Physical Security Management (PowerPoint PPTX Slide Deck)
PowerPoint (PPTX) 155 Slides
BENEFITS OF THIS POWERPOINT DOCUMENT
- Equips businesses with a foundational understanding of physical security management, essential for crafting effective security strategies tailored to their unique needs.
- Highlights the critical importance of prioritizing physical security management to safeguard assets, personnel, and maintain business continuity amidst evolving threats.
- Empowers organizations with actionable insights, tools, and case studies to implement robust physical security measures, ensuring resilience against security risks and emergencies.
RISK MANAGEMENT PPT DESCRIPTION
Curated by McKinsey-trained Executives
Unlocking the Complete Physical Security Management Business Toolkit: Empowering Your Organization with Expertise and Strategy
In today's ever-evolving landscape, the importance of physical security management cannot be overstated. As businesses expand and technology advances, the risks to physical assets and personnel also grow. Whether you're a small business or a large corporation, having a comprehensive understanding of physical security is crucial to safeguarding your assets and maintaining business continuity.
Introducing the Complete Physical Security Management Business Toolkit, a comprehensive 150+ slides PowerPoint deck designed to equip businesses with the knowledge, strategies, and tools necessary to enhance their physical security posture. Let's delve into the wealth of expertise this toolkit offers, covering everything from risk assessment to emergency preparedness and beyond.
CONTENT OVERVIEW
• Introduction to Physical Security
• Importance of Physical Security Management
• Risk Management
• Risk Assessment in Physical Security
• Perimeter Security
• Access Control
• Types of Access Control
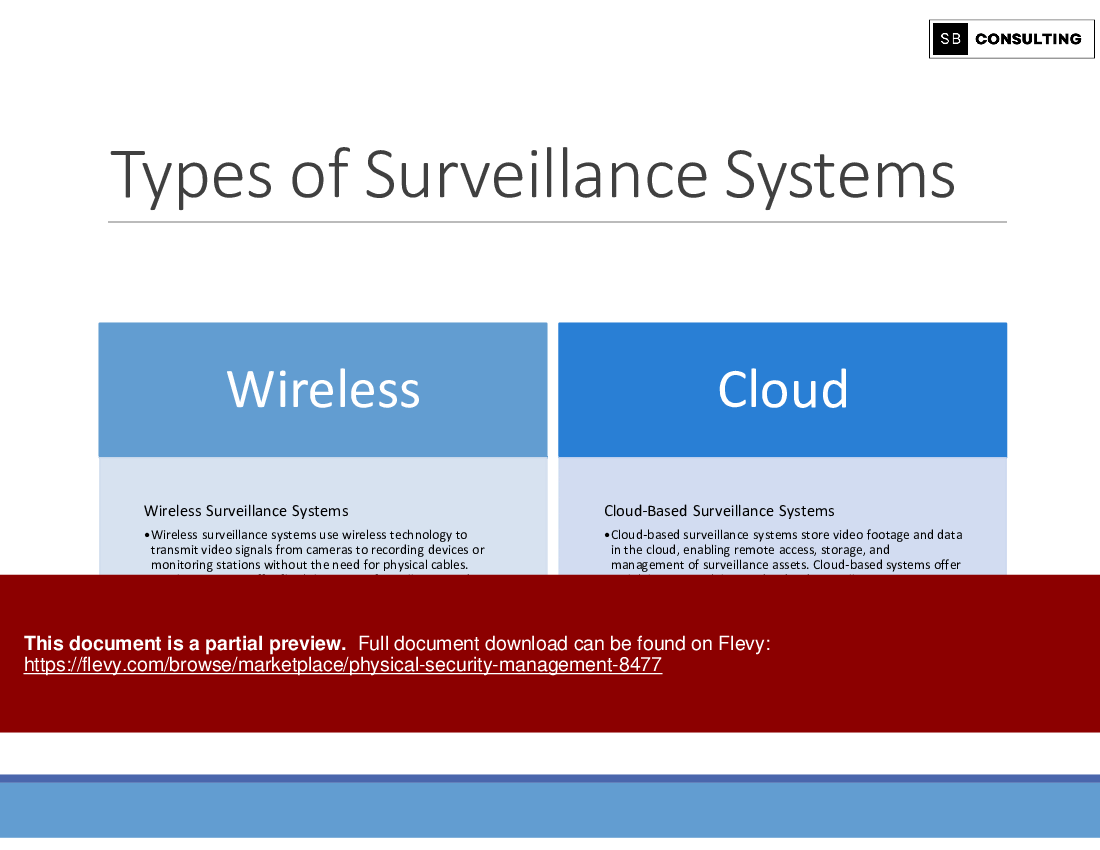
• Surveillance Systems
• Intrusion Detection Systems
• Alarm Systems
• Visitor Management
• Security Policies and Procedures
• Emergency Preparedness
• Physical Security Training
• Alarm Management
• Physical Security Information System
• Physical Security KPIs and Metrics
• Physical Security Checklists
• Physical Security Management Case Study
LEARNING OBJECTIVES
Introduction to Physical Security:
Learn the fundamentals of physical security, including its definition, objectives, and the core principles that underpin effective security strategies. Gain insights into the evolving threats landscape and why physical security is a cornerstone of any robust security framework.
Importance of Physical Security Management:
Discover why investing in physical security management is essential for protecting your organization's assets, reputation, and personnel. Explore real-world examples of the consequences of inadequate physical security and understand the tangible benefits of a proactive approach.
Risk Management:
Delve into the principles of risk management and how they apply to physical security. Identify potential threats and vulnerabilities within your organization and learn how to prioritize and mitigate risks effectively to minimize impact and maximize resilience.
Risk Assessment in Physical Security:
Master the art of conducting comprehensive risk assessments tailored to your organization's unique needs. Explore methodologies, tools, and best practices for identifying, analyzing, and evaluating security risks across various assets and environments.
Perimeter Security:
Learn how to secure your organization's perimeter against unauthorized access and intrusion. Explore physical barriers, access control measures, and surveillance technologies designed to fortify your premises and deter potential threats.
Access Control:
Gain a deep understanding of access control principles and the various types of access control systems available. From traditional locks and keys to sophisticated biometric solutions, explore how to manage and monitor access to critical areas effectively.
Surveillance Systems:
Explore the role of surveillance systems in enhancing situational awareness and deterring security threats. From CCTV cameras to advanced video analytics, learn how to design and deploy surveillance solutions tailored to your organization's needs.
Intrusion Detection Systems:
Discover how intrusion detection systems can help detect and respond to unauthorized entry or suspicious activity promptly. Explore different types of intrusion detection technologies, such as motion sensors, perimeter alarms, and acoustic sensors.
Alarm Systems:
Learn how alarm systems can serve as an early warning mechanism against security breaches and emergencies. Explore the components of alarm systems, including sensors, control panels, and communication protocols, and understand how to integrate them into your security infrastructure effectively.
Visitor Management:
Develop robust visitor management protocols to regulate access and monitor guest activity within your premises. From check-in procedures to badge issuance, learn how to maintain control and accountability while providing a welcoming environment for visitors.
Security Policies and Procedures:
Establish clear and comprehensive security policies and procedures to guide the behavior and actions of personnel. From access control protocols to incident response plans, ensure that everyone in your organization understands their roles and responsibilities in maintaining security.
Emergency Preparedness:
Prepare your organization to effectively respond to emergencies and crisis situations. From natural disasters to security incidents, develop contingency plans, evacuation procedures, and communication protocols to mitigate risks and ensure the safety of personnel.
Physical Security Training:
Invest in ongoing training and education to empower your staff with the knowledge and skills necessary to uphold security standards. From basic security awareness to specialized training for security personnel, foster a culture of vigilance and preparedness across your organization.
Alarm Management:
Optimize the performance of your alarm systems through effective management and monitoring practices. Learn how to configure alarm thresholds, prioritize alerts, and coordinate response efforts to minimize false alarms and maximize security effectiveness.
Physical Security Information System:
Harness the power of technology to centralize and streamline physical security management processes. Explore the features and capabilities of physical security information systems (PSIM), including incident tracking, data analysis, and reporting tools.
Physical Security KPIs and Metrics:
Measure the effectiveness of your physical security initiatives using key performance indicators (KPIs) and metrics. From incident response times to security incident trends, gain actionable insights to inform decision-making and drive continuous improvement.
Physical Security Checklists:
Utilize comprehensive checklists to ensure thoroughness and consistency in your physical security practices. From routine inspections to emergency response protocols, empower your teams with structured guidelines to follow and reference.
Physical Security Management Case Study:
Explore real-world examples of successful physical security management strategies in action. Learn from the experiences of organizations that have faced security challenges and overcome them through proactive planning, collaboration, and innovation.
In conclusion, the Complete Physical Security Management Business Toolkit is your comprehensive guide to strengthening your organization's security posture and mitigating risks effectively. Empower your teams with the knowledge, strategies, and tools they need to safeguard your assets, protect your people, and ensure business continuity in an increasingly complex threat landscape. Invest in physical security today and safeguard your future success.
Key Words:
Strategy & Transformation, Growth Strategy, Strategic Planning, Strategy Frameworks, Innovation Management, Pricing Strategy, Core Competencies, Strategy Development, Business Transformation, Marketing Plan Development, Product Strategy, Breakout Strategy, Competitive Advantage, Mission, Vision, Values, Strategy Deployment & Execution, Innovation, Vision Statement, Core Competencies Analysis, Corporate Strategy, Product Launch Strategy, BMI, Blue Ocean Strategy, Breakthrough Strategy, Business Model Innovation, Business Strategy Example, Corporate Transformation, Critical Success Factors, Customer Segmentation, Customer Value Proposition, Distinctive Capabilities, Enterprise Performance Management, KPI, Key Performance Indicators, Market Analysis, Market Entry Example, Market Entry Plan, Market Intelligence, Market Research, Market Segmentation, Market Sizing, Marketing, Michael Porter's Value Chain, Organizational Transformation, Performance Management, Performance Measurement, Platform Strategy, Product Go-to-Market Strategy, Reorganization, Restructuring, SWOT, SWOT Analysis, Service 4.0, Service Strategy, Service Transformation, Strategic Analysis, Strategic Plan Example, Strategy Deployment, Strategy Execution, Strategy Frameworks Compilation, Strategy Methodologies, Strategy Report Example, Value Chain, Value Chain Analysis, Value Innovation, Value Proposition, Vision Statement, Corporate Strategy, Business Development
NOTE:Our digital products are sold on an "as is" basis, making returns and refunds unavailable post-download. Please preview and inquire before purchasing. Please contact us before purchasing if you have any questions! This policy aligns with the standard Flevy Terms of Usage.
Got a question about the product? Email us at support@flevy.com or ask the author directly by using the "Ask the Author a Question" form. If you cannot view the preview above this document description, go here to view the large preview instead.
Source: Best Practices in Risk Management PowerPoint Slides: Physical Security Management PowerPoint (PPTX) Presentation Slide Deck, SB Consulting