Risk Management Process (PowerPoint PPTX Slide Deck)
PowerPoint (PPTX) 65 Slides
RISK MANAGEMENT PPT DESCRIPTION
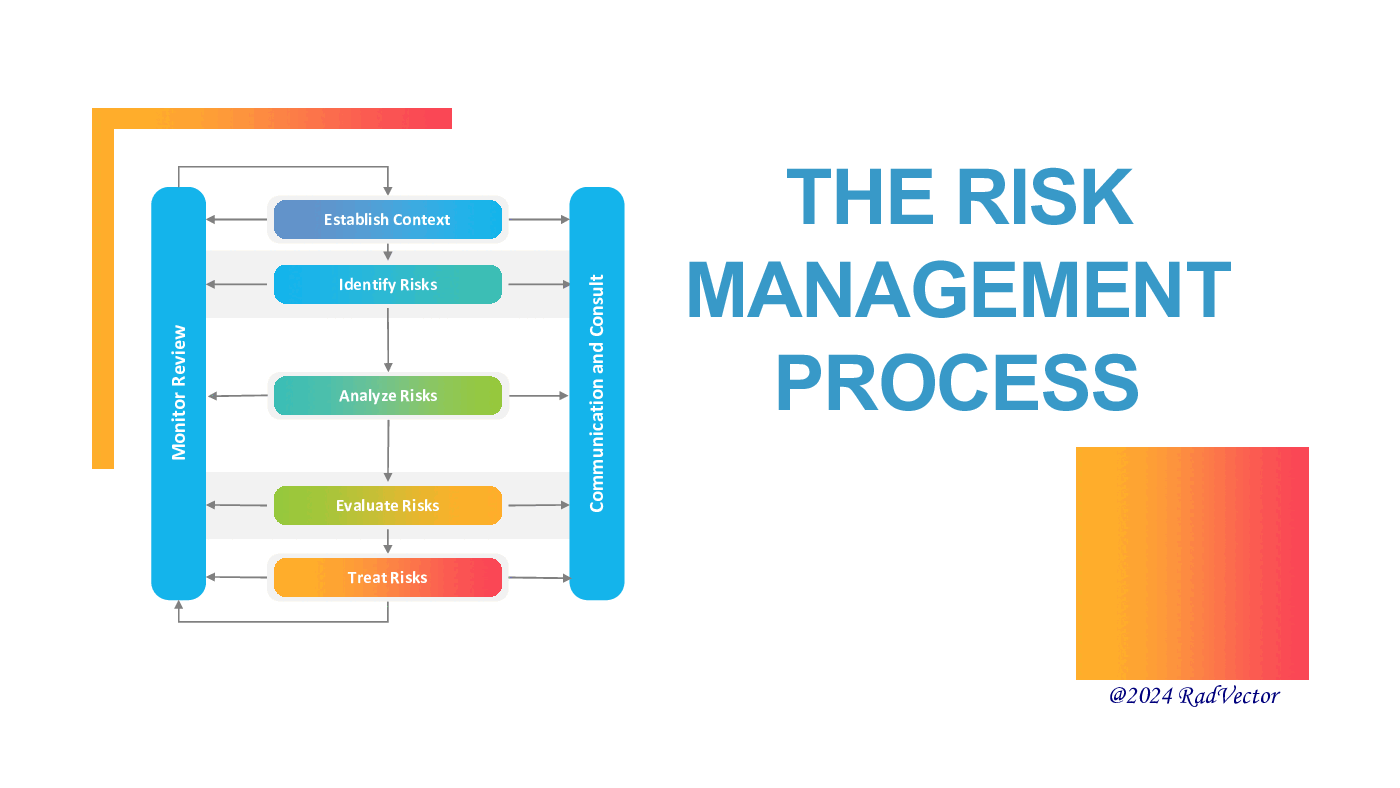
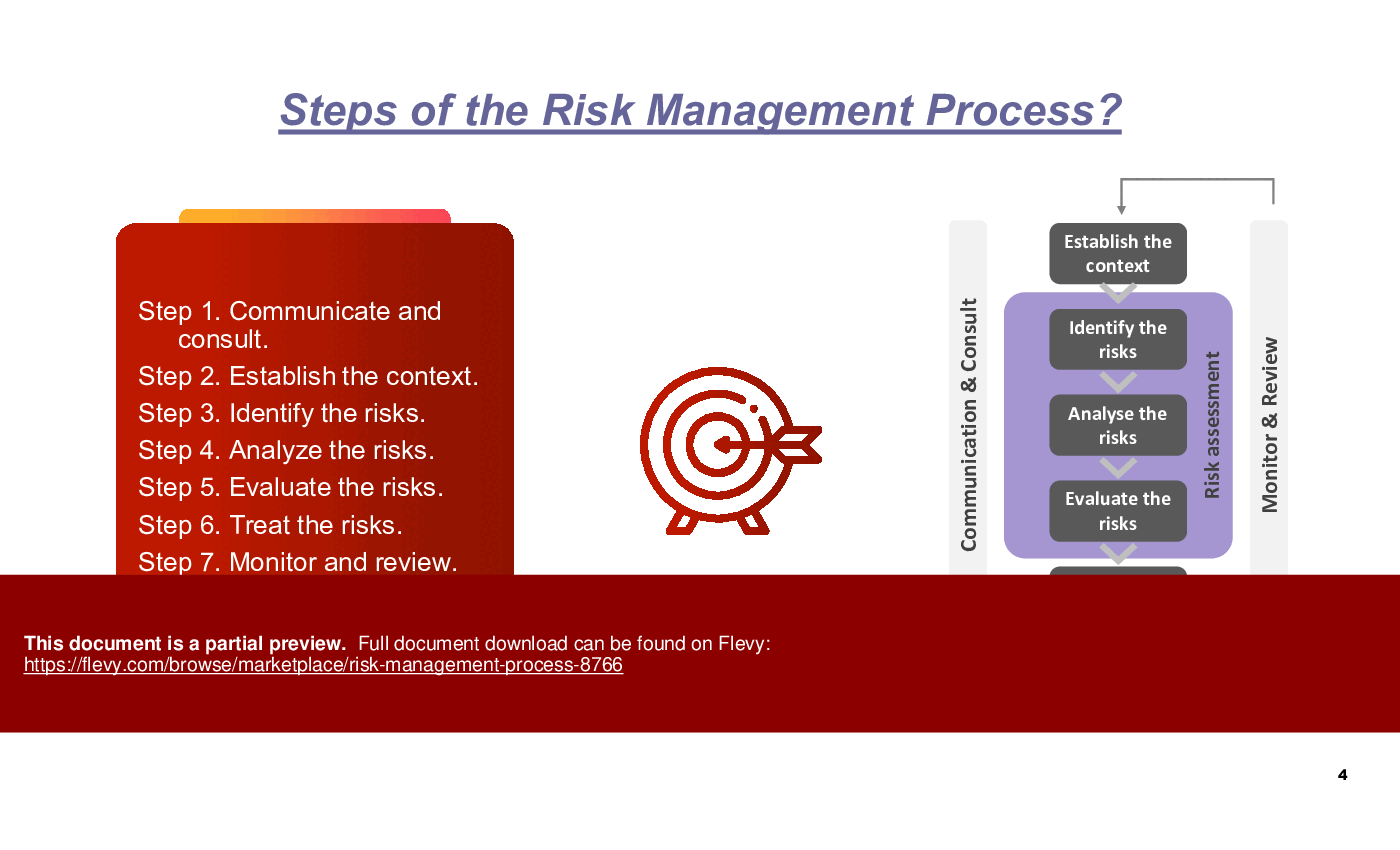
Risk management is a vital process for organizations to identify, assess, and mitigate potential risks that could impact their objectives. The seven steps to risk management provide a structured approach to effectively manage risks and safeguard organizational assets.
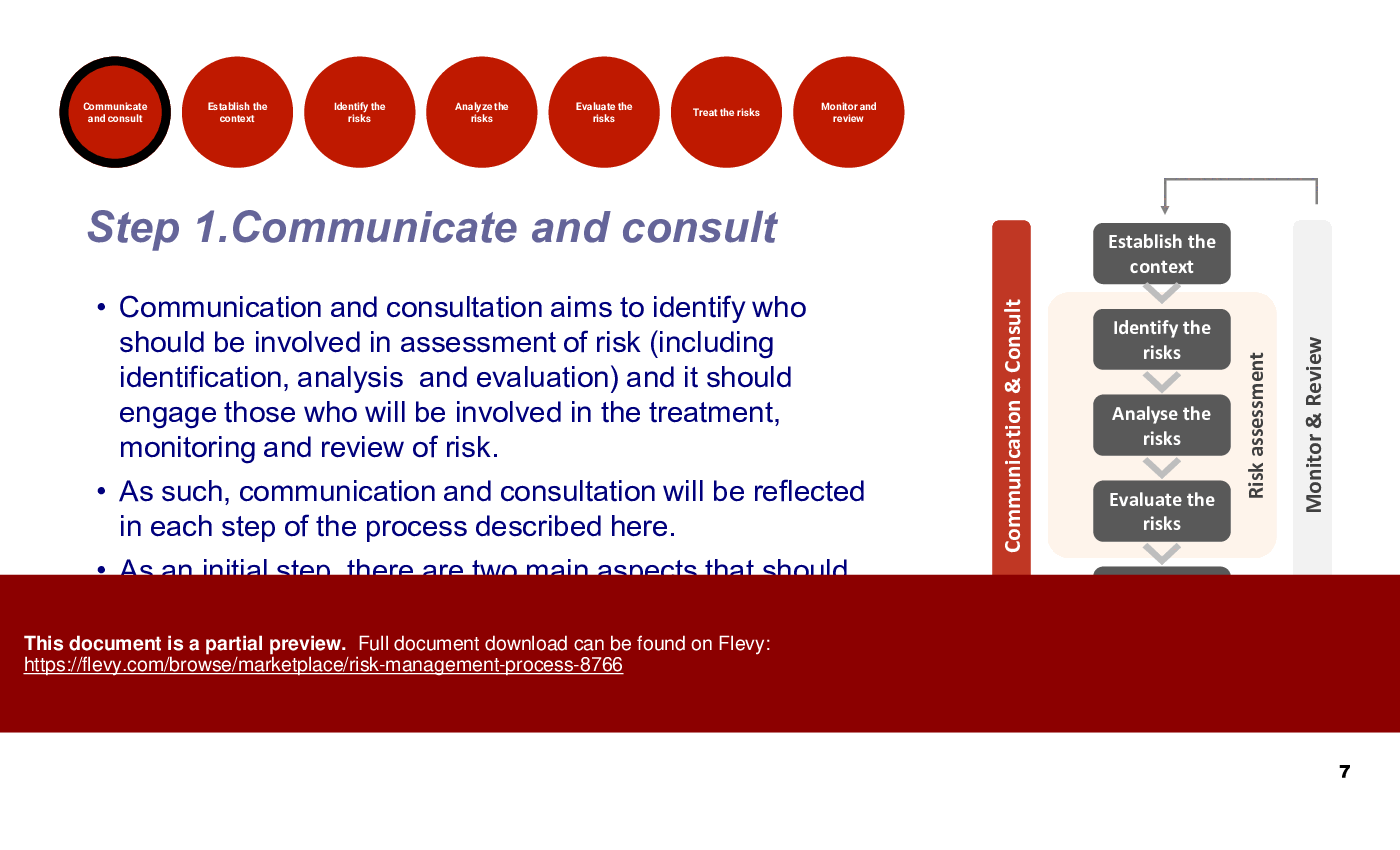
Step 1: Communication & Consultation
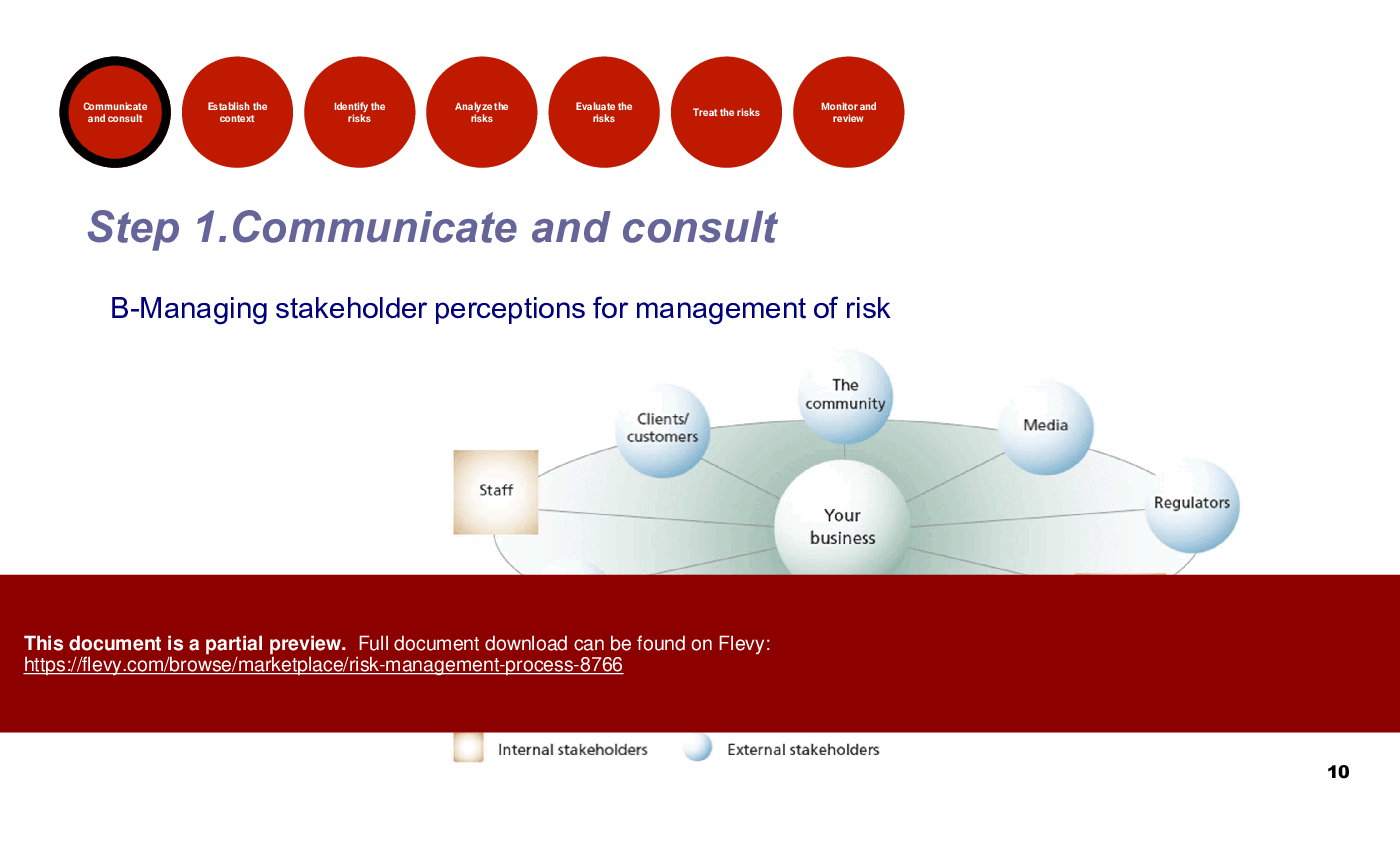
Effective communication is essential to ensure that all relevant stakeholders are engaged in the risk management process. By communicating the importance of risk management and consulting with stakeholders, organizations can gather valuable insights and perspectives to inform risk management decisions.
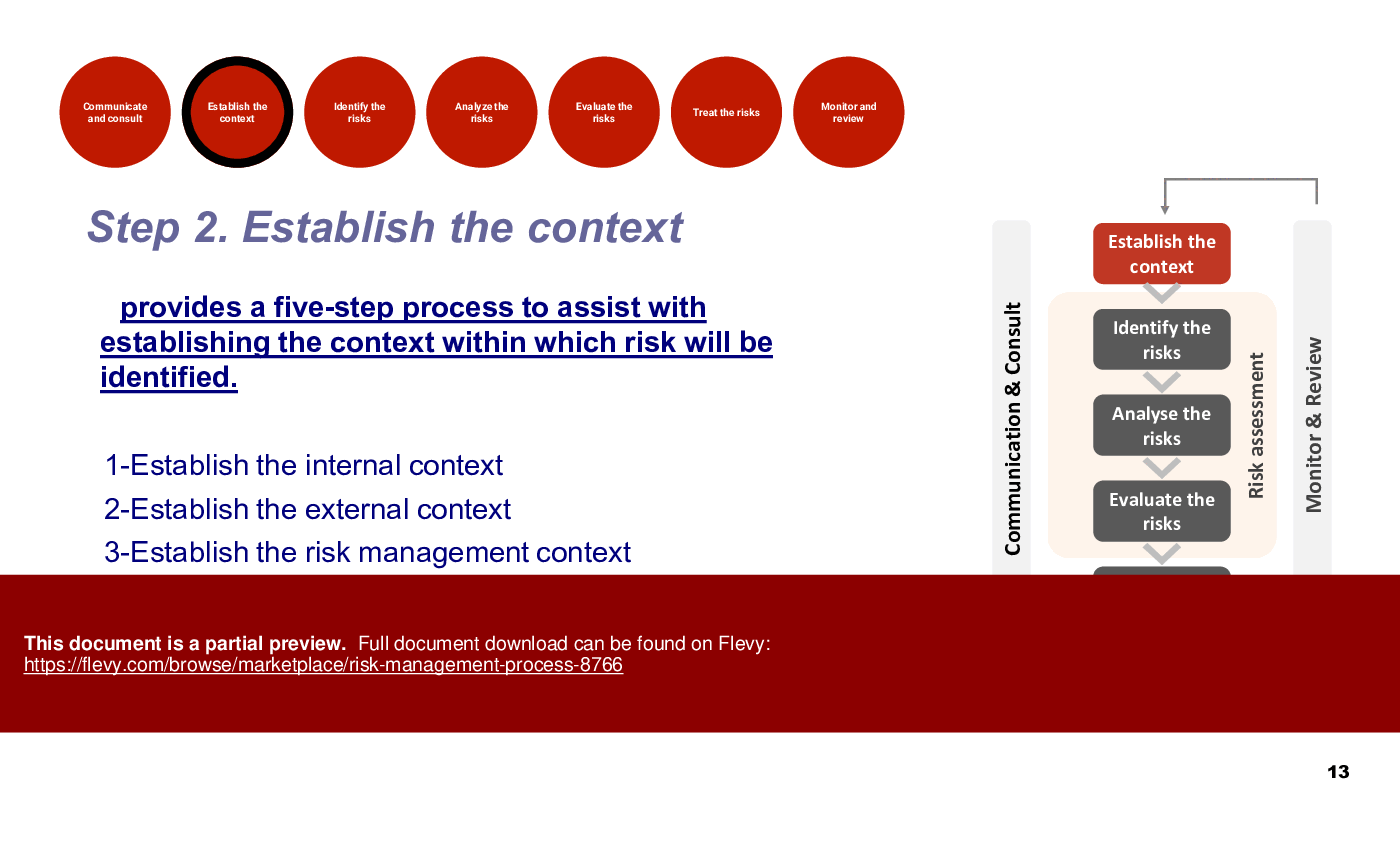
Step 2: Establish Context
Before undertaking risk management activities, it is crucial to establish the business context by clearly articulating the objectives that the organization seeks to achieve. This step helps align risk management efforts with the strategic goals and priorities of the organization.
Step 3: Risk Identification
The process of risk identification involves identifying potential risks that could affect the achievement of organizational objectives. This step may include brainstorming sessions, risk registers, and other techniques to systematically identify and document risks.
Step 4: Risk Assessment
Once risks are identified, they are assessed to determine their likelihood and potential impact on the organization. Risk assessment helps prioritize risks based on their significance and allows organizations to focus resources on addressing the most critical risks.
Step 5: Risk Evaluation
After assessing risks, they are evaluated to determine the need for treatment. This step involves comparing the assessed risks against established criteria to determine whether they are acceptable or require further action.
Step 6: Treat Risks
Based on the output of risk evaluation, risk treatment measures are determined to mitigate the identified threats. Risk treatment options may include risk avoidance, risk reduction, risk transfer, or risk acceptance, depending on the nature and severity of the risks.
Step 7: Monitor & Review
The final step in the risk management process involves monitoring the effectiveness of risk treatment measures and reviewing the overall performance of the risk management program. This step includes measuring risk performance, providing periodic reports to stakeholders, and making adjustments to risk treatment strategies as needed.
By following these seven steps to risk management, organizations can effectively identify, assess, and mitigate risks to achieve their objectives and enhance overall resilience and success.
The comprehensive framework outlined in this PPT equips organizations with the tools to navigate the complexities of risk management. With practical templates and strategies, it empowers decision-makers to proactively address risks and enhance organizational resilience.
Got a question about the product? Email us at support@flevy.com or ask the author directly by using the "Ask the Author a Question" form. If you cannot view the preview above this document description, go here to view the large preview instead.
MARCUS OVERVIEW
This synopsis was written by Marcus [?] based on the analysis of the full 65-slide presentation.
Executive Summary
The Risk Management Process presentation provides a structured approach to identifying, assessing, and mitigating risks within an organization. Developed by a team of security experts with extensive consulting experience, this presentation outlines a series of sequential steps that enable continual improvement in decision-making. By following this process, corporate executives and consultants can effectively manage risks, ensuring that organizational objectives are met while minimizing potential threats.
Who This Is For and When to Use
• Risk Management Officers responsible for overseeing risk mitigation strategies
• Project Managers seeking to identify and manage potential project risks
• Corporate Executives aiming to enhance decision-making through risk assessment
• Compliance Officers ensuring adherence to regulatory requirements
Best-fit moments to use this deck:
• During the initiation phase of a new project to identify potential risks
• In strategic planning sessions to align risk management with organizational objectives
• When conducting annual risk assessments to update risk management strategies
Learning Objectives
• Define the key steps in the risk management process
• Establish the context for effective risk identification and analysis
• Identify and categorize risks impacting organizational objectives
• Analyze risks to determine their likelihood and potential impact
• Evaluate risks against established criteria to prioritize management actions
• Treat identified risks using appropriate mitigation strategies
• Monitor and review risk management effectiveness over time
Table of Contents
• Introduction to Risk Management Process (page 3)
• Steps of the Risk Management Process (page 4)
• Communication and Consultation (page 5)
• Establishing Context (page 13)
• Identifying Risks (page 25)
• Analyzing Risks (page 33)
• Evaluating Risks (page 39)
• Treating Risks (page 42)
• Monitoring and Reviewing (page 46)
Primary Topics Covered
• Communication and Consultation - Engaging stakeholders to gather risk information and manage perceptions is crucial for effective risk management.
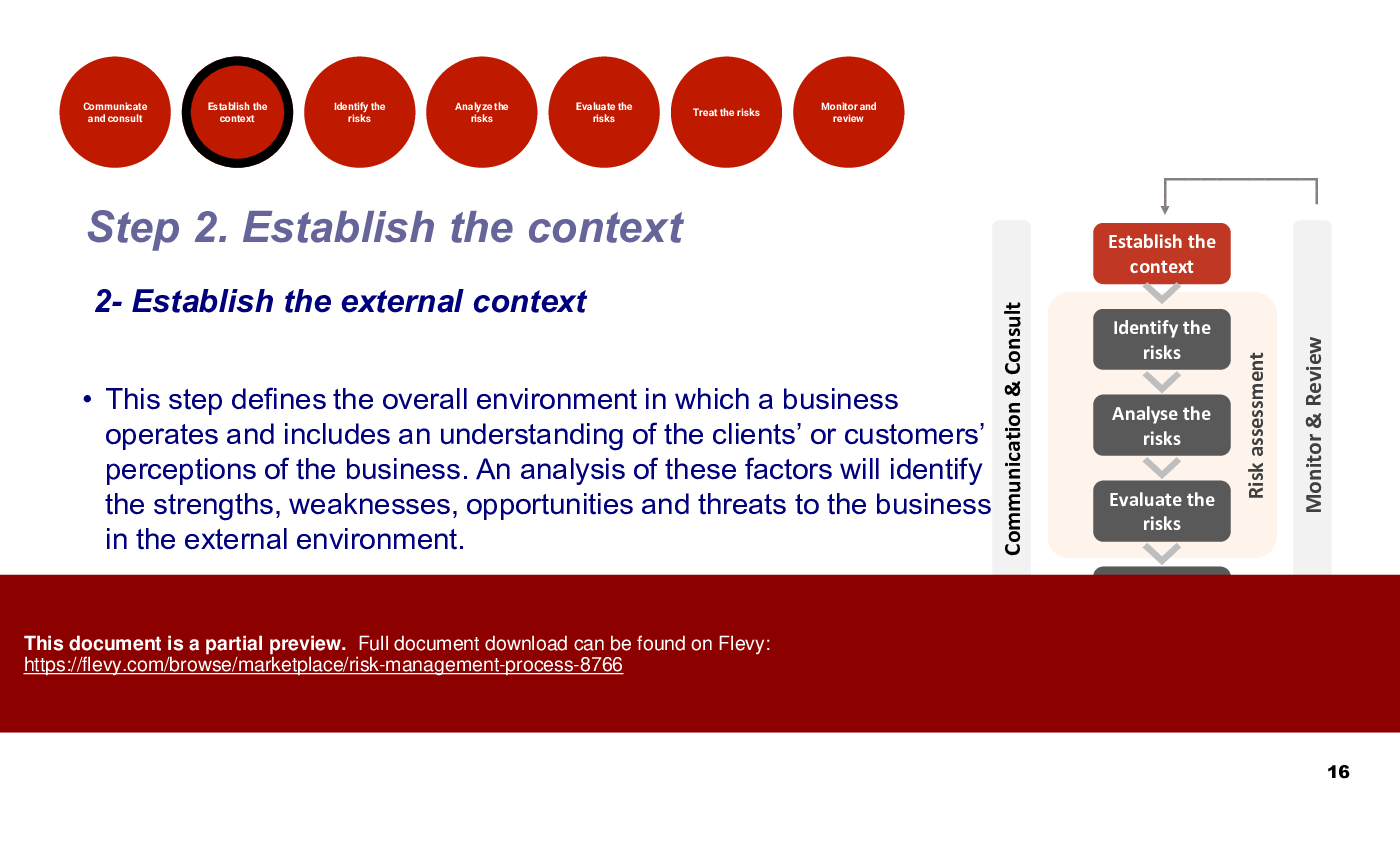
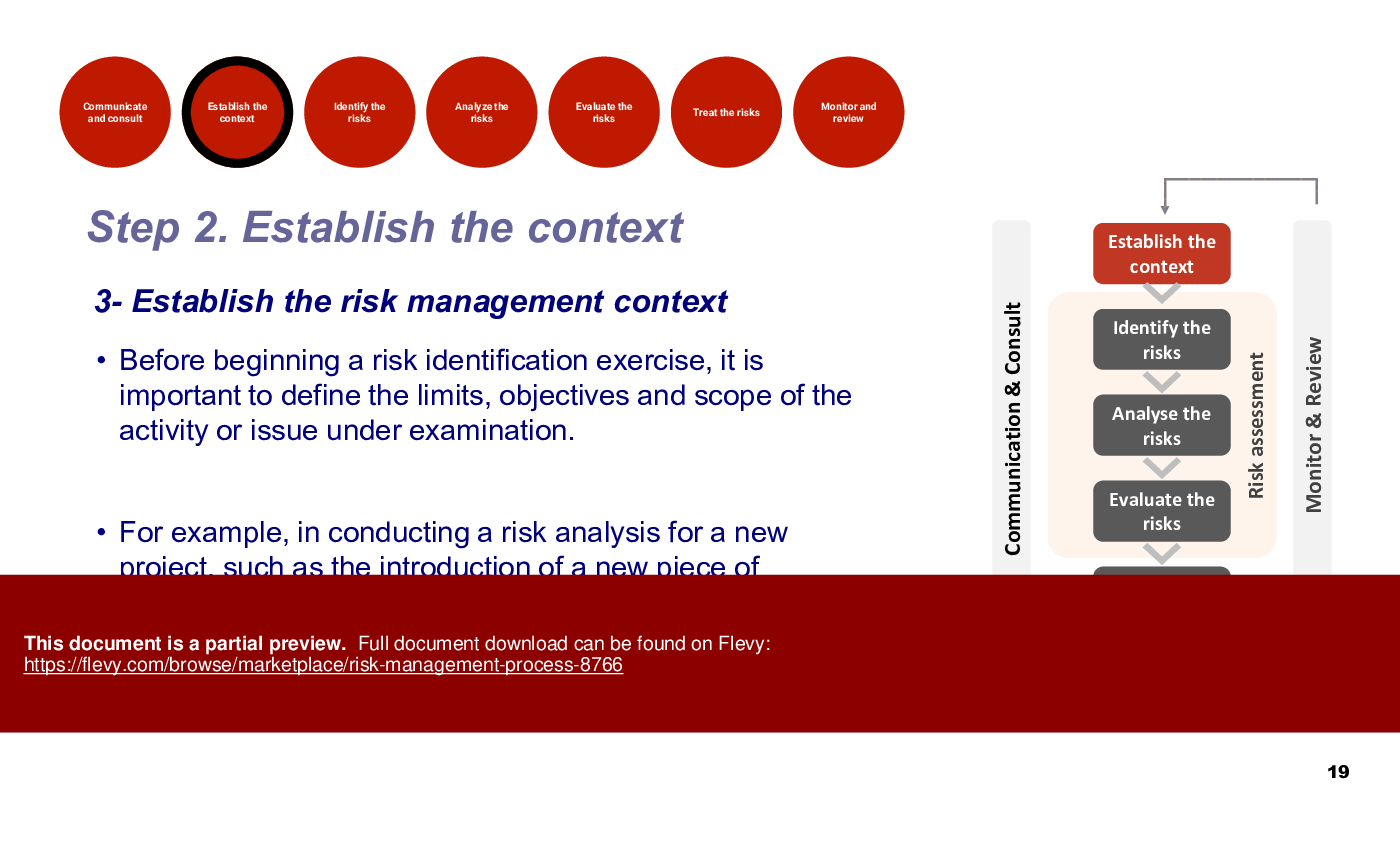
• Establishing Context - Defining internal and external contexts ensures that risk management aligns with organizational objectives and stakeholder expectations.
• Identifying Risks - A systematic approach to uncovering potential risks, both retrospective and prospective, is essential for comprehensive risk management.
• Analyzing Risks - Combining the likelihood of occurrence with potential impacts helps prioritize risks for management.
• Evaluating Risks - Comparing analyzed risks against established criteria determines which risks require treatment and further action.
• Treating Risks - Developing strategies to mitigate unacceptable risks, including avoidance, reduction, sharing, or acceptance.
• Monitoring and Reviewing - Regularly assessing risk management effectiveness ensures that new risks are identified and managed appropriately.
Deliverables, Templates, and Tools
• Risk management plan template for documenting identified risks and mitigation strategies
• Risk assessment framework for evaluating likelihood and impact
• Communication strategy template for stakeholder engagement
• Risk register for tracking identified risks and their status
• Monitoring and review checklist to ensure ongoing effectiveness of risk management processes
Slide Highlights
• Overview of the Risk Management Process illustrating the sequential steps involved
• Detailed breakdown of the Communication and Consultation step emphasizing stakeholder engagement
• Visual representation of the Impact-Probability Matrix for assessing risk severity
• Flowchart outlining the steps for identifying and analyzing risks
• Summary slide encapsulating key takeaways from the risk management process
Potential Workshop Agenda
Risk Management Overview Session (90 minutes)
• Introduce the risk management process and its importance
• Discuss the steps involved in effective risk management
• Engage participants in identifying risks relevant to their projects
Risk Analysis and Evaluation Workshop (60 minutes)
• Analyze identified risks using the Impact-Probability Matrix
• Prioritize risks based on evaluation criteria
• Develop action plans for high-priority risks
Risk Treatment Strategy Session (90 minutes)
• Brainstorm risk treatment options for prioritized risks
• Develop a comprehensive risk management plan
• Establish monitoring and review processes for ongoing risk management
Customization Guidance
• Tailor the risk management plan template to reflect specific organizational contexts and objectives
• Adjust the communication strategy based on stakeholder needs and project complexity
• Incorporate organizational terminology and frameworks into the risk assessment and evaluation processes
Secondary Topics Covered
• Risk acceptance criteria and decision-making frameworks
• Techniques for stakeholder engagement and communication
• Methods for continuous improvement in risk management practices
• Regulatory compliance considerations in risk management
Topic FAQ
What are the typical phases of a risk management process?
Standard frameworks organize risk work into sequential steps: Communication & Consultation; Establishing Context; Risk Identification; Risk Assessment/Analysis; Risk Evaluation; Risk Treatment; and Monitoring & Review. The Risk Management Process presentation explicitly lays out these 7 steps, ending with Monitor & Review as the final phase.How do you use an Impact-Probability Matrix to prioritize risks?
An Impact-Probability Matrix plots each identified risk by its likelihood and potential impact to assess severity and prioritize responses. After mapping risks, teams focus treatment on high-impact, high-likelihood items and document decisions in a risk register, using the matrix during the Analyze Risks step.What should be included in a risk register?
A risk register typically records each identified risk, its description, owner, likelihood, impact, current mitigation actions, status, and residual risk. The Risk Management Process deck includes a risk register template designed to track identified risks and their mitigation strategies across the assessment and treatment lifecycle.How often should organizations review their risk management plans?
Risk management plans should be reviewed periodically to remain relevant and effective; the materials recommend regular monitoring and suggest reviewing plans at least annually, with ongoing tracking of risk treatment effectiveness and periodic reports to stakeholders.What should I look for when choosing a risk management toolkit for my team?
Select a toolkit that supports the full process: stakeholder communication templates, a risk management plan, a risk assessment framework or Impact-Probability Matrix, a risk register for tracking, and monitoring/checklist tools. The Risk Management Process product on Flevy provides these 5 core templates and tools.What is the role of stakeholder communication in risk management?
Communication and Consultation gathers insights, surfaces prospective and retrospective risks, and manages stakeholder perceptions to inform decisions. Effective stakeholder engagement is positioned as a foundational step in the process to ensure identified risks and mitigation choices reflect stakeholder expectations and available information in the Communication and Consultation step.I’m leading a post-merger integration—which risk steps should I prioritize first?
In a post-merger context prioritize Establishing Context to align objectives and stakeholder expectations, then Risk Identification to capture integration-specific threats, followed by Analysis and Evaluation to prioritize responses. The Risk Management Process deck frames those initial priorities within its seven-step sequence.What treatment strategies can organizations use for unacceptable risks?
Common risk treatment options are risk avoidance, risk reduction (mitigation), risk sharing or transfer (e.g., insurance or outsourcing), and risk acceptance when within tolerance. These options are described as part of the Treat Risks step and form the basis for a documented risk treatment plan.Document FAQ
These are questions addressed within this presentation.
What is the Risk Management Process?
The Risk Management Process consists of a series of steps that enable organizations to identify, assess, and mitigate risks effectively, ensuring alignment with business objectives.
Why is communication important in risk management?
Effective communication engages stakeholders, gathers essential risk information, and manages perceptions, which is vital for successful risk management.
How do we identify risks?
Risks can be identified through retrospective analysis of past incidents, prospective brainstorming sessions, and stakeholder consultations.
What is the Impact-Probability Matrix?
The Impact-Probability Matrix is a tool used to assess the severity of risks by evaluating their likelihood of occurrence against potential impacts.
What strategies can be used to treat risks?
Risk treatment strategies include avoiding the risk, reducing its likelihood or impact, sharing the risk, or accepting it based on established criteria.
How often should risk management plans be reviewed?
Risk management plans should be reviewed periodically, ideally at least annually, to ensure they remain relevant and effective.
What is the significance of establishing context in risk management?
Establishing context ensures that risk management aligns with organizational goals and stakeholder expectations, providing a framework for effective decision-making.
How can we monitor and review risks effectively?
Regular monitoring involves tracking identified risks, assessing the effectiveness of treatment strategies, and updating the risk management plan as necessary.
Glossary
• Risk Management - The process of identifying, assessing, and controlling threats to an organization's capital and earnings.
• Stakeholder - An individual or group that has an interest in the outcome of a project or process.
• Risk Assessment - The systematic process of evaluating potential risks that may be involved in a projected activity or undertaking.
• Mitigation - Actions taken to reduce the severity or likelihood of a risk.
• Impact-Probability Matrix - A tool used to evaluate the severity of risks based on their likelihood and potential impact.
• Risk Register - A document used to track identified risks, their status, and mitigation strategies.
• Communication Strategy - A plan for how information will be shared with stakeholders throughout the risk management process.
• Monitoring and Review - The ongoing process of tracking risks and evaluating the effectiveness of risk management strategies.
• Risk Criteria - Standards used to evaluate the significance of risks and determine acceptable levels of risk.
• Prospective Risks - Risks that have not yet occurred, but may happen in the future.
• Retrospective Risks - Risks that have previously occurred and can be analyzed for future reference.
• Risk Treatment Plan - A detailed plan outlining how identified risks will be managed or mitigated.
• Compliance - Adherence to laws, regulations, and guidelines relevant to the organization’s operations.
• Stakeholder Engagement - The process of involving individuals or groups in decision-making related to risk management.
• Continuous Improvement - Ongoing efforts to enhance risk management practices and processes.
• Risk Tolerance - The level of risk that an organization is willing to accept in pursuit of its objectives.
• Risk Transfer - Shifting the risk to a third party, often through insurance or outsourcing.
• Residual Risk - The level of risk remaining after risk treatment measures have been applied.
• Inherent Risk - The level of risk that exists in the absence of any controls or mitigation strategies.
Source: Best Practices in Risk Management PowerPoint Slides: Risk Management Process PowerPoint (PPTX) Presentation Slide Deck, RadVector Consulting