WORD DESCRIPTION
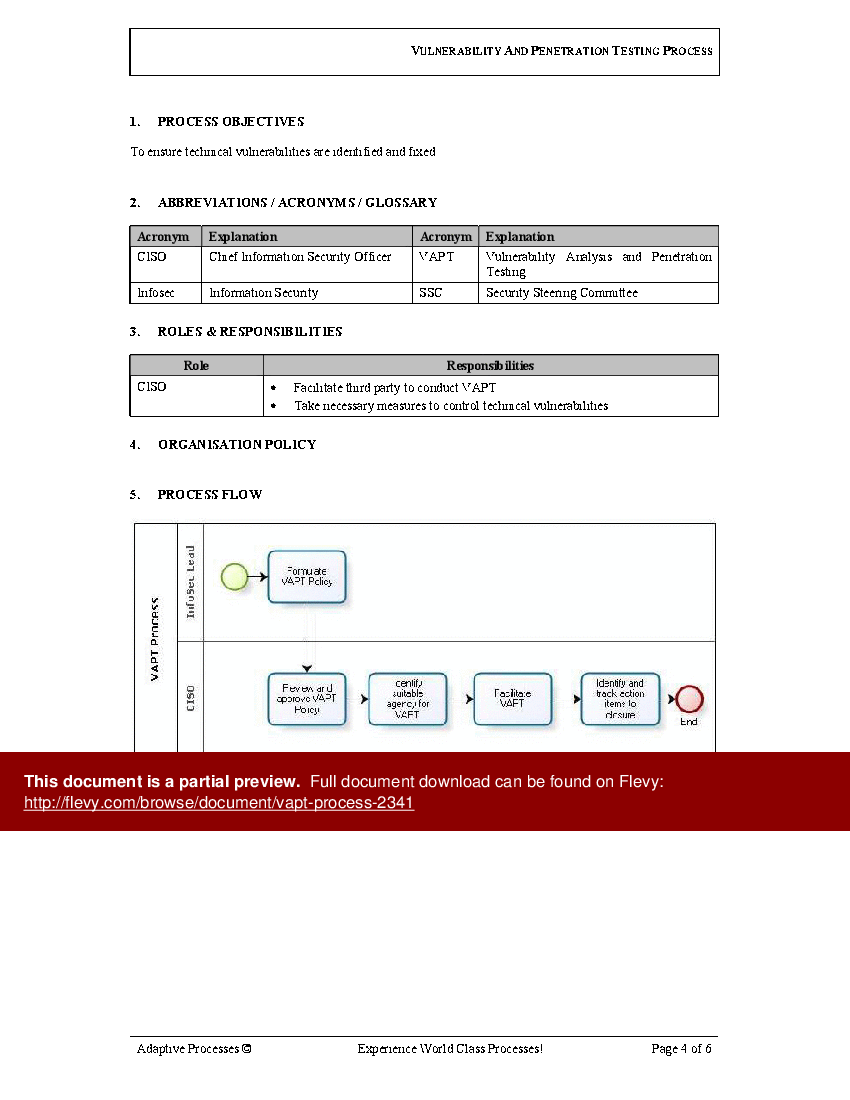
VAPT Process
Vulnerability Analysis and Penetration Testing
To ensure technical vulnerabilities are identified and fixed
Got a question about the product? Email us at support@flevy.com or ask the author directly by using the "Ask the Author a Question" form. If you cannot view the preview above this document description, go here to view the large preview instead.
Source: VAPT Process Word (DOC) Document, Adaptive US Inc.