Complete Guide to DBA Practices & Procedures - Database Security - Part 14 (PowerPoint PPTX Slide Deck)
PowerPoint (PPTX) 55 Slides
PPT DESCRIPTION
Part 14 of a multi-part series of presentations on the management discipline of database administration. This section covers the range of activities and practices for securing your databases and data. The entire series can be used to implement an efficient and effective database administration function at your organization. This part covers the following areas:
• Data Breaches
• Database Security Basics
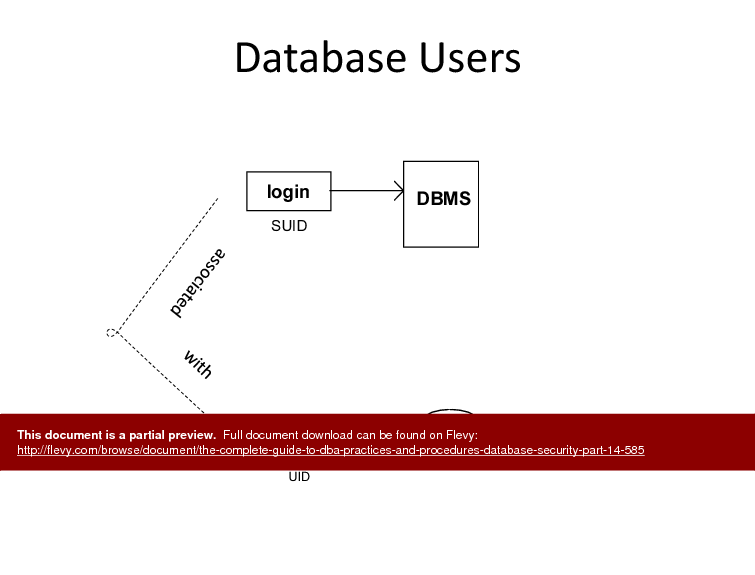
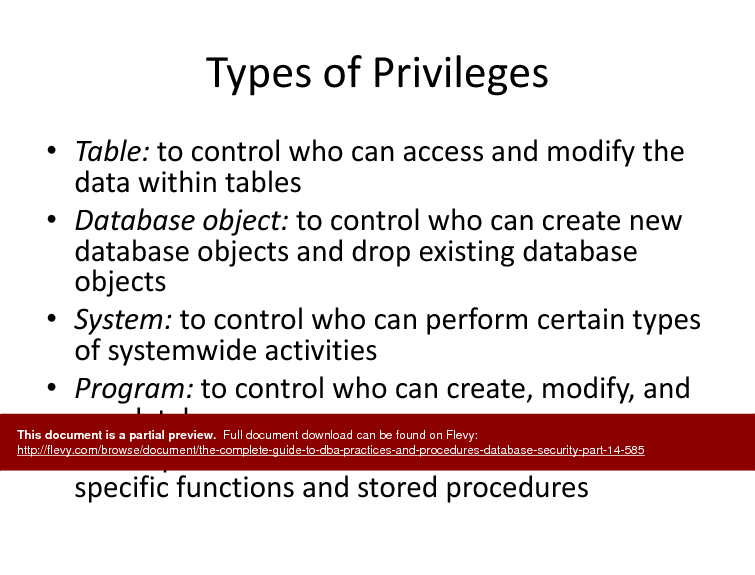
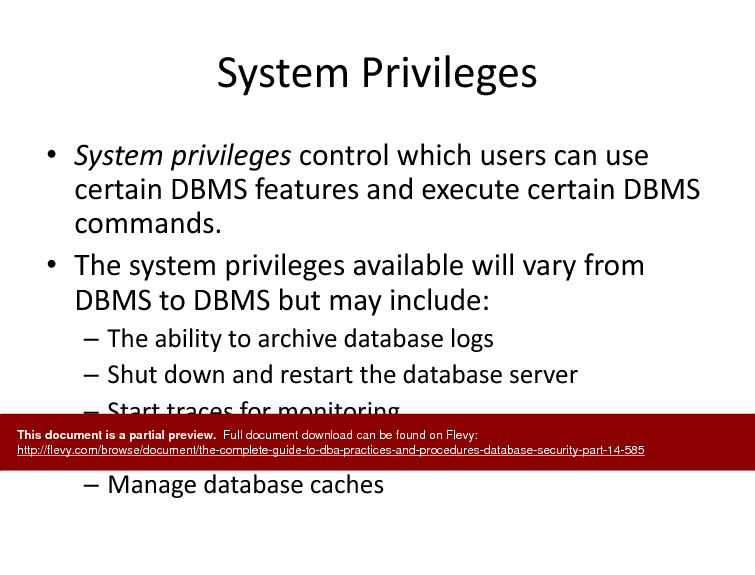
• Granting & Revoking Authority
• Authorization Roles & Groups
• Other Database Security Mechanisms
• Encryption
• SQL Injections Attacks
• Auditing
• External Security
• DBMS Fixpacks & Maintenance
Got a question about the product? Email us at support@flevy.com or ask the author directly by using the "Ask the Author a Question" form. If you cannot view the preview above this document description, go here to view the large preview instead.
Source: Complete Guide to DBA Practices & Procedures - Database Security - Part 14 PowerPoint (PPTX) Presentation Slide Deck, CSMullins