Cyber Security SOPs (600+ KPIs and Templates) (PowerPoint PPTX Slide Deck)
PowerPoint (PPTX) + Word (DOCX) 1,490 Slides
BENEFITS OF THIS POWERPOINT DOCUMENT
- Offers a comprehensive approach to building cybersecurity SOPs tailored to your organization's unique needs.
- Guides you through implementing risk management strategies aligned with industry standards and regulatory requirements.
- Equips teams with actionable playbooks for incident response, compliance audits, and third-party risk management.
CYBER SECURITY PPT DESCRIPTION
Curated by McKinsey-trained Executives
Master Cybersecurity with the Ultimate Guide
Are you ready to elevate your organization's cybersecurity strategy to new heights? Dive into our comprehensive guide, a must-have resource for businesses, IT professionals, and compliance officers seeking mastery in regulatory frameworks and risk management. This guide is packed with 1,400+ PowerPoint slides and comes with a 500-page Word file, ensuring you have all the tools needed to address today's most pressing cybersecurity challenges.
Unlock the Power of Cybersecurity Knowledge
Cybersecurity threats and compliance requirements are evolving faster than ever. Organizations face the challenge of keeping pace while safeguarding their data, meeting stringent regulatory demands, and mitigating risks. This guide is meticulously crafted to provide actionable insights, proven frameworks, and scalable strategies that empower you to achieve these goals.
Whether you're navigating GDPR, HIPAA, PCI DSS, or ISO standards, this guide delivers unparalleled depth across 41 comprehensive sections.
CONTENT OVERVIEW
Part 1: Foundations of Cybersecurity SOPs
1. Introduction to Cybersecurity SOPs
• Overview of SOPs in Cybersecurity
• Objectives and Goals of SOP Implementation
• Audience and Stakeholders for SOPs
• Benefits of SOPs in Cyber Defense and Compliance
2. Cybersecurity Principles and Concepts
• The CIA Triad: Confidentiality, Integrity, and Availability
• Defense in Depth Strategy
• Least Privilege Principle
• Zero Trust Model Overview
• Security vs. Usability: Balancing Needs
3. Regulations, Frameworks, and Standards
• Global Compliance Requirements:
• General Data Protection Regulation (GDPR)
• Health Insurance Portability and Accountability Act (HIPAA)
• Payment Card Industry Data Security Standard (PCI DSS)
• Cybersecurity Frameworks:
• NIST Cybersecurity Framework (CSF)
• ISO/IEC 27001 and 27002
• COBIT and ITIL for Cybersecurity Management
• Industry-Specific Regulations (e.g., CMMC for Defense, FFIEC for Financial Institutions)
4. Cybersecurity Governance
• Governance Structure and Policies
• Roles and Responsibilities of Stakeholders
• Establishing a Cybersecurity Steering Committee
• Risk Management Integration
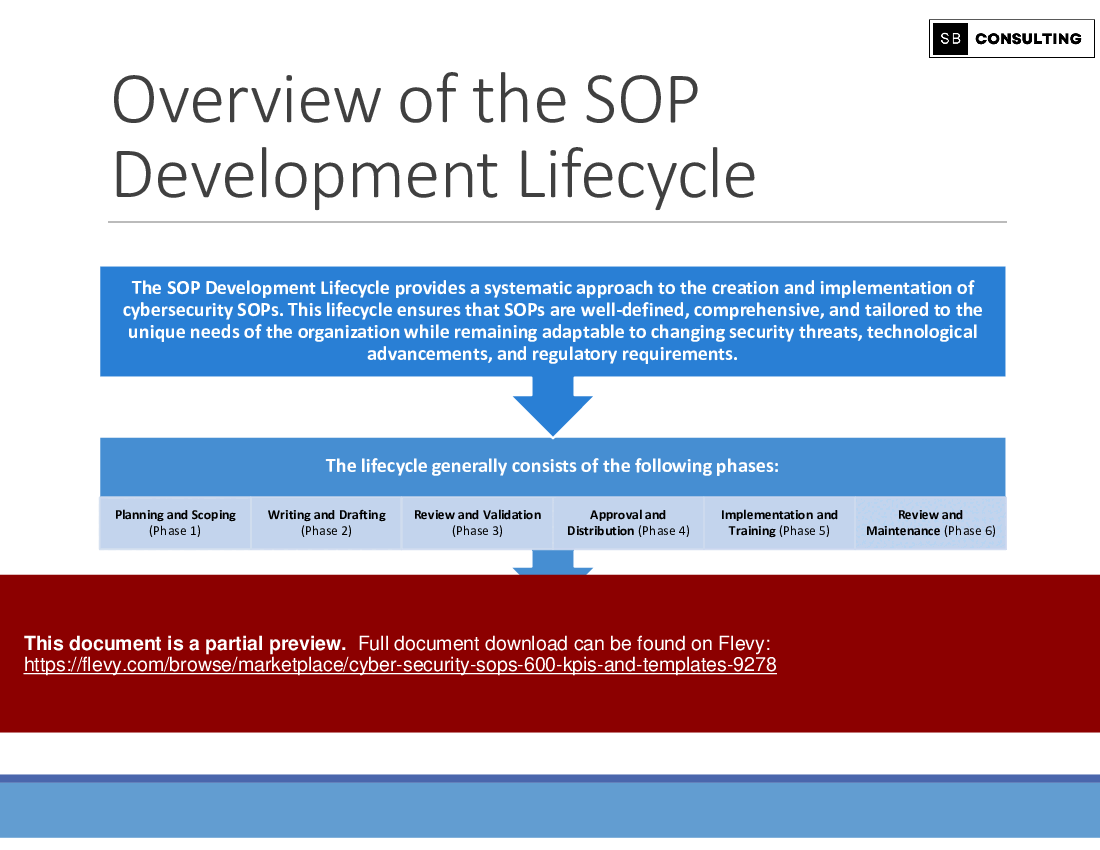
5. Developing and Documenting Cybersecurity SOPs
• SOP Lifecycle Phases: Planning, Writing, Implementing, Reviewing
• SOP Templates and Formatting Standards
• Tools for SOP Creation and Version Control
• SOP Distribution and Accessibility Guidelines
Part 2: Cybersecurity Operations SOPs
6. Access Control SOPs
• Creating User Accounts and Assigning Permissions
• Authentication Mechanisms (e.g., Passwords, MFA)
• Managing Shared Accounts and Service Accounts
• Privileged Access Control and Monitoring
• Periodic Access Reviews and Certification
7. Incident Management SOPs
• Incident Identification and Categorization
• Steps for Immediate Containment
• Notification and Communication Protocols
• Collaboration with Third Parties During Incidents
• Post-Incident Documentation and Root Cause Analysis
8. Network Security SOPs
• Firewall Rule Creation and Auditing
• VPN Configuration and Monitoring
• Implementing Secure Wireless Access Points
• Network Traffic Monitoring and Anomaly Detection
• Implementing Denial-of-Service (DoS) Mitigation Measures
9. Endpoint Security SOPs
• Device Onboarding Procedures
• Security Software Installation and Updates
• Device Health Monitoring and Compliance Checks
• Response to Infected or Compromised Devices
• Secure Disposal of Endpoint Devices
10. Data Protection SOPs
• Data Classification and Handling Guidelines
• Secure Storage and Encryption Requirements
• Implementing Backup and Recovery Procedures
• Protecting Personally Identifiable Information (PII)
• Data Masking and Tokenization
11. Cloud Security SOPs
• Secure Cloud Account Configuration
• Management of Cloud Storage Permissions
• Monitoring Cloud Workloads for Anomalies
• Encryption Standards for Cloud Data
• Disaster Recovery in Cloud Environments
Part 3: Advanced Cybersecurity SOPs
12. Threat Intelligence SOPs
• Gathering Threat Intelligence from Open Sources
• Utilizing Threat Intelligence Platforms (TIPs)
• Analyzing and Correlating Threat Data
• Sharing Threat Intelligence with Partners
13. Vulnerability Management SOPs
• Scheduling and Performing Vulnerability Scans
• Patch Deployment Procedures
• Documenting and Reporting Vulnerabilities
• Third-Party Vulnerability Management
14. Security Awareness and Training SOPs
• Designing Cybersecurity Training Programs
• Conducting Phishing Simulations
• Tracking Employee Security Training Completion
• Specialized Training for IT Staff and Developers
15. Malware Defense SOPs
• Identifying and Classifying Malware Threats
• Quarantine and Remediation Procedures
• Endpoint Detection and Response (EDR) Practices
• Reporting and Escalating Malware Incidents
16. API and Web Application Security SOPs
• Secure API Development and Testing
• Regular Web Application Scanning
• Managing Third-Party Libraries and Dependencies
• Protecting Against OWASP Top 10 Vulnerabilities
Part 4: Maintenance, Monitoring, and Continuous Improvement SOPs
17. Monitoring and Logging SOPs
• Configuring Security Information and Event Management (SIEM)
• Log Aggregation and Parsing
• Incident Detection from Logs
• Log Storage and Retention Guidelines
18. Audit and Compliance SOPs
• Preparing for Internal and External Audits
• Conducting Gap Analyses
• Managing Corrective Action Plans (CAPs)
• Ensuring Compliance with Legal Obligations
19. Backup and Recovery SOPs
• Implementing Regular Backup Schedules
• Testing Backups for Integrity and Completeness
• Recovery Procedures for Different Scenarios
• Offline and Immutable Backup Practices
20. Change Management SOPs
• Identifying and Documenting Configuration Changes
• Obtaining Necessary Approvals Before Changes
• Tracking Change Outcomes and Performance
• Emergency Change Procedures
21. Third-Party Risk Management SOPs
• Vetting Vendors During Procurement
• Conducting Regular Vendor Security Assessments
• Enforcing Security Requirements in Contracts
• Monitoring Vendor Access and Activity
Part 5: Emerging Trends and Strategic SOPs
22. Zero Trust SOPs
• Implementing Micro-Segmentation
• Continuous Authentication Mechanisms
• Securing Edge Devices in a Zero Trust Model
23. Operational Technology (OT) Security SOPs
• Securing Industrial Control Systems (ICS)
• Physical and Cyber Convergence SOPs
• Monitoring Critical Infrastructure for Threats
24. Ransomware Preparedness SOPs
• Preemptive Measures to Prevent Ransomware
• Developing a Ransomware Playbook
• Negotiation Protocols (If Applicable)
• Recovery from Ransomware Attacks
25. Artificial Intelligence Security SOPs
• Securing Machine Learning Pipelines
• Identifying Adversarial AI Threats
• Monitoring AI Decision-Making Processes
26. Cybersecurity Metrics and Reporting SOPs
• Defining Key Performance Indicators (KPIs)
• Cybersecurity Maturity Models
• Reporting to Executive Management
• Aligning Metrics with Business Objectives
TEMPALTES
Cybersecurity Standard Operating Procedures (SOPs)
1. Access Control Management SOP
2. Incident Response SOP
3. Data Backup and Recovery SOP
4. Patch Management SOP
5. Malware Incident Handling SOP
6. Vulnerability Management SOP
7. Network Security Configuration SOP
8. Email Security SOP
9. Endpoint Protection SOP
10. Secure Software Development Lifecycle (SDLC) SOP
11. Security Awareness Training SOP
12. Third-Party Vendor Risk Management SOP
13. Privileged Access Management SOP
14. Password Management SOP
15. Mobile Device Management SOP
16. Encryption Management SOP
17. Cloud Security Operations SOP
18. Internet Usage Policy SOP
19. Physical Security Controls SOP
20. Social Engineering Defense SOP
21. Phishing Incident Handling SOP
22. File Sharing Security SOP
23. Web Application Security SOP
24. Remote Access Policy SOP
25. Audit Log Review SOP
26. Security Incident Reporting SOP
27. Threat Intelligence Analysis SOP
28. Cybersecurity Policy Review SOP
29. Configuration Baseline Management SOP
30. Data Loss Prevention (DLP) SOP
31. Firewall Management SOP
32. Wireless Security SOP
33. User Account Management SOP
34. Insider Threat Management SOP
35. Forensic Investigation SOP
36. Internet of Things (IoT) Security SOP
37. DNS Security SOP
38. Penetration Testing SOP
39. Incident Communication SOP
40. Compliance Monitoring SOP
41. Legal and Regulatory Reporting SOP
42. Business Continuity and Disaster Recovery SOP
43. Secure File Transfer SOP
44. Change Management SOP
45. Secure Decommissioning SOP
46. Cloud Identity and Access Management SOP
47. Critical Infrastructure Protection SOP
48. Threat Hunting SOP
49. SIEM (Security Information and Event Management) SOP
50. Key Management SOP
Cybersecurity Assessment Forms
1. Vulnerability Assessment Form
2. Network Security Assessment Form
3. Penetration Testing Assessment Form
4. Risk Assessment Form
5. Data Protection Impact Assessment Form
6. Cybersecurity Maturity Assessment Form
7. Third-Party Risk Assessment Form
8. Incident Response Assessment Form
9. Cloud Security Assessment Form
10. Endpoint Security Assessment Form
11. Insider Threat Risk Assessment Form
12. Phishing Simulation Assessment Form
13. Application Security Assessment Form
14. Wireless Network Security Assessment Form
15. Firewall Configuration Assessment Form
16. Compliance Assessment Form
17. GDPR Readiness Assessment Form
18. SOC 2 Assessment Form
19. PCI DSS Assessment Form
20. HIPAA Security Assessment Form
21. Business Continuity Assessment Form
22. Disaster Recovery Plan Assessment Form
23. Encryption Standards Assessment Form
24. Mobile Device Security Assessment Form
25. Malware Defense Assessment Form
26. Threat Intelligence Assessment Form
27. DNS Security Assessment Form
28. Physical Security Assessment Form
29. Secure File Sharing Assessment Form
30. Access Control Assessment Form
31. Identity and Access Management Assessment Form
32. Cyber Insurance Readiness Assessment Form
33. Patch Management Effectiveness Assessment Form
34. Email Security Configuration Assessment Form
35. Web Application Security Assessment Form
36. IoT Security Assessment Form
37. Zero Trust Architecture Assessment Form
38. Security Awareness Training Effectiveness Assessment Form
39. Incident Reporting Effectiveness Assessment Form
40. Privileged Access Assessment Form
41. Security Governance Assessment Form
42. Secure Software Development Practices Assessment Form
43. Data Classification Assessment Form
44. Security Operations Center (SOC) Assessment Form
45. Threat Hunting Maturity Assessment Form
46. API Security Assessment Form
47. Critical Infrastructure Risk Assessment Form
48. Configuration Management Effectiveness Assessment Form
49. Security Metrics Assessment Form
50. Cyber Resilience Assessment Form
Cybersecurity SOP Checklists
1. Access Control Checklist
2. Incident Response Plan Checklist
3. Vulnerability Management Checklist
4. Backup and Recovery Checklist
5. Patch Management Checklist
6. Network Security Configuration Checklist
7. Malware Handling Checklist
8. Privileged Access Management Checklist
9. Password Policy Checklist
10. Mobile Device Security Checklist
11. Cloud Security Checklist
12. Physical Security Controls Checklist
13. Social Engineering Awareness Checklist
14. Phishing Defense Checklist
15. File Sharing Security Checklist
16. Secure Software Development Checklist
17. Remote Work Security Checklist
18. Audit Log Review Checklist
19. Security Awareness Training Checklist
20. Threat Intelligence Sharing Checklist
21. Cybersecurity Policy Update Checklist
22. Secure Configuration Baseline Checklist
23. DLP Implementation Checklist
24. Firewall Rule Validation Checklist
25. Wireless Security Checklist
26. User Account Management Checklist
27. Insider Threat Mitigation Checklist
28. Forensic Readiness Checklist
29. IoT Security Checklist
30. DNS Security Checklist
31. Penetration Testing Checklist
32. Incident Communication Checklist
33. Compliance Reporting Checklist
34. Disaster Recovery Testing Checklist
35. Secure File Transfer Checklist
36. Change Management Checklist
37. Secure Asset Decommissioning Checklist
38. Cloud IAM Configuration Checklist
39. Critical Infrastructure Protection Checklist
40. Threat Hunting Procedures Checklist
41. SIEM Optimization Checklist
42. Secure Key Management Checklist
43. Third-Party Risk Management Checklist
44. Encryption Management Checklist
45. Endpoint Protection Checklist
46. Internet Usage Monitoring Checklist
47. Application Security Testing Checklist
48. Secure API Integration Checklist
49. Zero Trust Implementation Checklist
50. Cybersecurity Metrics Tracking Checklist
Cybersecurity KPI Categories
1. Incident Response
2. Threat Detection
3. Vulnerability Management
4. Data Protection
5. Compliance Management
6. Risk Management
7. Security Awareness Training
8. Endpoint Security
9. Patch Management
10. Cloud Security
11. Access Management
12. Identity Management
13. Malware Defense
14. Phishing Defense
15. Network Security
16. Application Security
17. Email Security
18. SIEM Performance
19. Threat Hunting
20. Cyber Threat Intelligence
21. Insider Threat Management
22. Business Continuity
23. Disaster Recovery
24. Encryption Standards
25. Third-Party Risk Management
26. Secure Configuration Management
27. Wireless Security
28. API Security
29. IoT Security
30. Data Loss Prevention
31. Secure Software Development
32. Compliance Readiness
33. Incident Reporting
34. Security Governance
35. SOC Effectiveness
36. Privileged Access Management
37. Security Policy Adherence
38. Cyber Resilience
39. Firewall Management
40. DNS Security
41. Secure File Transfer
42. Zero Trust Architecture
43. Audit Log Analysis
44. Security Metrics Development
45. Mobile Device Security
46. Physical Security
47. Threat Actor Analysis
48. Deception Technology
49. Cyber Insurance Coverage
50. Web Application Security
51. Legal and Regulatory Reporting
52. Data Classification
53. Security Framework Implementation
54. Compliance Audit Results
55. Threat Vector Analysis
56. Incident Escalation
57. Remote Work Security
58. Security Investments ROI
59. Security Automation
60. Emerging Technology Risks
Cybersecurity OKRs
1. Improve Incident Response Time
2. Reduce Phishing Attack Success Rate
3. Enhance Endpoint Protection Coverage
4. Increase Employee Security Awareness
5. Decrease Vulnerability Remediation Time
6. Strengthen Cloud Security Posture
7. Enhance Data Encryption Coverage
8. Improve Threat Detection Accuracy
9. Expand Threat Intelligence Sources
10. Increase Patch Management Effectiveness
11. Reduce Malware Infection Incidents
12. Optimize SIEM Performance Metrics
13. Improve Compliance Audit Scores
14. Expand Zero Trust Implementation
15. Enhance Privileged Access Security
16. Improve Application Security Testing Results
17. Secure Third-Party Vendor Relationships
18. Reduce Data Loss Incidents
19. Improve Wireless Network Security
20. Increase Secure API Adoption
21. Enhance Insider Threat Detection Capabilities
22. Improve Cyber Risk Assessment Accuracy
23. Increase Adoption of Encryption Standards
24. Strengthen Mobile Device Security Policies
25. Reduce Downtime in Disaster Recovery Events
26. Optimize Firewall Rules Management
27. Enhance DNS Security Configurations
28. Increase Cybersecurity Framework Adherence
29. Improve Threat Hunting Operations
30. Reduce Cybersecurity Tool Redundancy
Key Learning Objectives
Understand Critical Cybersecurity Concepts
Gain mastery over cybersecurity frameworks like ISO 27001, NIST, and regulatory frameworks such as GDPR, HIPAA, and PCI DSS.
Learn to Build Robust SOPs
Develop and implement Standard Operating Procedures (SOPs) tailored for compliance, incident response, risk mitigation, and beyond.
Streamline Risk Management
Discover effective risk assessment methodologies, asset classification techniques, and risk mitigation strategies.
Achieve Regulatory Excellence
Master industry-specific compliance protocols to streamline audits, reporting, and legal alignment.
Enhance Governance & Resilience
Create frameworks for cyber risk governance and resilience to withstand modern cyber threats.
Leverage Emerging Technologies
Address risks from AI, machine learning, blockchain, and multi-cloud environments while preparing for future technologies.
Invest in Your Cybersecurity Future Today
This guide is more than just a resource; it's an investment in your organization's security and compliance journey. With 1,400+ slides and a 500-page companion document, it's the ultimate toolkit for any professional serious about mastering cybersecurity.
Key Words:
Strategy & Transformation, Growth Strategy, Strategic Planning, Strategy Frameworks, Innovation Management, Pricing Strategy, Core Competencies, Strategy Development, Business Transformation, Marketing Plan Development, Product Strategy, Breakout Strategy, Competitive Advantage, Mission, Vision, Values, Strategy Deployment & Execution, Innovation, Vision Statement, Core Competencies Analysis, Corporate Strategy, Product Launch Strategy, BMI, Blue Ocean Strategy, Breakthrough Strategy, Business Model Innovation, Business Strategy Example, Corporate Transformation, Critical Success Factors, Customer Segmentation, Customer Value Proposition, Distinctive Capabilities, Enterprise Performance Management, KPI, Key Performance Indicators, Market Analysis, Market Entry Example, Market Entry Plan, Market Intelligence, Market Research, Market Segmentation, Market Sizing, Marketing, Michael Porter's Value Chain, Organizational Transformation, Performance Management, Performance Measurement, Platform Strategy, Product Go-to-Market Strategy, Reorganization, Restructuring, SWOT, SWOT Analysis, Service 4.0, Service Strategy, Service Transformation, Strategic Analysis, Strategic Plan Example, Strategy Deployment, Strategy Execution, Strategy Frameworks Compilation, Strategy Methodologies, Strategy Report Example, Value Chain, Value Chain Analysis, Value Innovation, Value Proposition, Vision Statement, Corporate Strategy, Business Development, Busienss plan pdf, business plan, PDF, Biusiness Plan DOC, Bisiness Plan Template, PPT
NOTE: Our digital products are sold on an "as is" basis, making returns and refunds unavailable post-download. Please preview and inquire before purchasing. Please contact us before purchasing if you have any questions! This policy aligns with the standard Flevy Terms of Usage.
Disclaimer
This guide is intended for educational purposes only and does not constitute legal advice. Frameworks such as GDPR, HIPAA, and ISO are referenced, and all copyrights belong to their respective owners. Users are advised to consult a professional for tailored guidance and verify the applicability of the information to their specific situation. No warranties, expressed or implied, are provided, and the authors disclaim liability for any use or reliance on this material.
Got a question about the product? Email us at support@flevy.com or ask the author directly by using the "Ask the Author a Question" form. If you cannot view the preview above this document description, go here to view the large preview instead.
TOPIC FAQ
What are the core phases for developing cybersecurity SOPs?
Cybersecurity SOPs are developed through a lifecycle of discrete phases: planning, writing, implementing, and reviewing. Planning defines scope and stakeholders, writing codifies procedures and templates, implementing covers distribution and version control, and reviewing ensures updates and continuous improvement — 4 lifecycle phases.Which regulatory frameworks should cybersecurity SOPs align to for data protection?
SOPs should align to global regulations and standards referenced for data protection such as GDPR, HIPAA, and PCI DSS, alongside frameworks that guide controls and governance like NIST Cybersecurity Framework and ISO/IEC 27001/27002, ensuring coverage across legal and technical obligations.What KPIs are useful to track incident response performance?
Incident response performance is typically monitored via KPIs and OKRs focused on response and reporting outcomes, for example improving incident response time and measuring incident reporting effectiveness. These metrics map to the Incident Response KPI category and related OKRs in the toolkit.How should organizations evaluate third‑party vendor security?
Vendor security evaluation combines upfront vendor vetting, periodic security assessments, contract security requirements, and ongoing monitoring of vendor activity. The toolkit supports this approach with a Third‑Party Vendor Risk Management SOP and a Third‑Party Risk Assessment Form as practical artifacts.I'm a small security team with limited budget—what SOPs should I prioritize first?
Small teams should prioritize SOPs that reduce operational risk: Incident Response SOP, Access Control Management SOP, Data Backup and Recovery SOP, and Patch Management SOP. These address containment, access hygiene, recovery, and vulnerability remediation as foundational controls.How many templates and assessment tools do commercial cybersecurity SOP toolkits typically contain?
This offering documents that a comprehensive commercial toolkit can include large template libraries; Flevy's Cyber Security SOPs (600+ KPIs and Templates) lists 50 SOP templates, 50 assessment forms, 50 checklists, plus 60 KPI categories and extensive slide/word content.What monitoring and logging practices should SOPs cover for effective detection?
Monitoring and logging SOPs should specify SIEM configuration, log aggregation and parsing, detection rules that surface incidents from logs, and log storage/retention guidelines to support forensic and detection activities, including SIEM configuration and log retention practices.How can SOPs prepare an organization for ransomware incidents?
Ransomware preparedness SOPs include preemptive controls, a documented ransomware playbook covering containment and recovery, negotiation protocols where applicable, and testing recovery procedures. Organizations should codify these steps into a Ransomware Playbook for operational readiness.Source: Best Practices in Cyber Security PowerPoint Slides: Cyber Security SOPs (600+ KPIs and Templates) PowerPoint (PPTX) Presentation Slide Deck, SB Consulting
This document is available as part of the following discounted bundle(s):
Save %!
Enterprise Operations & Governance SOP Master Suite
This bundle contains 6 total documents. See all the documents to the right.