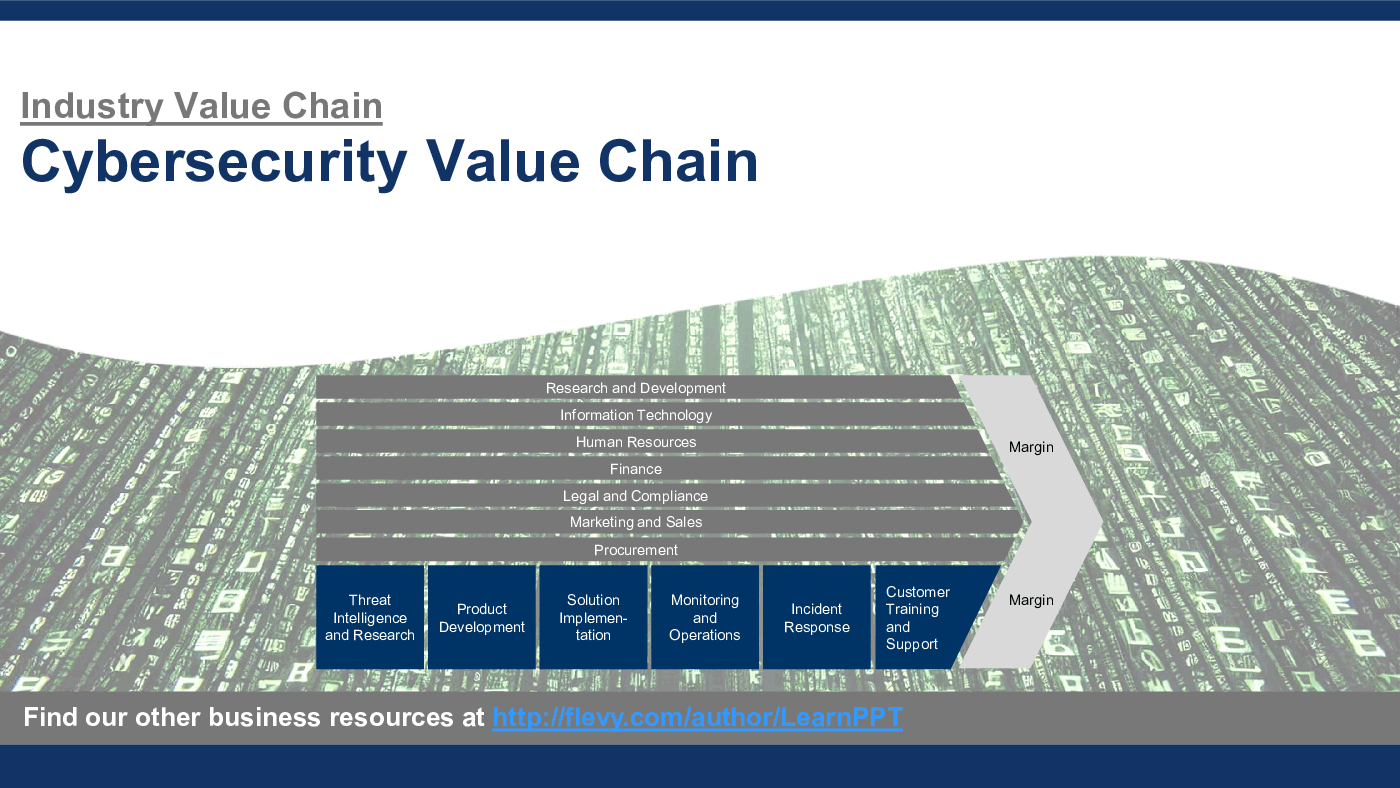
This PowerPoint presentation captures the Cybersecurity Value Chain, which includes the following primary and support activities for Cybersecurity firms:
Primary Activities
1. Threat Intelligence and Research
2. Product Development
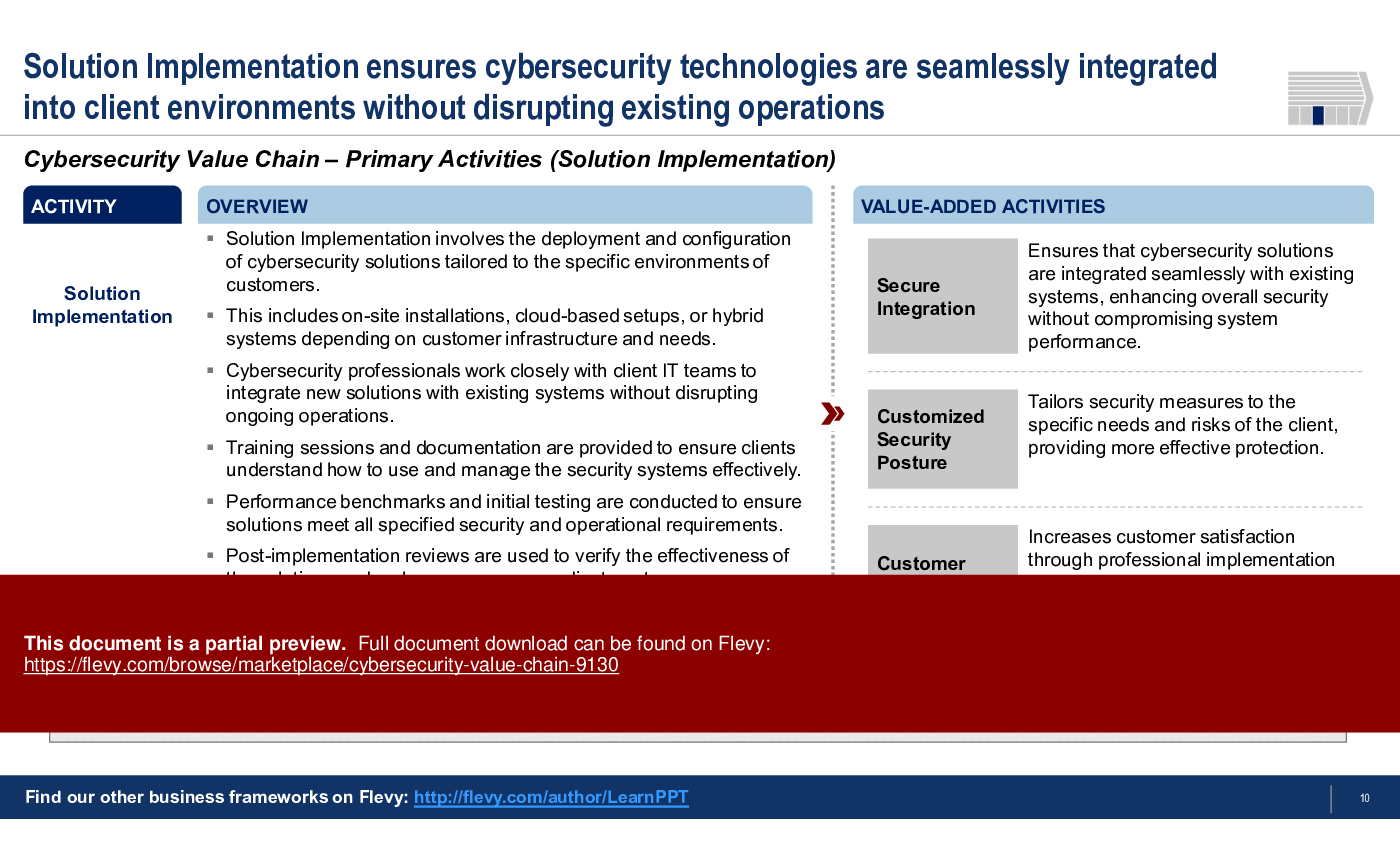
3. Solution Implementation
4. Monitoring and Operations
5. Incident Response
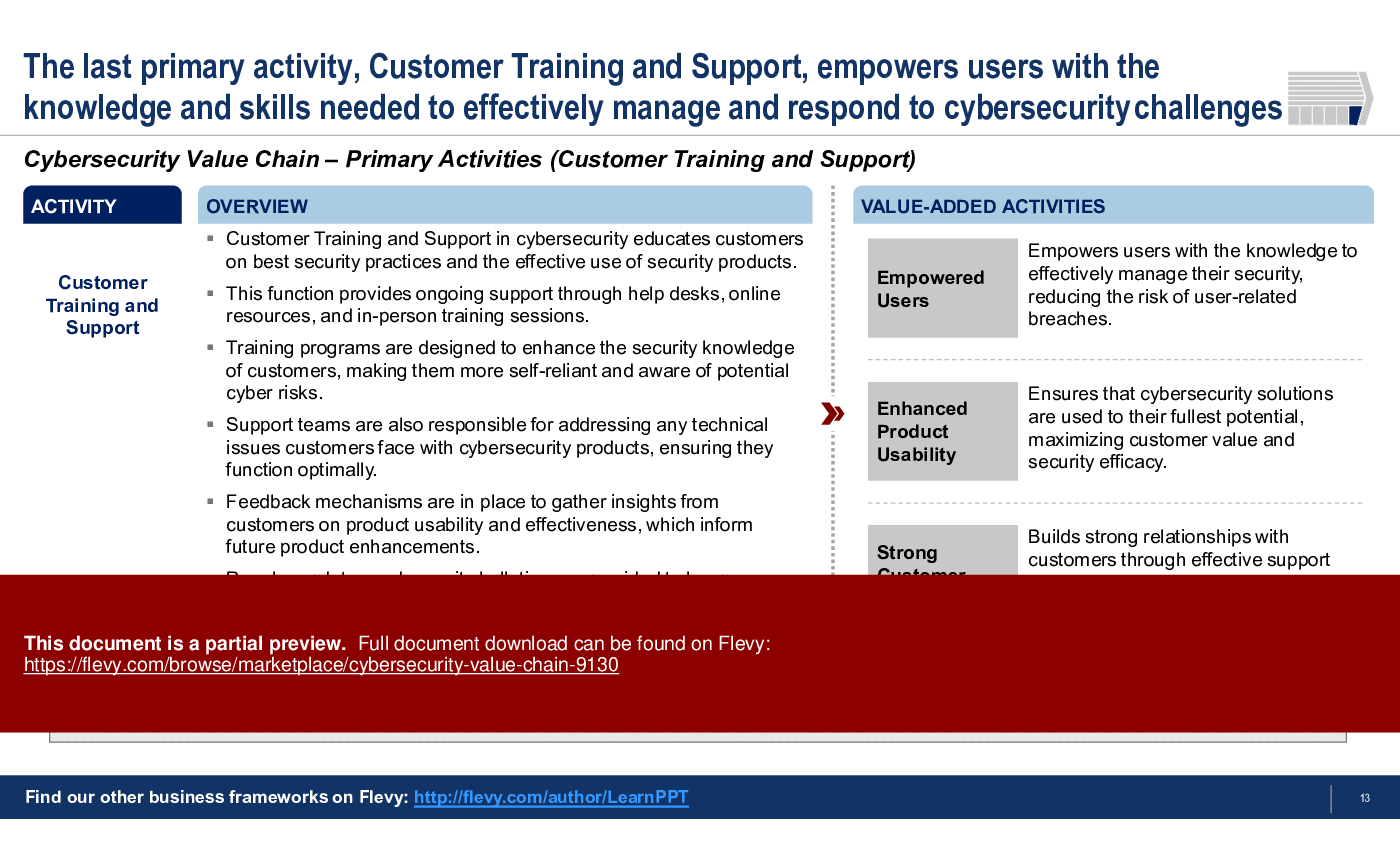
6. Customer Training and Support
Support Activities
1. Research and Development
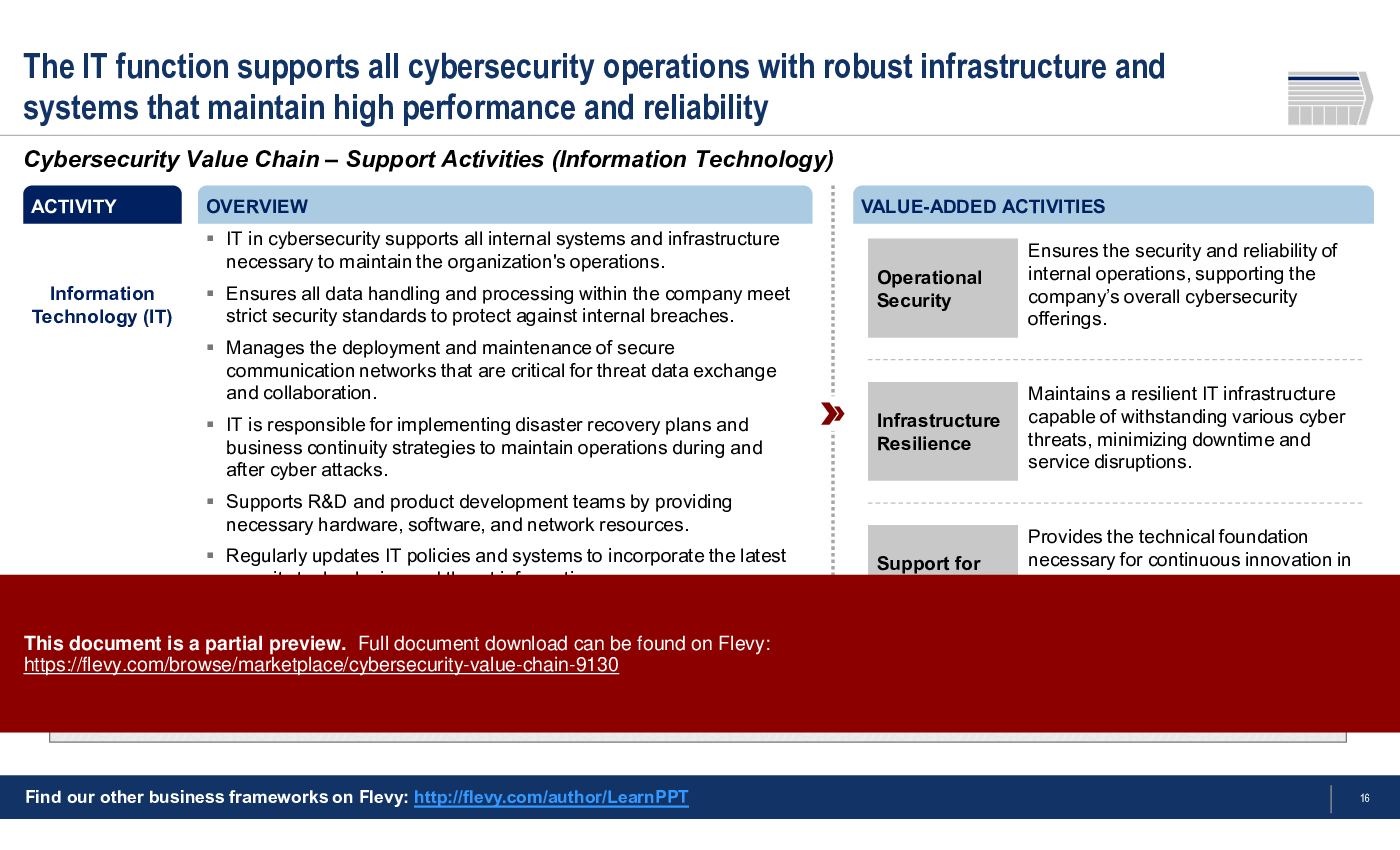
2. Information Technology
3. Human Resources
4. Finance
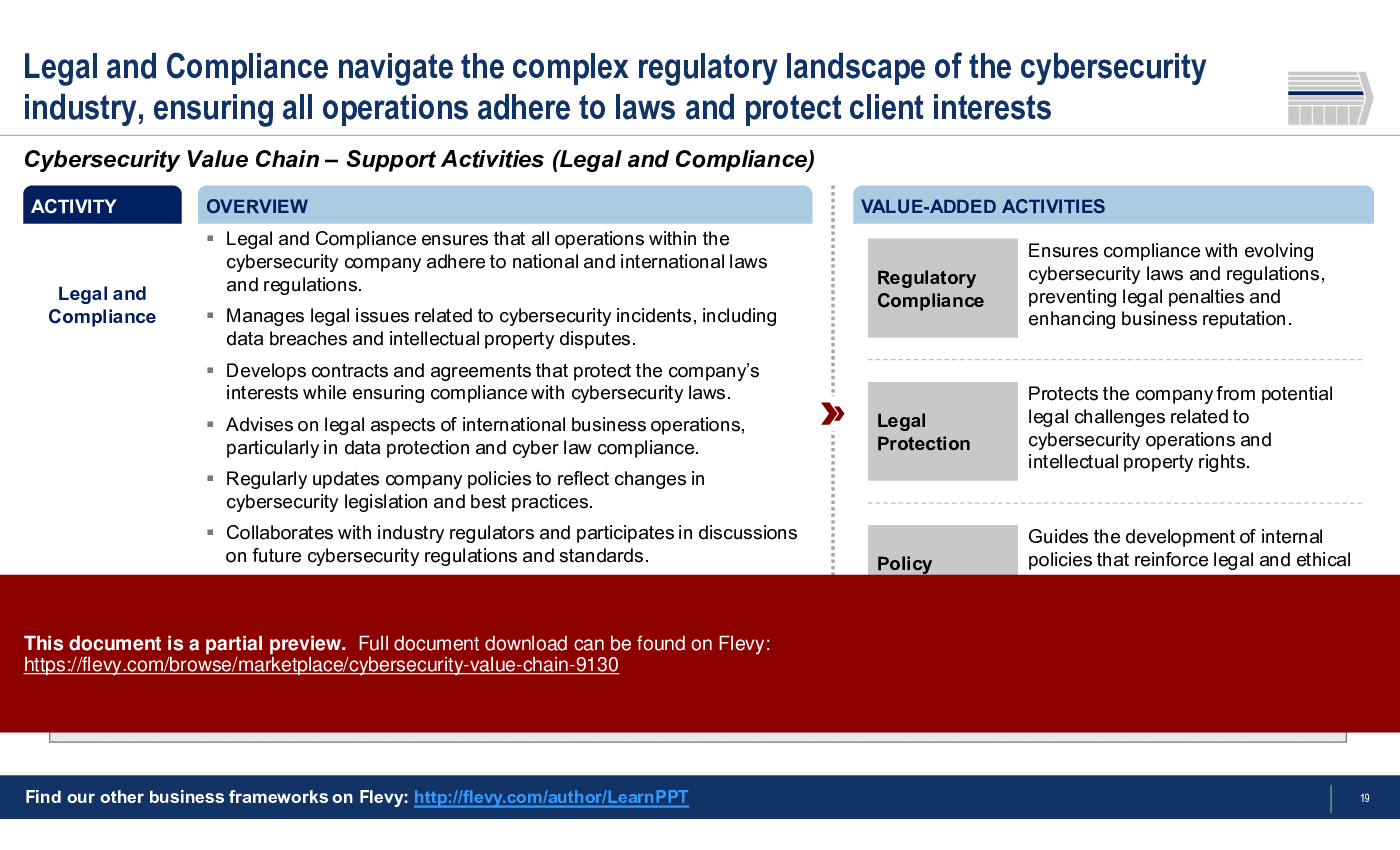
5. Legal and Compliance
6. Marketing and Sales
7. Procurement
This PPT presentation dives deeper into each of these activities, highlighting key elements.
Seamless integration between research, product development, and incident response is critical for delivering timely and effective cybersecurity solutions. Furthermore, continuous innovation within the value chain ensures that cybersecurity measures evolve at the pace of new threat vectors and technological advances. Analyzing the Cybersecurity Value Chain helps allocate resources effectively to the most impactful areas, such as threat research or advanced security technologies, maximizing ROI. Efficient customer training and support strengthen user defenses, turning potential vulnerabilities into informed lines of defense.
This PPT presentation also discusses Cybersecurity Value Chain Analysis, highlighting a multitude of key considerations and potential insights to pay attention to. We further discuss the significant impact of Digital Transformation and various specific emergent technologies on the Cybersecurity industry.
Got a question about the product? Email us at support@flevy.com or ask the author directly by using the "Ask the Author a Question" form. If you cannot view the preview above this document description, go here to view the large preview instead.
MARCUS OVERVIEW
This synopsis was written by Marcus [?] based on the analysis of the full 30-slide presentation.
Executive Summary
The Cybersecurity Value Chain presentation provides a detailed framework for understanding the series of steps that cybersecurity firms undertake to deliver effective security solutions. This consulting-grade resource, developed by former McKinsey, BCG, and Deloitte consultants, outlines both primary and support activities essential for optimizing cybersecurity operations. By leveraging this framework, executives will gain actionable insights into enhancing their cybersecurity strategies, ensuring compliance, and maximizing return on investment (ROI).
Who This Is For and When to Use
• Cybersecurity executives and managers responsible for strategic planning and operational execution
• IT leaders and security analysts focused on threat detection and incident response
• Compliance officers ensuring adherence to cybersecurity regulations
• Business development professionals in cybersecurity firms aiming to enhance service offerings
Best-fit moments to use this deck:
• During strategic planning sessions to align cybersecurity initiatives with business objectives
• For training sessions aimed at enhancing team understanding of the cybersecurity value chain
• When conducting assessments of current cybersecurity operations and identifying areas for improvement
Learning Objectives
• Define the Cybersecurity Value Chain and its significance in delivering security solutions
• Analyze the integration of primary and support activities within the value chain
• Identify key metrics for measuring the effectiveness of cybersecurity operations
• Establish a framework for continuous improvement in cybersecurity practices
• Develop strategies for optimizing resource allocation across the value chain
• Enhance understanding of regulatory compliance requirements in cybersecurity
Table of Contents
• Executive Summary (page 1)
• Cybersecurity Value Chain (page 2)
• Primary Activities (page 3)
• Support Activities (page 4)
• Cybersecurity Value Chain Analysis (page 5)
Primary Topics Covered
• Threat Intelligence and Research - This activity involves gathering and analyzing data on emerging threats to proactively defend against potential cyber attacks.
• Product Development - Focuses on creating innovative cybersecurity solutions tailored to evolving threats, ensuring robust protection for clients.
• Solution Implementation - Ensures seamless integration of cybersecurity technologies into client environments, minimizing operational disruptions.
• Monitoring and Operations - Provides continuous oversight of systems to detect and respond to threats in real-time, enhancing overall security posture.
• Incident Response - Addresses and mitigates security breaches swiftly to minimize impact and restore systems effectively.
• Customer Training and Support - Empowers users with knowledge and skills to manage cybersecurity challenges effectively.
Deliverables, Templates, and Tools
• Threat intelligence gathering template for proactive defense strategies
• Product development roadmap for cybersecurity solutions
• Solution implementation checklist to ensure seamless integration
• Monitoring and operations dashboard for real-time threat detection
• Incident response plan template for effective breach management
• Customer training program outline to enhance user engagement
Slide Highlights
• Overview of the Cybersecurity Value Chain illustrating primary and support activities
• Detailed breakdown of Threat Intelligence and Research with value-added activities
• Insights into Product Development processes and their impact on market competitiveness
• Framework for Monitoring and Operations emphasizing continuous protection
• Incident Response strategies highlighting rapid recovery and damage limitation
Potential Workshop Agenda
Cybersecurity Value Chain Overview (60 minutes)
• Introduce the Cybersecurity Value Chain framework
• Discuss the importance of each primary and support activity
• Identify areas for improvement within current operations
Threat Intelligence and Incident Response Deep Dive (90 minutes)
• Explore best practices for threat intelligence gathering
• Review incident response strategies and case studies
• Develop action plans for enhancing incident response capabilities
Customer Training and Support Session (60 minutes)
• Discuss the importance of user training in cybersecurity
• Develop a customer training program tailored to specific needs
• Gather feedback on training effectiveness and areas for enhancement
Customization Guidance
• Tailor the framework to align with specific organizational goals and cybersecurity threats
• Adjust training materials to reflect the unique needs of client environments
• Incorporate company-specific metrics for measuring success in cybersecurity initiatives
Secondary Topics Covered
• Regulatory compliance considerations in cybersecurity
• The role of advanced technologies in enhancing cybersecurity measures
• Strategies for effective vendor management and procurement in cybersecurity
FAQ
What is the Cybersecurity Value Chain?
The Cybersecurity Value Chain is a framework that outlines the primary and support activities necessary for delivering effective cybersecurity solutions, emphasizing how each step adds value.
How can this framework improve our cybersecurity operations?
By analyzing the value chain, organizations can identify inefficiencies, optimize resource allocation, and enhance overall security effectiveness.
What are the primary activities in the Cybersecurity Value Chain?
The primary activities include Threat Intelligence and Research, Product Development, Solution Implementation, Monitoring and Operations, Incident Response, and Customer Training and Support.
How does the framework address regulatory compliance?
The framework incorporates considerations for legal and compliance aspects, ensuring that all operations adhere to relevant cybersecurity regulations.
What tools are included in the presentation?
The presentation includes templates for threat intelligence gathering, incident response planning, and customer training programs, among others.
How can we customize the framework for our organization?
Organizations can tailor the framework by aligning it with specific business goals, adjusting training materials, and incorporating unique metrics for success.
What role does customer training play in the Cybersecurity Value Chain?
Customer training enhances user knowledge and skills, empowering them to manage cybersecurity challenges effectively and reducing the risk of breaches.
How can we measure the effectiveness of our cybersecurity operations?
Metrics can be established based on the framework's activities, focusing on areas such as incident response times, customer satisfaction, and compliance adherence.
Glossary
• Cybersecurity Value Chain - A framework outlining the series of activities involved in delivering cybersecurity solutions.
• Threat Intelligence - Information gathered about potential threats to anticipate and mitigate risks.
• Incident Response - The process of managing and mitigating the impact of security breaches.
• Product Development - The creation of cybersecurity solutions tailored to evolving threats.
• Monitoring and Operations - Continuous oversight of systems to detect and respond to threats.
• Customer Training - Educational programs designed to enhance user knowledge of cybersecurity practices.
• Regulatory Compliance - Adherence to laws and regulations governing cybersecurity practices.
• Procurement - The process of acquiring necessary tools and technologies for cybersecurity operations.
• Operational Efficiency - The effectiveness of processes in achieving desired outcomes with minimal waste.
• Risk Management - Strategies and practices aimed at identifying and mitigating potential security risks.
• Data Protection - Measures taken to safeguard sensitive information from unauthorized access.
• Supply Chain Security - Ensuring the security of the procurement process to prevent vulnerabilities.
• Customer Satisfaction - The degree to which customers are pleased with the services provided.
• Innovation - The development of new ideas or products to improve cybersecurity measures.
• Market Awareness - Understanding market trends and customer needs in cybersecurity.
• Feedback Mechanisms - Processes for gathering customer insights to drive continuous improvement.
• Operational Continuity - Maintaining essential functions during and after a cybersecurity incident.
• Advanced Technologies - Emerging tools and methodologies that enhance cybersecurity capabilities.
• Behavioral Analytics - Analyzing user behavior patterns to detect anomalies and potential threats.
• Cloud Security - Measures taken to protect data and applications hosted in cloud environments.
• IoT Security - Strategies for securing Internet of Things devices against cyber threats.
• Digital Transformation - The integration of digital technologies into all areas of a business, fundamentally changing how it operates.
CYBER SECURITY PPT SLIDES
Source: Best Practices in Cyber Security, Value Chain Analysis PowerPoint Slides: Cybersecurity Value Chain PowerPoint (PPTX) Presentation Slide Deck, LearnPPT Consulting