OAuth 2.0 - Demystified (PowerPoint PPTX Slide Deck)
PowerPoint (PPTX) 112 Slides
CYBER SECURITY PPT DESCRIPTION
OAuth 2.0 is an open standard for access delegation, commonly used to grant websites or applications limited access to a user's information without exposing their credentials. It is designed to work specifically with Hypertext Transfer Protocol (HTTP) and provides specific authorization flows for web applications, desktop applications, mobile phones, and living room devices.
Key Concepts of OAuth 2.0
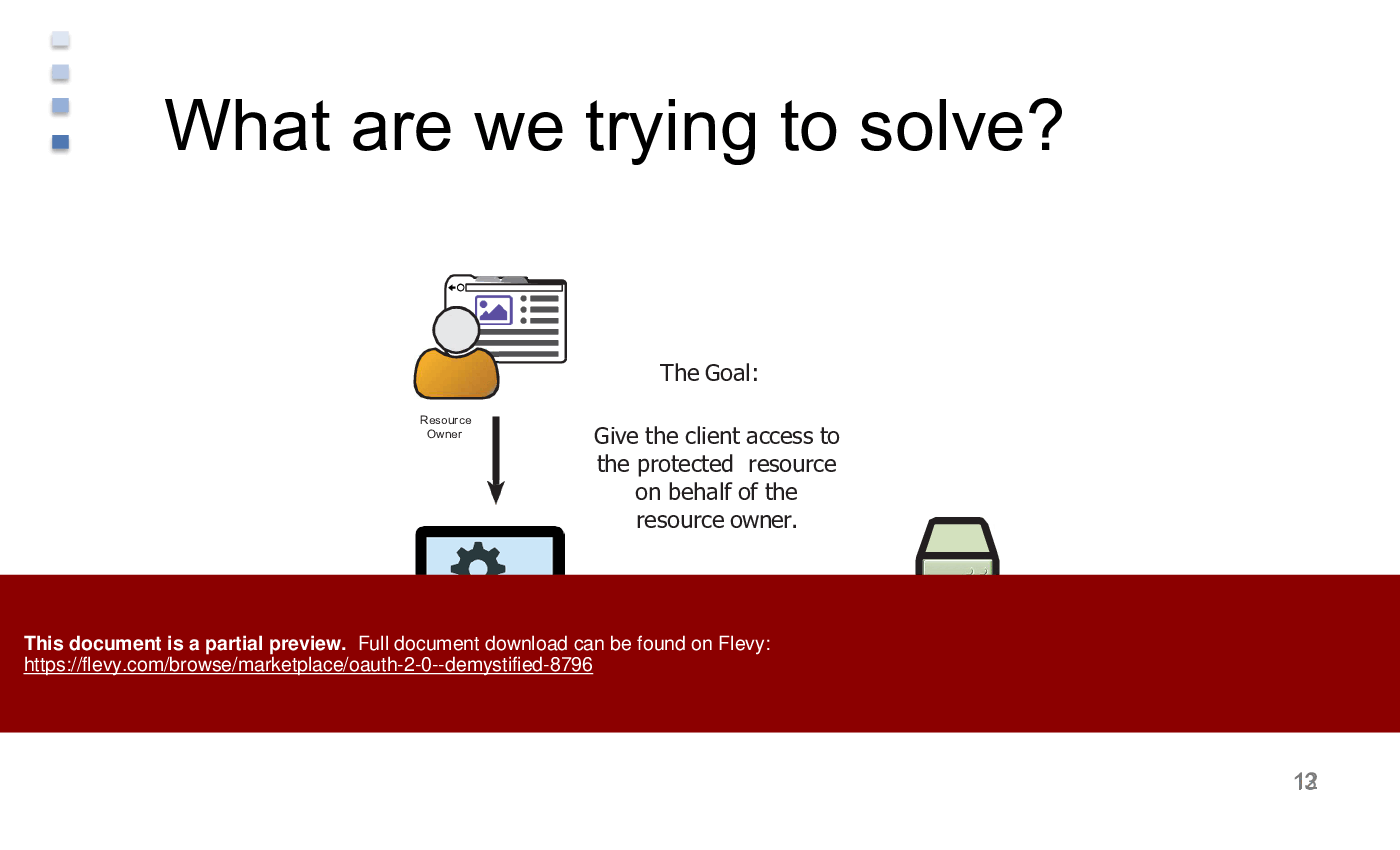
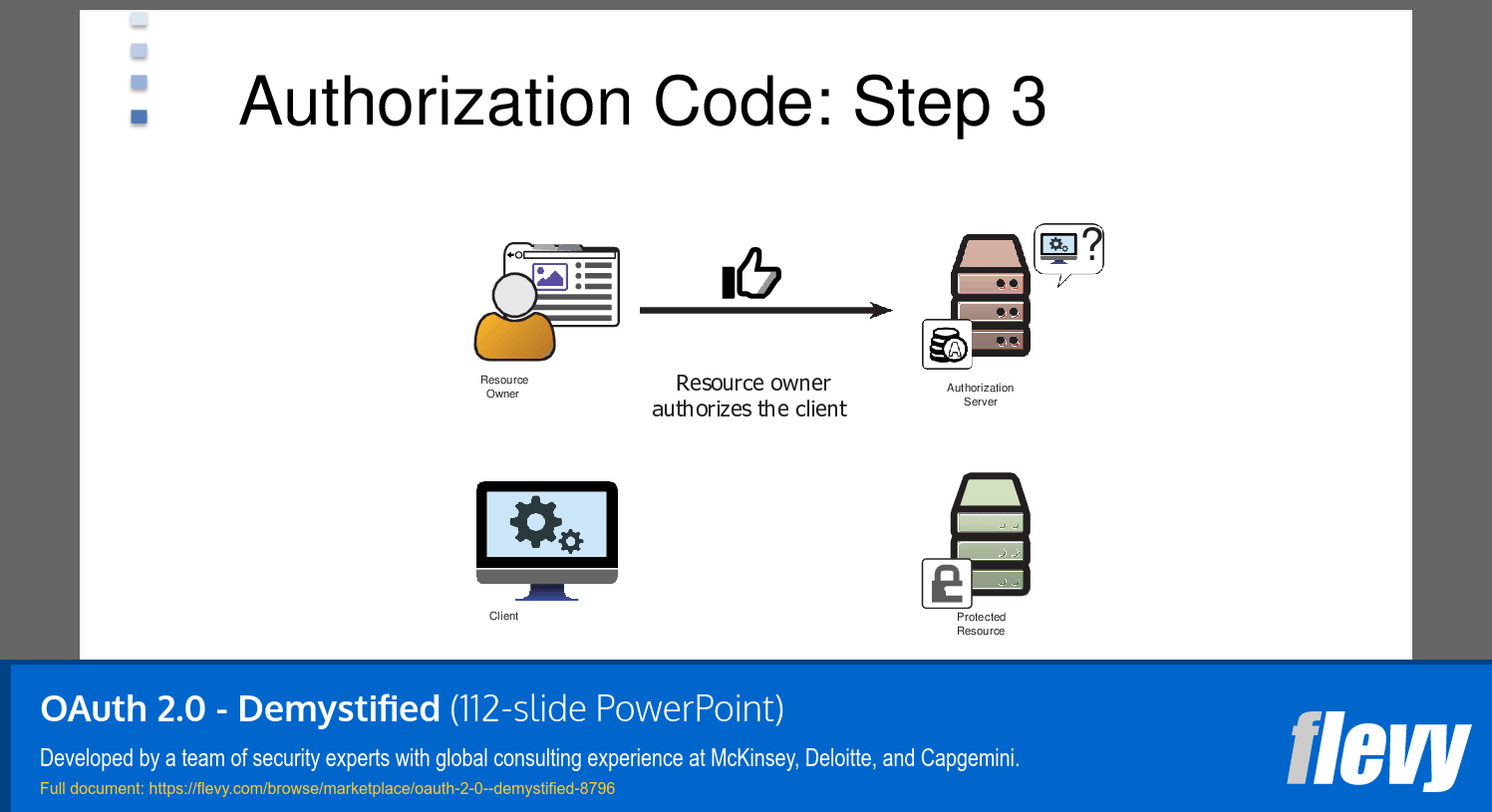
1. Resource Owner: The user who authorizes an application to access their account.
2. Client: The application requesting access to the user's account.
3. Resource Server: The server hosting the protected resources, capable of accepting and responding to protected resource requests using access tokens.
4. Authorization Server: The server issuing access tokens to the client after successfully authenticating the resource owner and obtaining authorization.
OAuth 2.0 Flow
OAuth 2.0 defines four primary grant types (authorization flows) to serve different use cases:
1. Authorization Code Grant: Used by web and mobile apps, where the client's server can securely interact with the authorization server.
2. Implicit Grant: Suitable for browser-based applications where the access token is returned directly to the client.
3. Resource Owner Password Credentials Grant: When the user's credentials are trusted by the client.
4. Client Credentials Grant: Used for server-to-server interactions.
OAuth 2.0 in Salesforce
Salesforce leverages OAuth 2.0 for secure data sharing across applications and for third-party integrations. It provides a secure way to access Salesforce APIs.
1. Setting Up OAuth in Salesforce:
• Navigate to Setup and create a new Connected App.
• Define the OAuth settings by specifying the callback URL and selecting OAuth scopes, which dictate the level of access granted.
• Salesforce provides a consumer key and consumer secret, which the client application uses to identify itself.
2. OAuth Flow in Salesforce:
• Authorization Code Grant: Commonly used in Salesforce, where the client directs the user to Salesforce's authorization endpoint. Upon successful login, Salesforce redirects back with an authorization code.
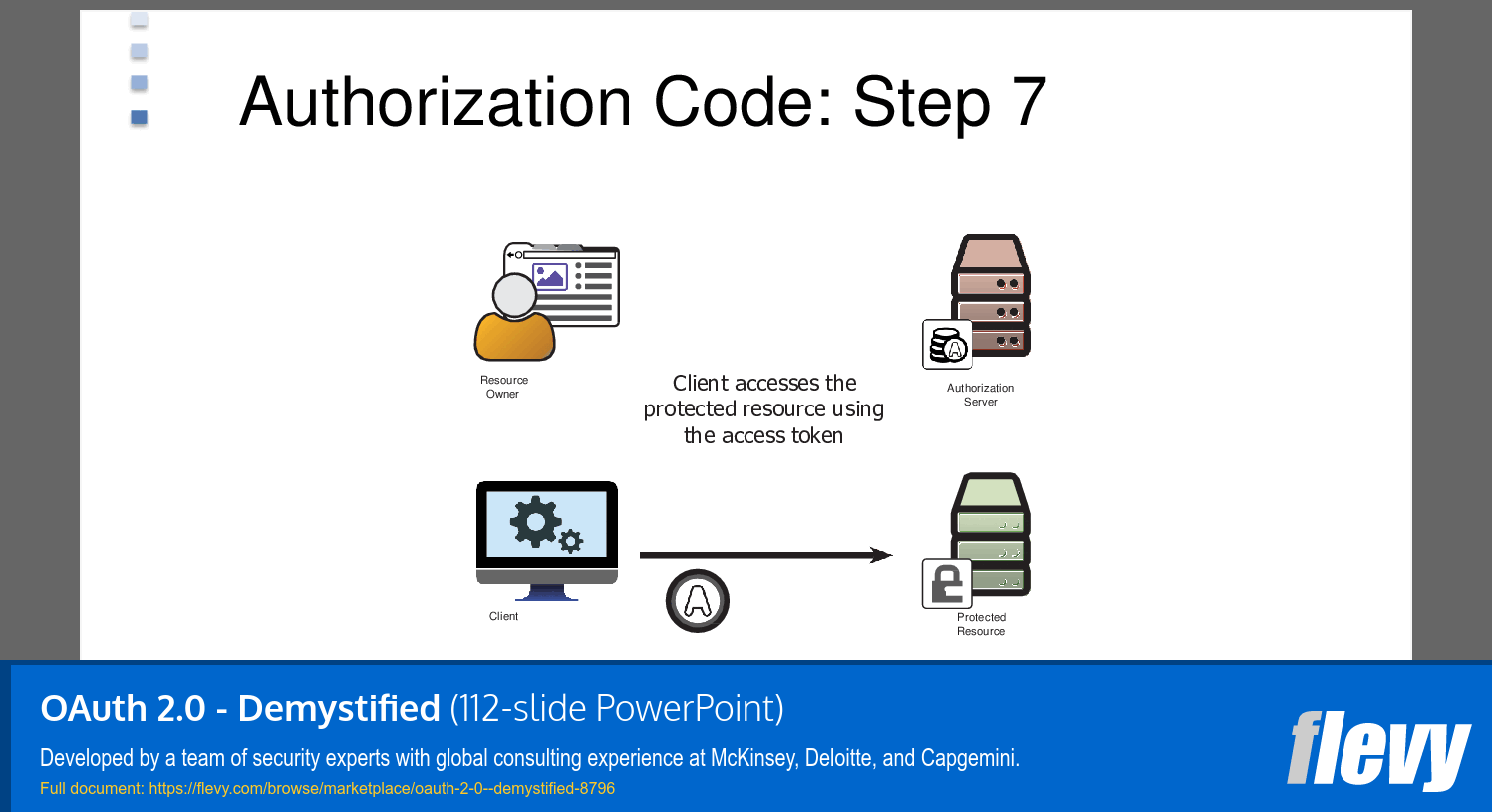
• The client application exchanges this authorization code for an access token by making a request to Salesforce's token endpoint.
• With the access token, the client application can access Salesforce resources on behalf of the user.
3. Use Cases:
• Integrating third-party applications like Slack, Google Apps, or custom applications with Salesforce.
• Enabling mobile applications to securely access Salesforce data.
• Allowing secure API access for automation scripts or backend services.
Overall, OAuth 2.0 provides a robust framework for secure authorization, and its implementation in Salesforce enhances secure integrations and resource access management.
Got a question about the product? Email us at support@flevy.com or ask the author directly by using the "Ask the Author a Question" form. If you cannot view the preview above this document description, go here to view the large preview instead.
Source: Best Practices in Cyber Security PowerPoint Slides: OAuth 2.0 - Demystified PowerPoint (PPTX) Presentation Slide Deck, RadVector Consulting