Editor's Note: Take a look at our featured best practice, KPI Compilation: 600+ Supply Chain Management KPIs (141-slide PowerPoint presentation). This presentation is a comprehensive collection of Key Performance Indicators (KPI) related to Supply Chain Management (SCM). A KPI is a quantifiable measure used to evaluate the success of an organization, employee, or process in meeting objectives for performance. KPIs are [read more]
Why Cutting Edge Cybersecurity Is Vital for the Supply Chain
Also, if you are interested in becoming an expert on Supply Chain Management (SCM), take a look at Flevy's Supply Chain Management (SCM) Frameworks offering here. This is a curated collection of best practice frameworks based on the thought leadership of leading consulting firms, academics, and recognized subject matter experts. By learning and applying these concepts, you can you stay ahead of the curve. Full details here.
* * * *

Manufacturers can’t prevent natural disasters or diseases. They can be smart about their cyber security. In this article, we take a look at why cutting-edge cybersecurity is an important element of supply chain management, and what can happen when it isn’t in place.
First, What Is Supply Chain Management?
A supply chain is simply the set of stages that raw materials experience before becoming products on the shelf. It begins the moment a material is harvested from the ground and does not end until it’s a finished product.
Depending on the item in question, a supply chain can have many links — often located all across the world. Managing these chains is a logistical challenge, requiring a keen understanding of data, technology, and yes, cyber security.
Supply chain managers are responsible for having backup plans and security processes that will avoid disruptions, and offer alternatives when they do occur.
How Cyber Threats Impact Supply Chains
On May 14th, 2021, Ireland had to shut down all of its healthcare service IT systems. It took weeks to bring them back online. During that time, thousands of patients experienced private healthcare data leaks. Services lagged, and the entire system was thrust into chaos of hitherto unseen proportions.
The culprit? A ransomware attack launched by a band of Russian hackers who go by the name of (yes, this is real) Wizard Spider.
Ransomware is a cyber attack that allows criminals to essentially hijack a network of computers and demand money in return for giving it back.
Ireland did not cave into the demands of Wizard Spider, and consequently spent weeks trying to breathe life back into their IT systems.
If ransomware can create chaos for an entire country, no supply chain is safe. Using this same technology, cyber terrorists could (for example) target manufacturers of vital medical equipment. Or, they could simply choose a business that they found to be vulnerable, using its lack of cutting-edge cyber security to extort money and create chaos.
The Solution
Undoubtedly, most, if not all supply chain systems use some form of cyber security. But while some is always better than none, updates and constant vigilance are required to make sure these systems are as effective as they need to be.
It’s worth noting that while ransomware and other cyber threats have been around ostensibly since the dawn of computers, threats change and grow over time. A system last refigured in 2017 might not have any protections at all in place to prevent the attack that occurred in Ireland last spring.
There are ways to check your system for weak points and make changes that eliminate vulnerabilities. Consider the services of a cyber security analyst. They will take a look at your system in much the same way that a bad actor would, finding out what it takes to get in and then leaving you with actionable recommendations for preventing infiltration.
Prioritizing security is key. Many infiltrations occur not because of outdated software but because of human error. Taking the time to learn cyber security best practices, and then implementing these guidelines company-wide is a vital component of keeping supply chains safe and secure.
People all over the world rely on healthy, highly functioning supply chains. Cutting-edge cyber security is one way to keep supply lines safe, and business running smoothly.
Want to Achieve Excellence in Supply Chain Management (SCM)?
Gain the knowledge and develop the expertise to become an expert in Supply Chain Management (SCM). Our frameworks are based on the thought leadership of leading consulting firms, academics, and recognized subject matter experts. Click here for full details.
Supply Chain Management (SCM) is the design, planning, execution, control, and monitoring of Supply Chain activities. It also captures the management of the flow of goods and services.
In February of 2020, COVID-19 disrupted—and in many cases halted—global Supply Chains, revealing just how fragile they have become. By April, many countries experienced declines of over 40% in domestic and international trade.
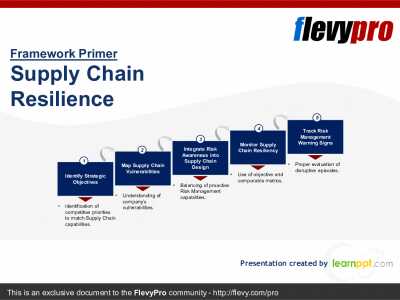
COVID-19 has likewise changed how Supply Chain Executives approach and think about SCM. In the pre-COVID-19 era of globalization, the objective was to be Lean and Cost-effective. In the post-COVID-19 world, companies must now focus on making their Supply Chains Resilient, Agile, and Smart. Additional trends include Digitization, Sustainability, and Manufacturing Reshoring.
Learn about our Supply Chain Management (SCM) Best Practice Frameworks here.
Readers of This Article Are Interested in These Resources
|
|
33-slide PowerPoint presentation
|
|
5-page Word document
| |||
About Shane Avron
Shane Avron is a freelance writer, specializing in business, general management, enterprise software, and digital technologies. In addition to Flevy, Shane's articles have appeared in Huffington Post, Forbes Magazine, among other business journals.
Top 8 Recommended Documents on Supply Chain Resilience
» View more resources Supply Chain Resilience here.
» View the Top 100 Best Practices on Flevy.