SOC for Cybersecurity - Implementation Toolkit (Excel XLSX)
Excel (XLSX) + Zip archive file (ZIP)
CYBER SECURITY EXCEL DESCRIPTION
SOC for Cybersecurity is a reporting framework developed by the AICPA that provides a consistent approach for evaluating and communicating an organization's cybersecurity risk management program. This framework is important because it helps organizations demonstrate their cybersecurity readiness, effectiveness of controls, and ability to protect sensitive data against cyber threats. By undergoing a SOC for Cybersecurity examination, companies can enhance stakeholder confidence, provide transparency into their cybersecurity posture, and showcase their commitment to robust cyber risk management practices in a rapidly evolving threat landscape.
This SOC for Cybersecurity Implementation Toolkit includes a set of best practice templates, step-by-step workplans, and maturity diagnostics for any SOC cybersecurity implementation related project. Please note the above partial preview is ONLY of the Self Assessment Excel Dashboard, referenced in steps 1 and 2 (see below for more details).
Through a 3-step process, this toolkit will guide you from idea to implementation. Please find a below a summary of the 3 steps.
STEP 1: Get your bearings
Start with the latest quick edition of the SOC for Cybersecurity Self Assessment book in PDF containing 49 requirements to perform a quickscan, get an overview and share with stakeholders.
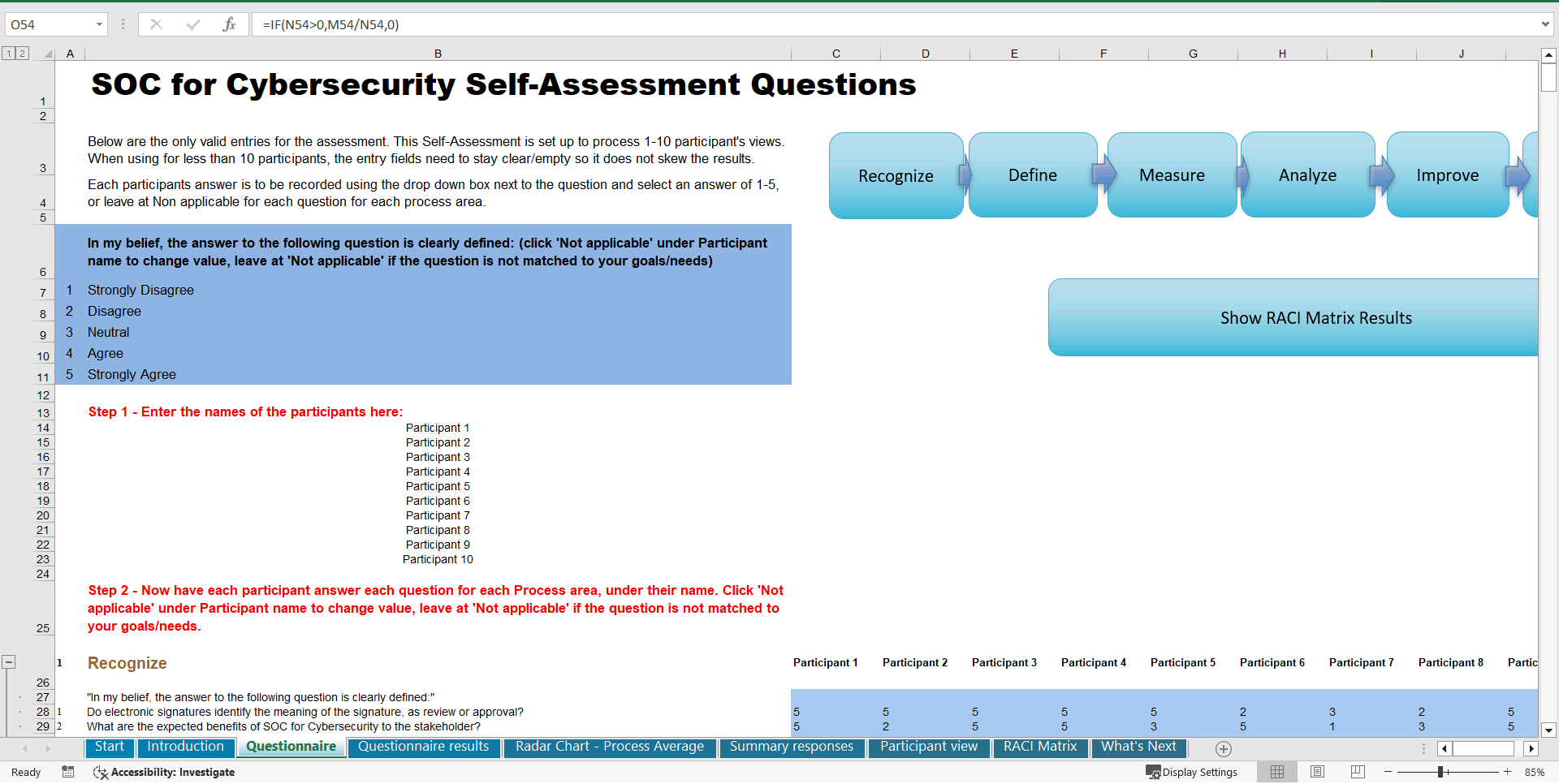
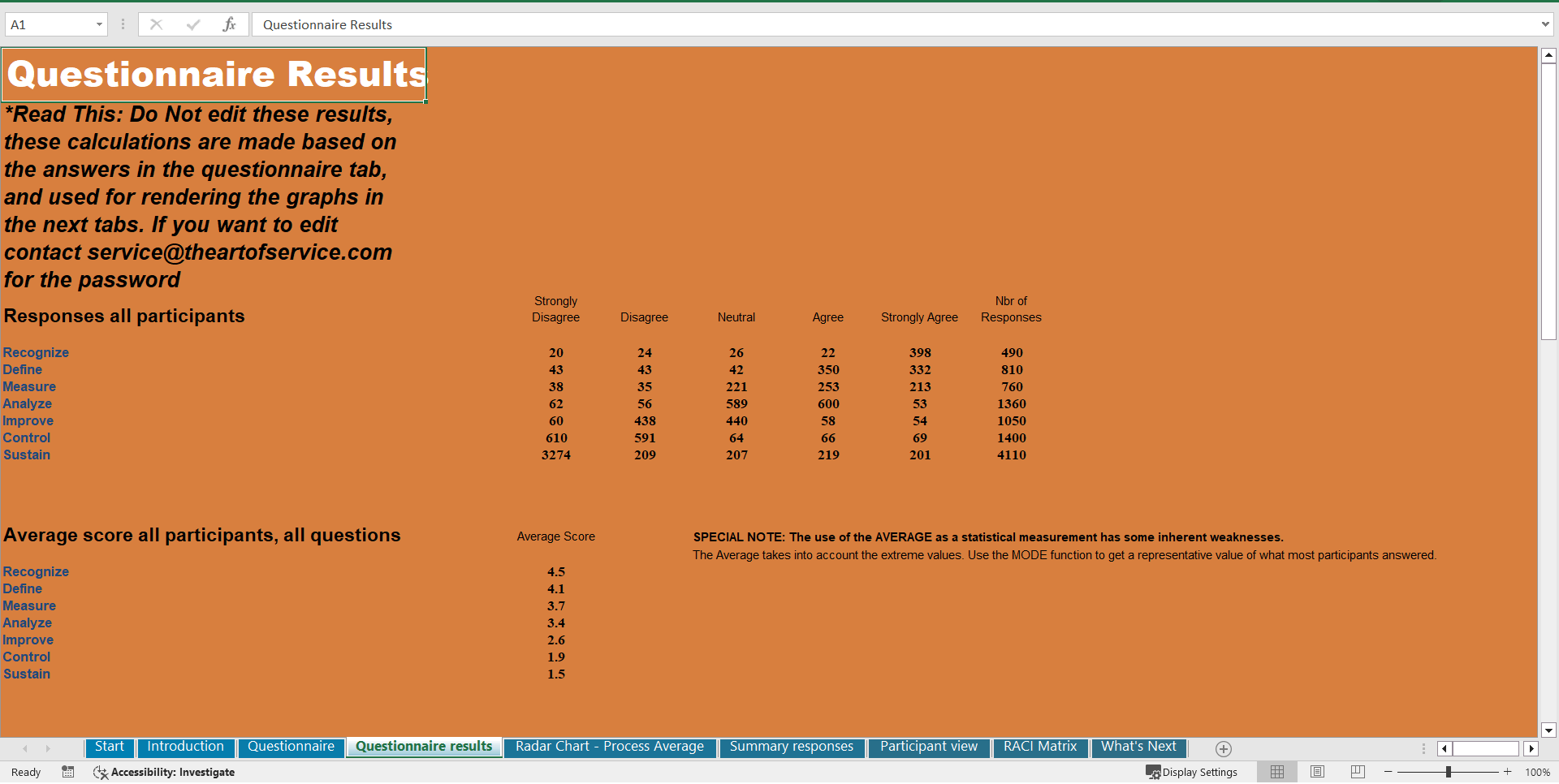
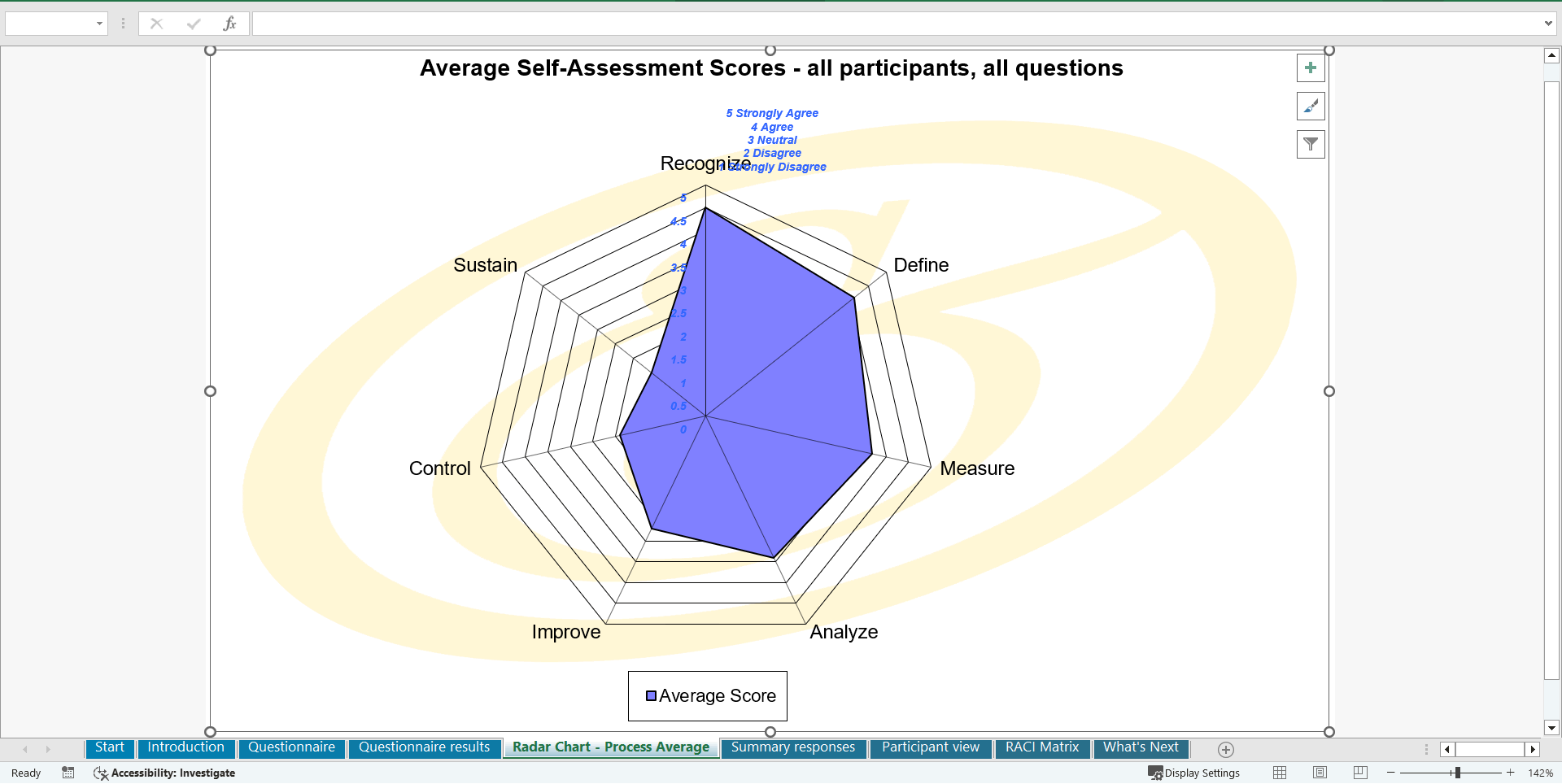
Organized in a data driven improvement cycle RDMAICS (Recognize, Define, Measure, Analyze, Improve, Control and Sustain), check the example pre-filled Self-Assessment Excel Dashboard to get familiar with results generation.
STEP 2: Set concrete goals, tasks, dates and numbers you can track
Featuring 998 new and updated case-based questions, organized into seven core areas of process design, this Self-Assessment will help you identify areas in which SOC for Cybersecurity improvements can be made.
The Self-Assessment Excel Dashboard; with the SOC for Cybersecurity Self-Assessment and Scorecard you will develop a clear picture of which SOC for Cybersecurity areas need attention, which requirements you should focus on and who will be responsible for them:
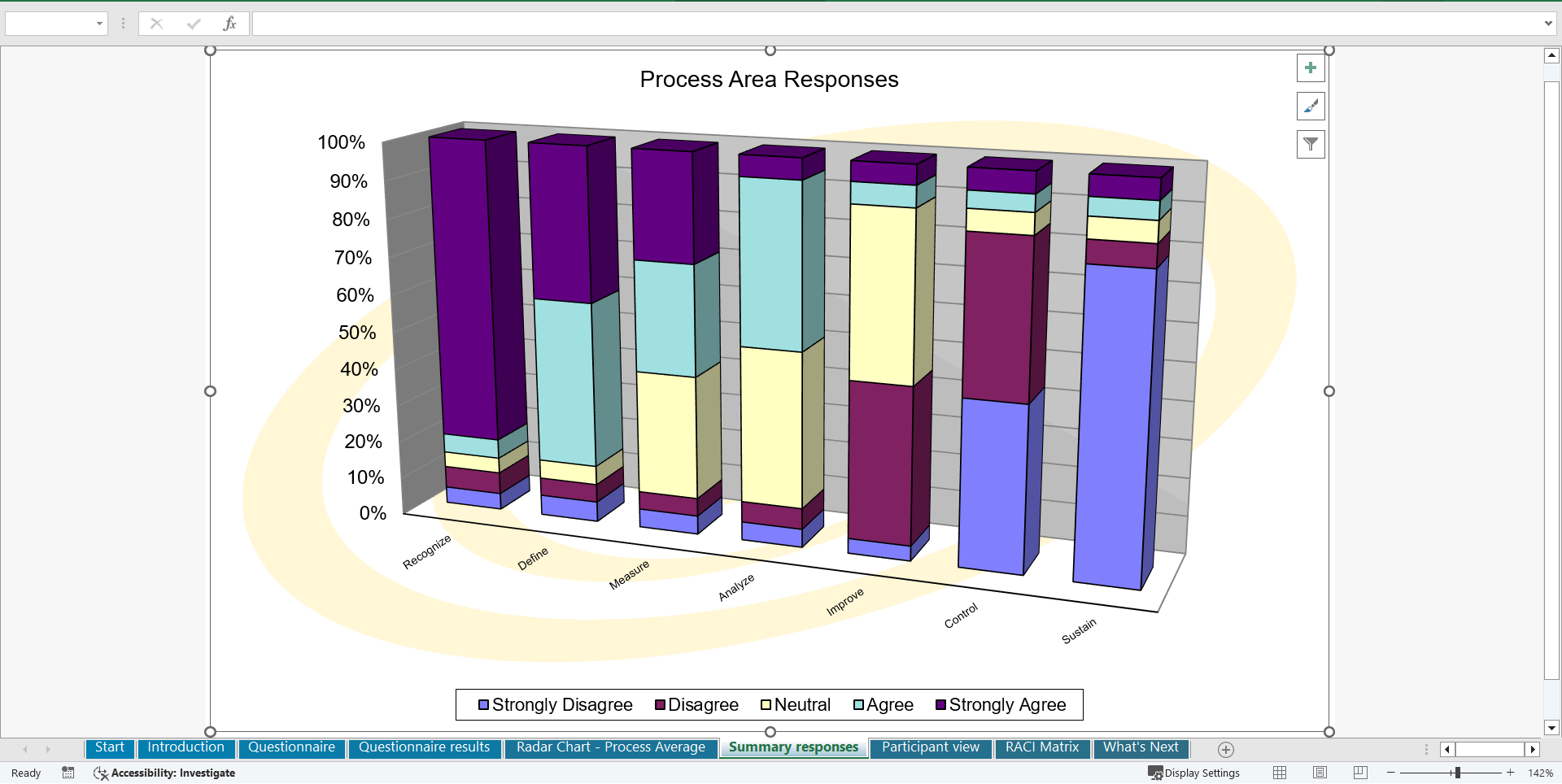
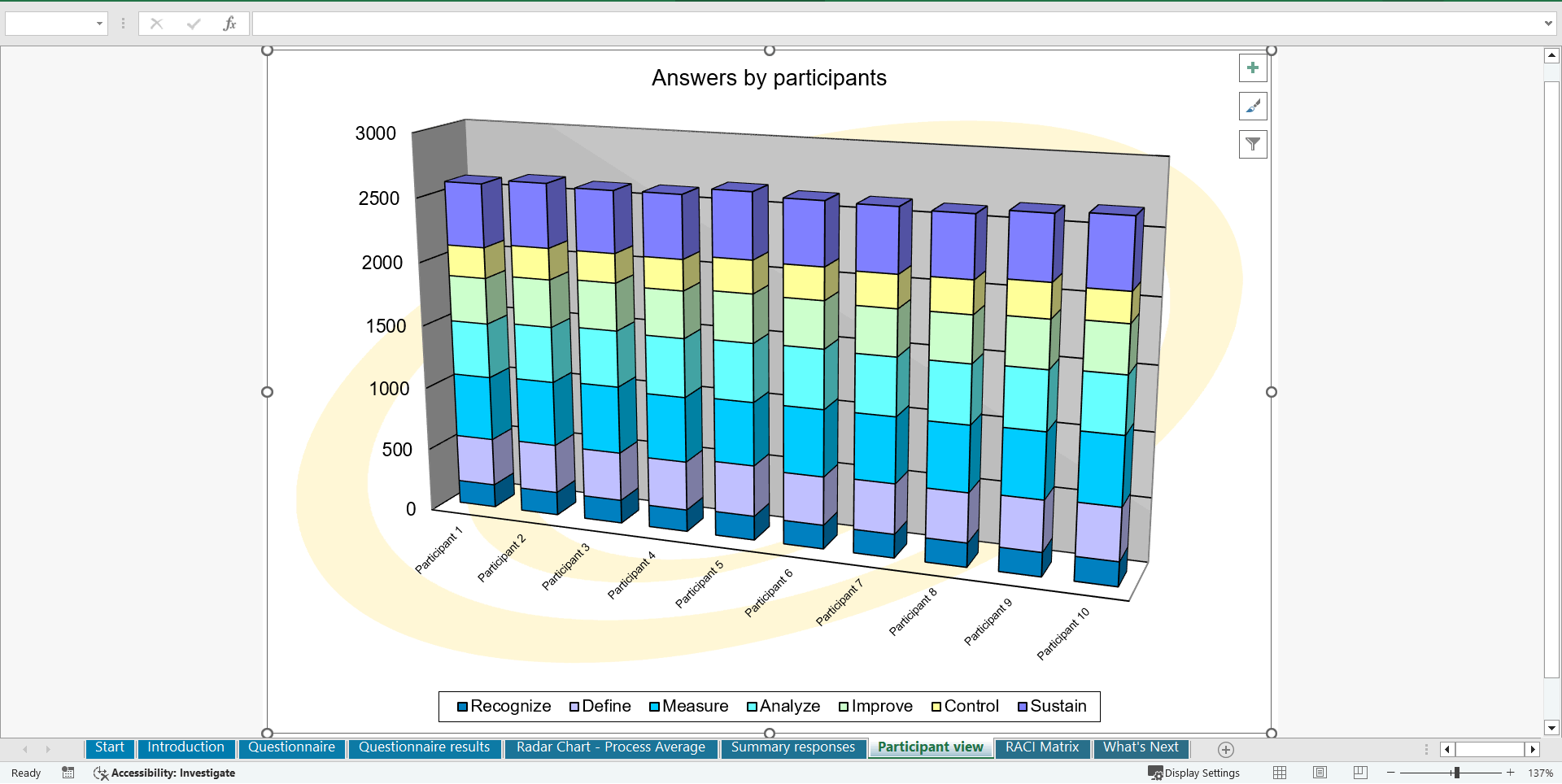
• Shows your organization instant insight in areas for improvement: Auto generates reports, radar chart for maturity assessment, insights per process and participant and bespoke, ready to use, RACI Matrix
• Gives you a professional Dashboard to guide and perform a thorough SOC for Cybersecurity Self-Assessment
• Is secure: Ensures offline data protection of your Self-Assessment results
• Dynamically prioritized projects-ready RACI Matrix shows your organization exactly what to do next
STEP 3: Implement, Track, follow up and revise strategy
The outcomes of STEP 2, the self assessment, are the inputs for STEP 3; Start and manage SOC for Cybersecurity projects with the 62 implementation resources. There are 62 step-by-step SOC for Cybersecurity Project Management Form Templates covering over 1500 SOC for Cybersecurity project requirements and success criteria.
Got a question about the product? Email us at support@flevy.com or ask the author directly by using the "Ask the Author a Question" form. If you cannot view the preview above this document description, go here to view the large preview instead.
Source: Best Practices in Cyber Security, System and Organization Controls Excel: SOC for Cybersecurity - Implementation Toolkit Excel (XLSX) Spreadsheet, Gerard Blokdijk