ISO 27001/27002 Security Audit Questionnaire (Excel XLSX)
Excel (XLSX)
BENEFITS OF THIS EXCEL DOCUMENT
- Help you assess your compliance with the ISO 27001 Security standard.
- Support you to improve your company.
- Compare your security measures with what may be expected and improve them accordingly.
ISO 27001 EXCEL DESCRIPTION
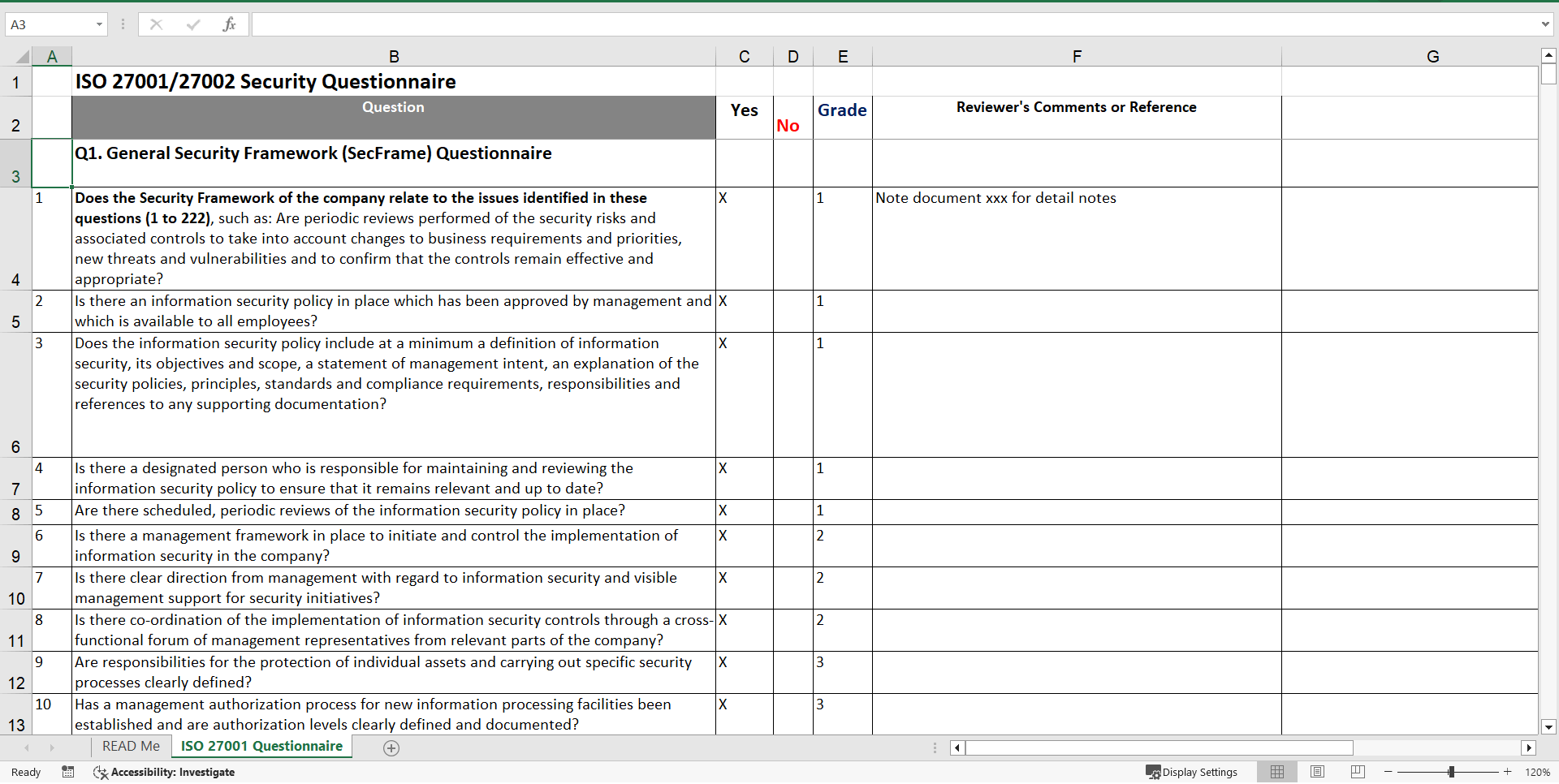
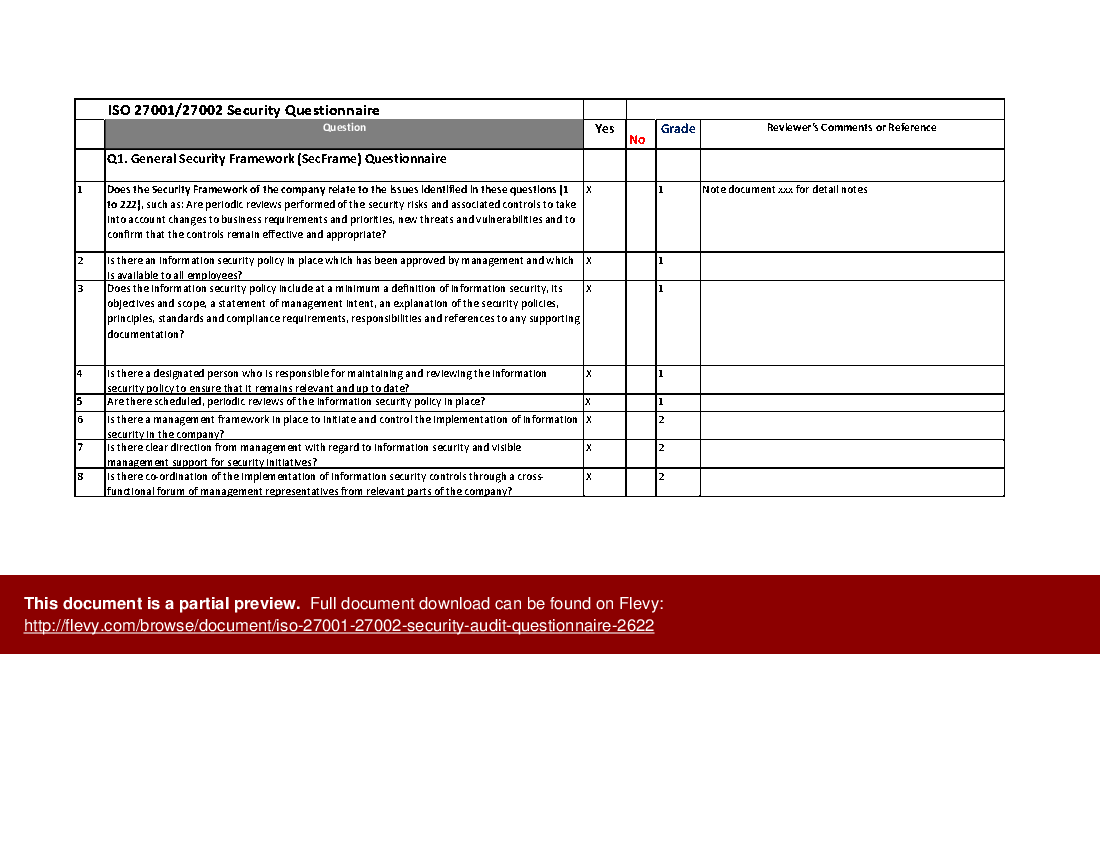
This spreadsheet contains a set of security questions and an evaluation method, which could be used to support your efforts in assessing whether your company complies with the requirements of ISO Security standard ISO 27001/27002.
It is made up of 2 parts. The first part contains a summary of the questionnaires included in the second part and instructions on using this spreadsheet.
The second part contains 17 questionnaires with 372 questions on all aspects of information security, as defined in the ISO standard.
The questionnaires included in this spreadsheet are:
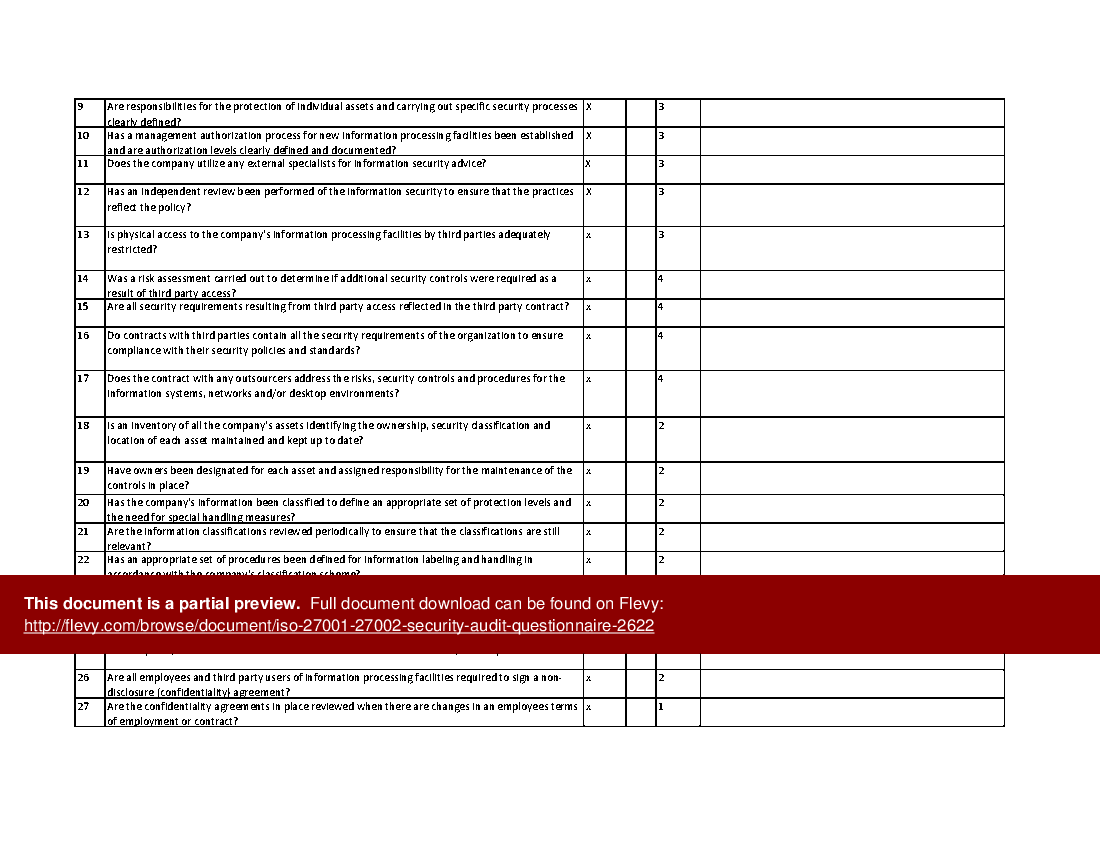
Q1. General Security Framework Questionnaire (222 questions)
Q2. Information Security Policies (A5) Questionnaire (5 questions)
Q3. Organization of Information Security (A6) Questionnaire (8 questions)
Q4. Human resources security (A7) Questionnaire (8 questions)
Q5. Asset management (A8) Questionnaire (12 questions)
Q6. Access control (Section A9) Questionnaire (15 questions)
Q7. Cryptography (Section A10) Questionnaire (3 questions)
Q8. Physical security (Section A11-part 1) Questionnaire (12 questions)
Q9. Environmental security (Section A11-part 2) Questionnaire (8 questions)
Q10. Data Protection (Section A11-part 3) Questionnaire (6 questions)
Q11. Operations security (Section A12) Questionnaire (10 questions)
Q12. Communications security (Section A13) Questionnaire (8 questions)
Q13. System acquisition, development and maintenance (A14) Questionnaire (16 questions)
Q14. Supplier relationships (A15) Questionnaire (7 questions)
Q15. Information security incident management (A16) Questionnaire (6 questions)
Q16. Information security aspects of business continuity management
(A17) Questionnaire (10 questions)
Q17. Compliance (A18) Questionnaire (9 questions)
This template offers a comprehensive grading system to evaluate your organization's adherence to each questionnaire section. The evaluation grades provide a clear, quantifiable measure of compliance, making it easier to identify areas needing improvement. The tool is designed for ease of use, ensuring that your team can efficiently conduct thorough security audits. This structured approach helps in maintaining robust information security management practices, aligning with ISO standards.
Got a question about the product? Email us at support@flevy.com or ask the author directly by using the "Ask the Author a Question" form. If you cannot view the preview above this document description, go here to view the large preview instead.
Source: Best Practices in ISO 27001, ISO 27002 Excel: ISO 27001/27002 Security Audit Questionnaire Excel (XLSX) Spreadsheet, John Kyriazoglou