Security Operations Center (SOC) Toolkit (PowerPoint PPTX Slide Deck)
PowerPoint (PPTX) 206 Slides
BENEFITS OF THIS POWERPOINT DOCUMENT
- Equips organizations with comprehensive knowledge and strategies for establishing and operating a robust Security Operations Center (SOC).
- Guides businesses in navigating complex cybersecurity challenges, from compliance requirements such as HIPAA and GDPR to understanding and mitigating various types of cyber attacks.
- Empowers organizations to elevate their cybersecurity posture through the implementation of SOC best practices, effective incident management, and continuous performance measurement using KPIs and metrics.
CYBER SECURITY PPT DESCRIPTION
Curated by McKinsey-trained Executives
Elevate Your Security Game: The Ultimate Security Operations Center Business Toolkit
In today's digital landscape, cybersecurity is not just a buzzword; it's a critical necessity for businesses of all sizes. As cyber threats continue to evolve in complexity and frequency, organizations must equip themselves with robust defense mechanisms to safeguard their sensitive data and operations. Enter the Security Operations Center (SOC) – the nerve center of cybersecurity operations. However, building and managing an effective SOC requires more than just technology; it demands comprehensive knowledge, strategic planning, and meticulous execution.
CONTENT OVERVIEW
• Introduction to Cybersecurity
• Fundamentals of Cybersecurity
• Risk Management in Cybersecurity
• HIPAA Compliance
• GDPR Compliance
• Implementing Cybersecurity Policies
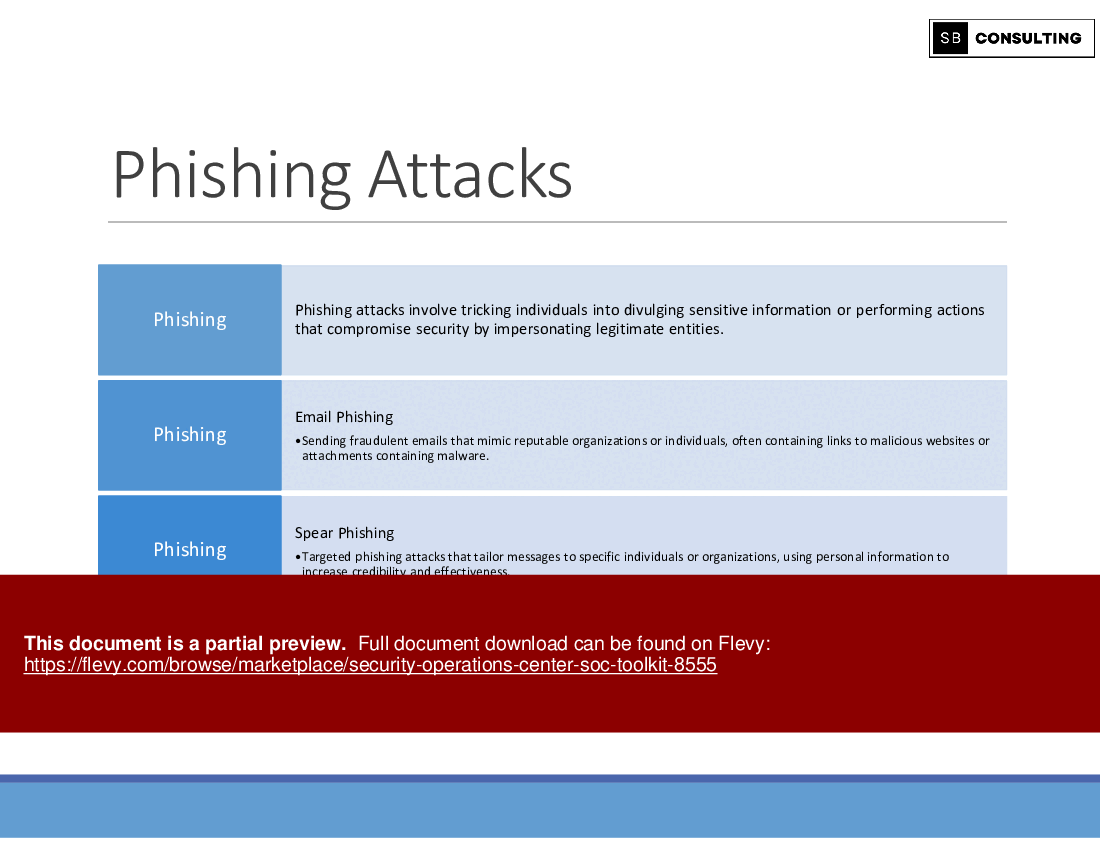
• Understanding Cyber Attacks
• Types of Cyber Attacks
• Backup and Recovery Structures
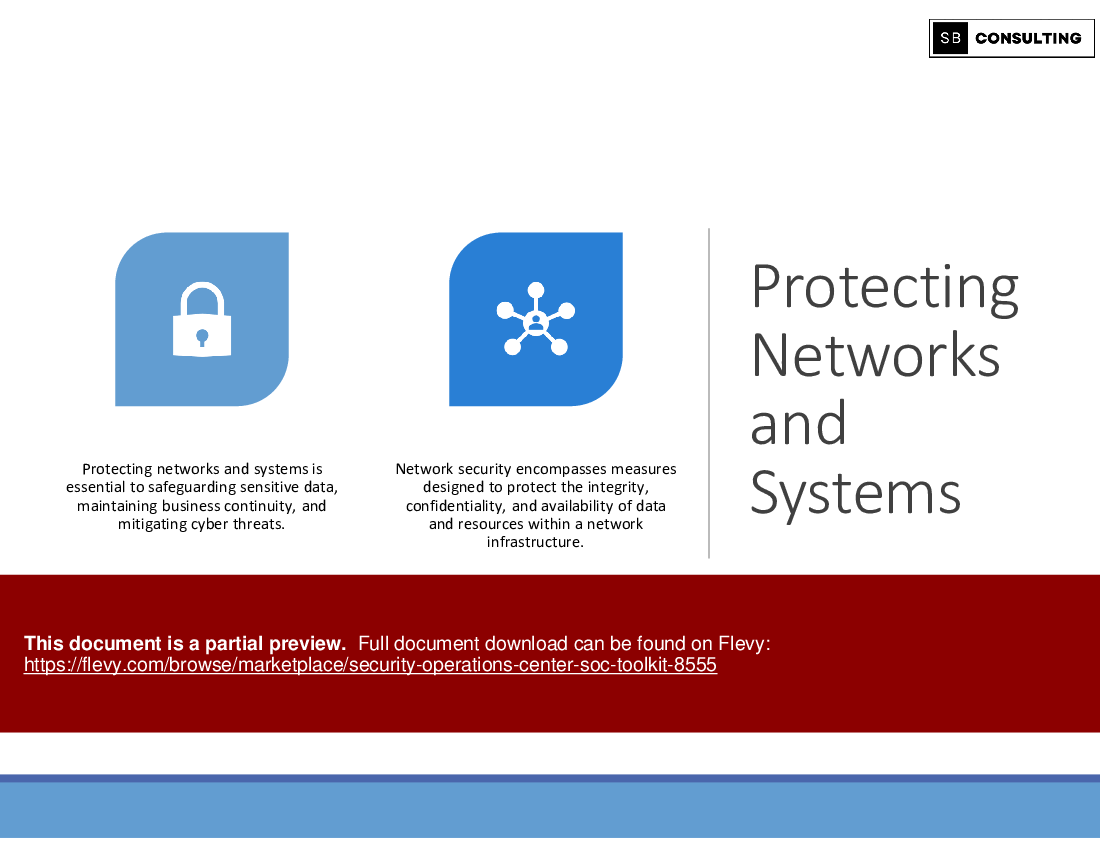
• Cloud Security
• ISO/IEC 27001 Compliance
• Definition of Security Operations Center (SOC)
• Why Businesses Need a SOC
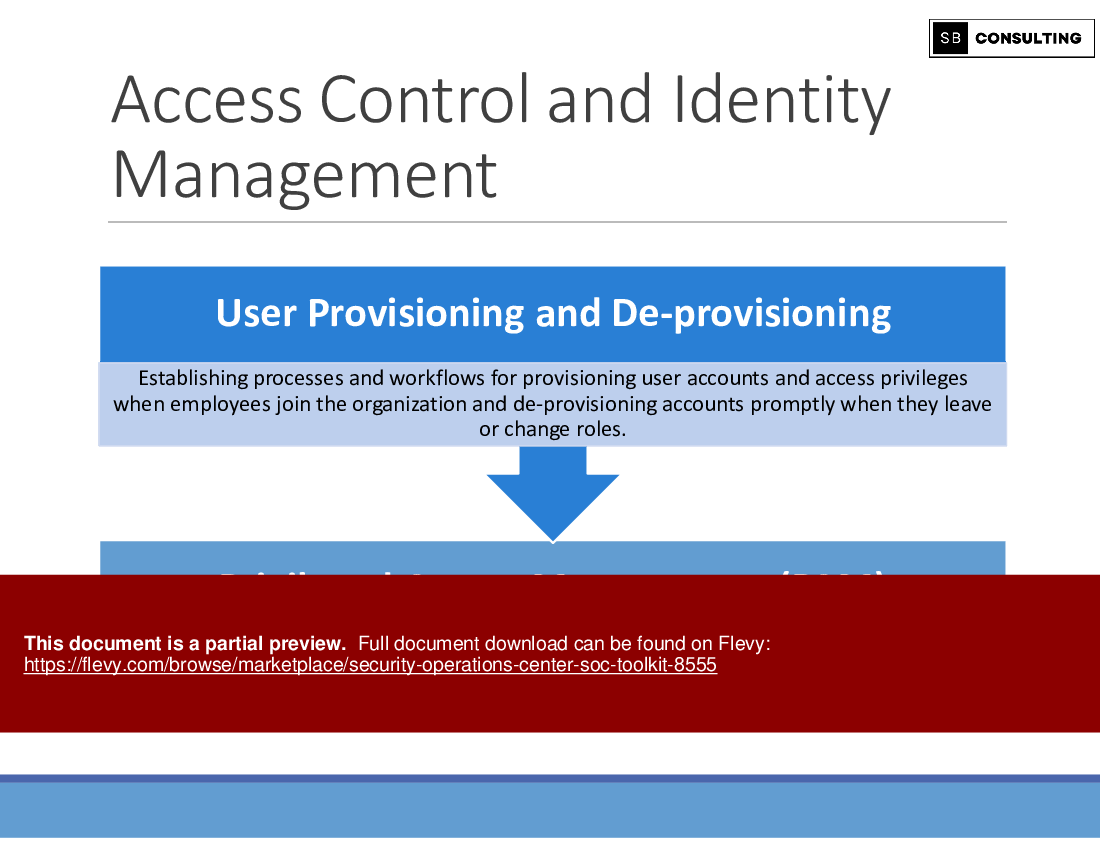
• Vulnerability Management
• How Security Operations Centers Work
• In-house SOC
• Hybrid SOC
• Dedicated SOC
• Outsourced SOC
• SOC Roles and Responsibilities
• Benefits of Security Operations Centers
• Incident Management
• SOC Challenges
• Implementing a SOC
• Building a SOC Team
• Developing a SOC Strategy
• SOC Automation
• Outsourcing a SOC
• SOC Best Practices
• SOC Key Performance Indicators (KPIs) and Metrics
• SOC Checklists
LEARNING OBJECTIVES
Learning Objective 1: Mastering the Fundamentals of Cybersecurity
Our toolkit begins with an in-depth exploration of cybersecurity fundamentals. From understanding the anatomy of cyber threats to grasping the principles of risk management, this section provides a solid foundation for cybersecurity novices and seasoned professionals alike.
Learning Objective 2: Compliance Demystified – HIPAA and GDPR
Navigating the regulatory landscape is essential for businesses handling sensitive data. Our toolkit demystifies two critical compliance frameworks – HIPAA and GDPR – providing clear guidelines on how to ensure your organization remains compliant while fortifying its cybersecurity posture.
Learning Objective 3: Crafting Effective Cybersecurity Policies
Policies serve as the backbone of any cybersecurity strategy. Learn the art of crafting comprehensive cybersecurity policies tailored to your organization's unique needs, covering everything from data protection to incident response protocols.
Learning Objective 4: Understanding the Anatomy of Cyber Attacks
To defend against cyber threats effectively, one must first understand how they operate. Our toolkit delves into the various types of cyber attacks, from phishing and malware to DDoS attacks, equipping you with the knowledge needed to detect and mitigate threats proactively.
Learning Objective 5: Building Resilience with Backup and Recovery Structures
Data loss can cripple businesses, making robust backup and recovery structures indispensable. Explore best practices for designing resilient backup solutions to ensure business continuity in the face of cyber incidents.
Learning Objective 6: Securing the Cloud – Best Practices
As organizations increasingly migrate to cloud environments, securing cloud infrastructure becomes paramount. Discover proven strategies and best practices for safeguarding your cloud assets from cyber threats.
Learning Objective 7: Achieving ISO/IEC 27001 Compliance
ISO/IEC 27001 certification demonstrates your commitment to information security excellence. Our toolkit provides practical guidance on achieving and maintaining ISO/IEC 27001 compliance, enhancing your organization's credibility and trustworthiness.
Learning Objective 8: Unveiling the Security Operations Center (SOC)
What exactly is a SOC, and why does your business need one? Explore the functions and significance of SOC in today's cybersecurity landscape, gaining insights into its pivotal role in threat detection, incident response, and risk mitigation.
Learning Objective 9: Navigating SOC Models – In-house, Hybrid, Dedicated, and Outsourced
Choosing the right SOC model is crucial for optimizing cybersecurity operations. Compare and contrast different SOC deployment options – from in-house and hybrid models to dedicated and outsourced SOC – to determine the best fit for your organization's needs and resources.
Learning Objective 10: Decoding SOC Roles and Responsibilities
Every SOC relies on a team of skilled professionals to operate effectively. Dive into the diverse roles and responsibilities within a SOC, from SOC analysts and incident responders to SOC managers and threat intelligence experts, understanding how each role contributes to overall cybersecurity resilience.
Learning Objective 11: Maximizing the Benefits of Security Operations Centers
Unlock the myriad benefits that SOC offers, from enhanced threat visibility and rapid incident response to proactive threat hunting and continuous security monitoring. Learn how SOC can elevate your organization's cybersecurity posture and business resilience.
Learning Objective 12: Overcoming SOC Challenges
Despite its many advantages, establishing and operating a SOC comes with its fair share of challenges. Explore common SOC pain points and proven strategies for overcoming them, ensuring smooth SOC operations and sustained cybersecurity effectiveness.
Learning Objective 13: Implementing a SOC – From Strategy to Execution
From laying the groundwork with a comprehensive SOC strategy to executing deployment and operationalization, our toolkit provides a step-by-step guide to implementing a SOC tailored to your organization's specific requirements and objectives.
Learning Objective 14: Building a High-Performing SOC Team
A SOC is only as effective as its team members. Discover strategies for recruiting, training, and retaining top cybersecurity talent, fostering a culture of collaboration, innovation, and continuous learning within your SOC team.
Learning Objective 15: Developing a Robust SOC Strategy
A well-defined SOC strategy serves as a roadmap for achieving cybersecurity excellence. Learn how to develop a strategic SOC roadmap aligned with your organization's risk profile, business objectives, and resource constraints, ensuring long-term success and resilience.
Learning Objective 16: Embracing SOC Automation for Efficiency and Scale
Automation is a game-changer in SOC operations, enabling faster threat detection, response, and remediation. Explore the latest automation technologies and best practices for integrating automation into your SOC workflow, maximizing efficiency and scalability while minimizing human error.
Learning Objective 17: Outsourcing SOC – Pros, Cons, and Best Practices
For organizations lacking the resources or expertise to maintain an in-house SOC, outsourcing can be a viable alternative. Evaluate the pros, cons, and best practices of outsourcing SOC functions to managed security service providers (MSSPs), ensuring a seamless transition and optimal cybersecurity outcomes.
Learning Objective 18: Mastering SOC Best Practices
Drawing on industry-leading practices and real-world case studies, our toolkit distills the essential best practices for SOC operations, incident management, threat hunting, and more, empowering you to elevate your cybersecurity posture and stay ahead of evolving threats.
Learning Objective 19: Measuring SOC Performance with KPIs and Metrics
Effective performance measurement is essential for assessing SOC effectiveness and driving continuous improvement. Learn how to define, track, and analyze key performance indicators (KPIs) and metrics tailored to your SOC's objectives and stakeholders, enabling data-driven decision-making and accountability.
Learning Objective 20: Ensuring Compliance with SOC Checklists
Compliance with industry standards and best practices is non-negotiable in cybersecurity. Leverage our comprehensive SOC checklists to ensure your SOC operations adhere to regulatory requirements, industry standards, and internal policies, minimizing compliance risk and maximizing security effectiveness.
With cyber threats becoming increasingly sophisticated and pervasive, investing in a robust Security Operations Center is no longer optional – it's imperative. Our comprehensive toolkit equips you with the knowledge, strategies, and best practices needed to establish, operate, and optimize a world-class SOC, enabling your organization to stay ahead of threats, safeguard critical assets, and thrive in the digital age. Elevate your security game today with the ultimate Security Operations Center Business Toolkit.
Key Words:
Strategy & Transformation, Growth Strategy, Strategic Planning, Strategy Frameworks, Innovation Management, Pricing Strategy, Core Competencies, Strategy Development, Business Transformation, Marketing Plan Development, Product Strategy, Breakout Strategy, Competitive Advantage, Mission, Vision, Values, Strategy Deployment & Execution, Innovation, Vision Statement, Core Competencies Analysis, Corporate Strategy, Product Launch Strategy, BMI, Blue Ocean Strategy, Breakthrough Strategy, Business Model Innovation, Business Strategy Example, Corporate Transformation, Critical Success Factors, Customer Segmentation, Customer Value Proposition, Distinctive Capabilities, Enterprise Performance Management, KPI, Key Performance Indicators, Market Analysis, Market Entry Example, Market Entry Plan, Market Intelligence, Market Research, Market Segmentation, Market Sizing, Marketing, Michael Porter's Value Chain, Organizational Transformation, Performance Management, Performance Measurement, Platform Strategy, Product Go-to-Market Strategy, Reorganization, Restructuring, SWOT, SWOT Analysis, Service 4.0, Service Strategy, Service Transformation, Strategic Analysis, Strategic Plan Example, Strategy Deployment, Strategy Execution, Strategy Frameworks Compilation, Strategy Methodologies, Strategy Report Example, Value Chain, Value Chain Analysis, Value Innovation, Value Proposition, Vision Statement, Corporate Strategy, Business Development
NOTE:Our digital products are sold on an "as is" basis, making returns and refunds unavailable post-download. Please preview and inquire before purchasing. Please contact us before purchasing if you have any questions! This policy aligns with the standard Flevy Terms of Usage.
Got a question about the product? Email us at support@flevy.com or ask the author directly by using the "Ask the Author a Question" form. If you cannot view the preview above this document description, go here to view the large preview instead.
Source: Best Practices in Cyber Security PowerPoint Slides: Security Operations Center (SOC) Toolkit PowerPoint (PPTX) Presentation Slide Deck, SB Consulting