Assessment Dashboard - Cloud Security and Risk Standards (Excel XLSX)
BUY WITH CONFIDENCE
BENEFITS OF DOCUMENT
- Diagnose Cloud Security and Risk Standards projects, initiatives, organizations, businesses and processes using accepted diagnostic standards and practices.
- Implement evidence-based best practice strategies aligned with overall goals.
- Integrate recent advances in Cloud Security and Risk Standards and process design strategies into practice according to best practice guidelines.
DESCRIPTION
This product (Assessment Dashboard - Cloud Security and Risk Standards) is an Excel template (XLSX) with a supplemental Zip archive file document, which you can download immediately upon purchase.
This Cloud Security and Risk Standards Self Assessment helps you diagnose and address the following issues and questions:
IDS/IPS traffic pattern analysis can often detect or block attacks such as a denial-of-service attack or a network scan. However, in some cases this is legitimate traffic (such as using cloud infrastructure for load testing or security testing). Does the cloud provider have a documented exception process for allowing legitimate traffic that the IDS/IPS flags as an attack pattern?
It is clear that the CSP will face a large number of requests from its customers to prove that the CSP is secure and reliable. There a number of audit and compliance considerations for both the CSP and the customer to consider in cloud computing. First, which compliance framework should a CSP adopt to satisfy its customers and manage its own risks?
In addition to the security of your own customer data, customers should also be concerned about what data the provider collects and how the CSP protects that data. Specifically with regard to your customer data, what metadata does the provider have about your data, how is it secured, and what access do you, the customer, have to that metadata?
IDS/IPS content matching can detect or block known malware attacks, virus signatures, and spam signatures, but are also subject to false positives. If the cloud provider provides IDS/IPS services, is there a documented exception process for allowing legitimate traffic that has content similar to malware attacks or spam?
Security and authentication technologies, allied to event logging, in the cloud computing environment can help auditors as they deal with issues related to workflow were those who entered, approved, changed or otherwise touched data authorized to do so, on an individual, group or role-related basis?
As a CSP undertakes to build out or take a fresh look at its service offerings, the CSP should clearly define its business strategy and related risk management philosophy. What market segments or industries does the CSP intend to serve?
How do you know that a breach has occurred, how do you ensure that the CSP notifies you when a breach occurs, and who is responsible for managing the breach notification process (and costs associated with the process)?
An extra consideration when using cloud services concerns the handling of encryption keys – where are the keys stored and how are they made available to application code that needs to decrypt the data for processing?
Another critical success factor is that appropriate governance needs to be in place. That is, is an appropriate organizational structure in place to manage the organization facing the cloud computing solution?
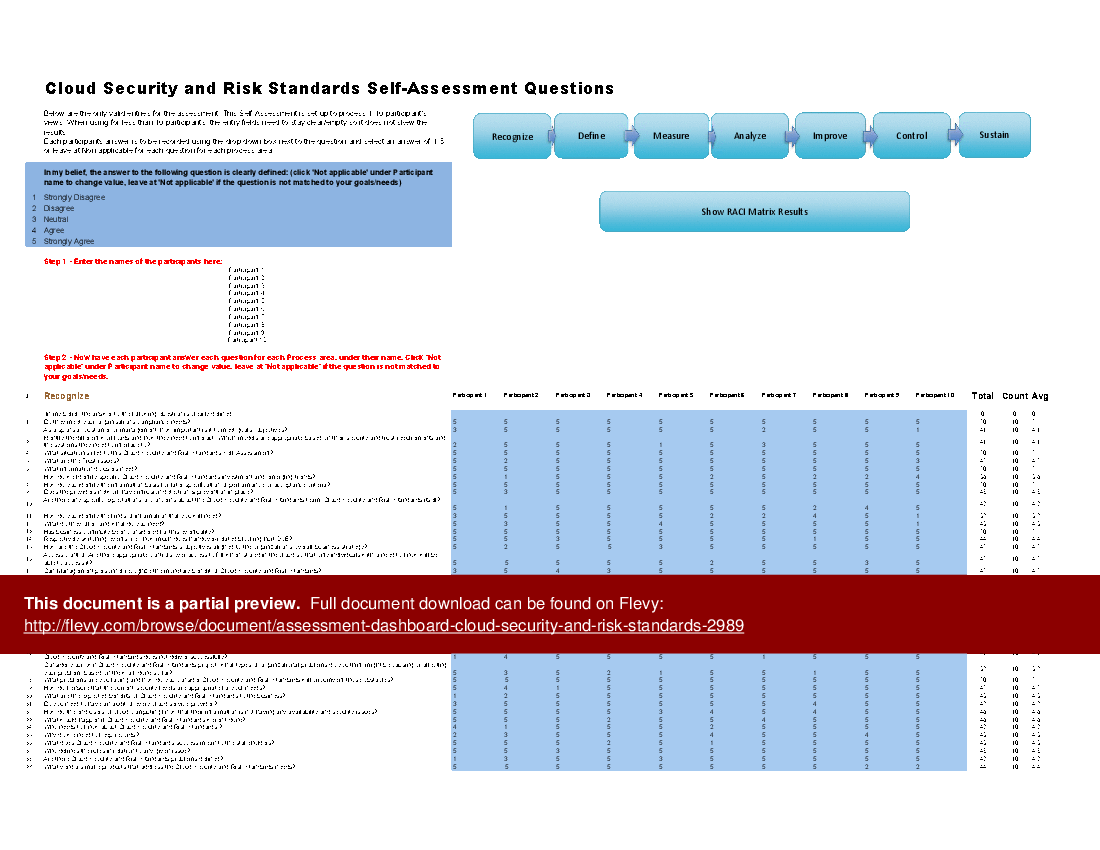
The Self Assessment tool is built in MS Excel. The above preview showcases an example of a completed version. The secondary document includes a blank template, as well as a detailed 140+ page PDF guide. The guide provides a convenient way to distribute and share among the participants to prepare and discuss the Self Assessment.
Got a question about the product? Email us at support@flevy.com or ask the author directly by using the "Ask the Author a Question" form. If you cannot view the preview above this document description, go here to view the large preview instead.
Source: Best Practices in Cloud Excel: Assessment Dashboard - Cloud Security and Risk Standards Excel (XLSX) Spreadsheet, Gerard Blokdijk
OVERVIEW
![]() (XLSX)
(XLSX)![]() (ZIP)
(ZIP)
Gerard is the CEO at The Art of Service. He has been providing information technology insights, talks, tools and products to organizations in a wide range of industries for over 25 years. Gerard is a widely recognized and respected information expert. Gerard founded The Art of Service consulting business in 2000. Gerard has authored numerous published books to date.
Ask the Author a Question
Cloud Digital Transformation Business Resilience Internet of Things Audit Management Supply Chain Resilience Supply Chain Analysis Bitcoin Blockchain Scrum Configuration Management Governance Center of Excellence Kanban Kanban Board SaaS